Use your vulnerability management dashboard in Microsoft Defender for Business
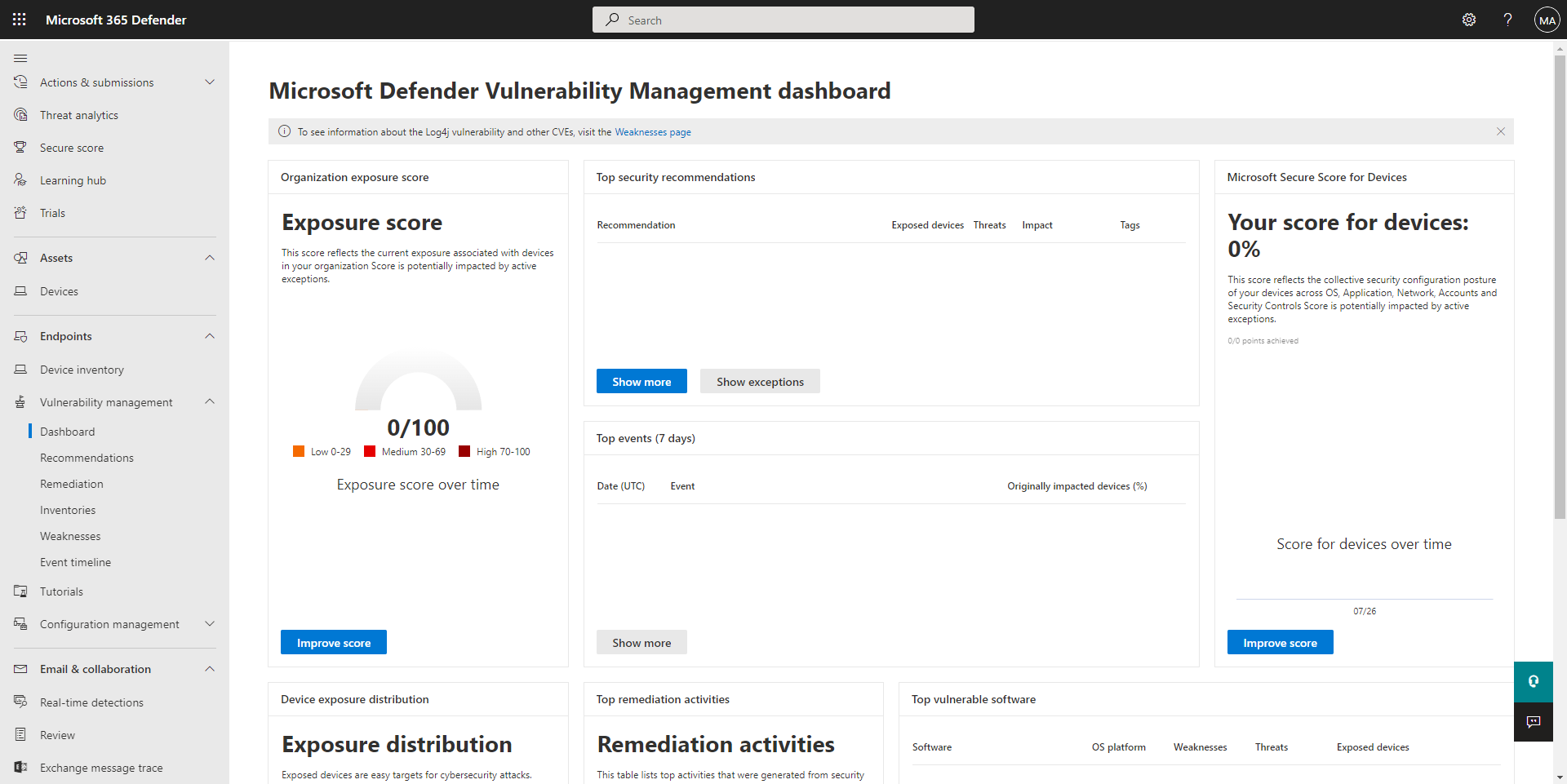
Defender for Business includes a vulnerability management dashboard that is designed to save your security team time and effort. In addition to providing an exposure score, that dashboard enables you to view information about exposed devices and see relevant security recommendations. You can use your Defender Vulnerability Management dashboard to:
- View your exposure score, which is associated with devices in your company.
- View your top security recommendations, such as addressing impaired communications with devices, turning on firewall protection, or updating Microsoft Defender Antivirus definitions.
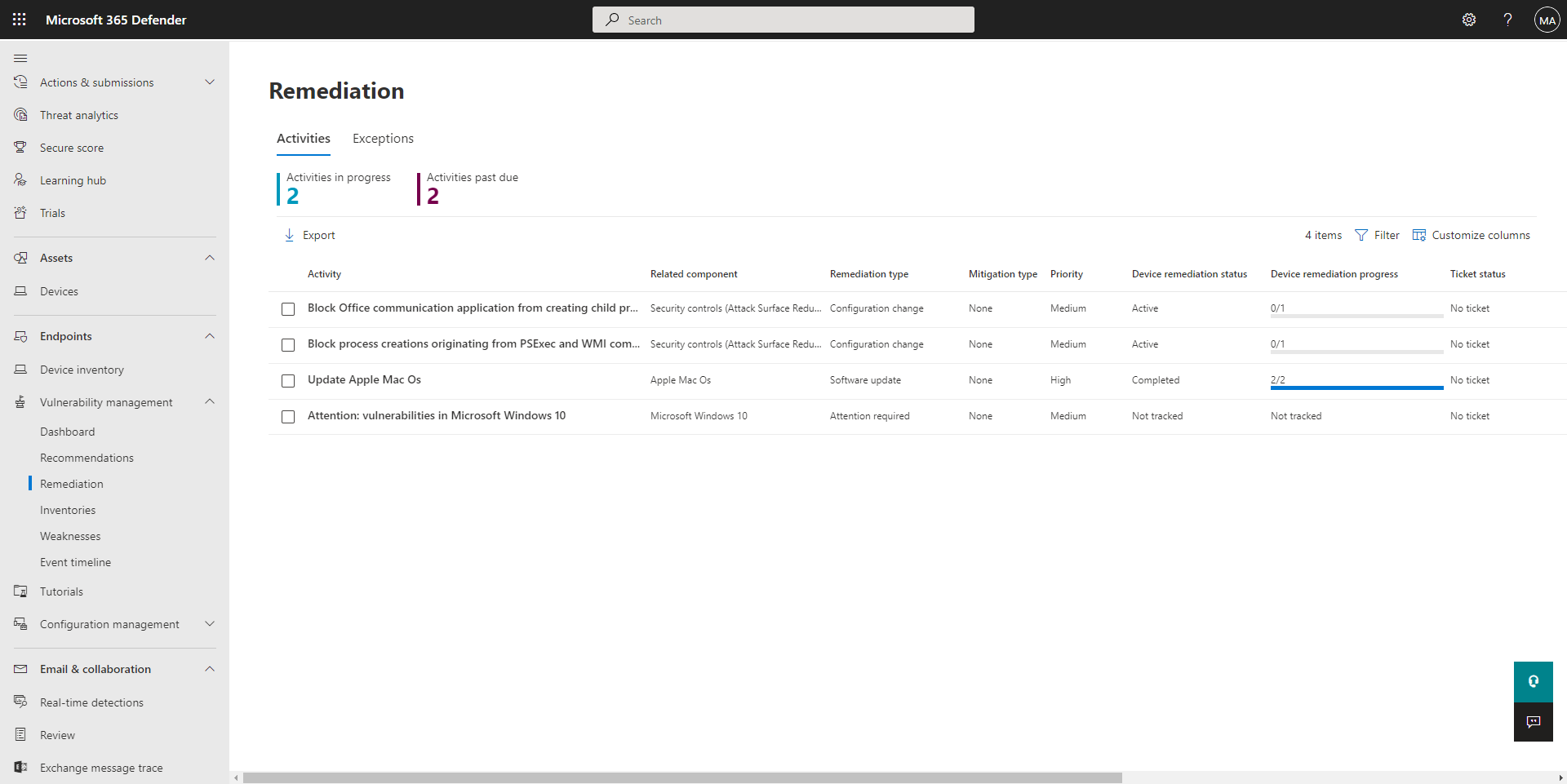
- View remediation activities, such as any files that were sent to quarantine, or vulnerabilities found on devices.
Vulnerability management features and capabilities
Vulnerability management features and capabilities in Microsoft Defender for Business include:
Dashboard: Provides information about vulnerabilities, exposure, and recommendations. You can see recent remediation activities, exposed devices, and ways to improve your company's overall security. Each card in the dashboard includes a link to more detailed information or to a page where you can take a recommended action.
Recommendations: Lists current security recommendations and related threat information to review and consider. When you select an item in the list, a flyout panel opens with more details about threats and actions you can take.
Remediation: Lists any remediation actions and their status. Remediation activities can include sending a file to quarantine, stopping a process from running, and blocking a detected threat from running. Remediation activities can also include updating a device, running an antivirus scan, and more.
Inventories: Lists software and apps currently in use in your organization. You'll see browsers, operating systems, and other software on devices, along with identified weaknesses and threats.
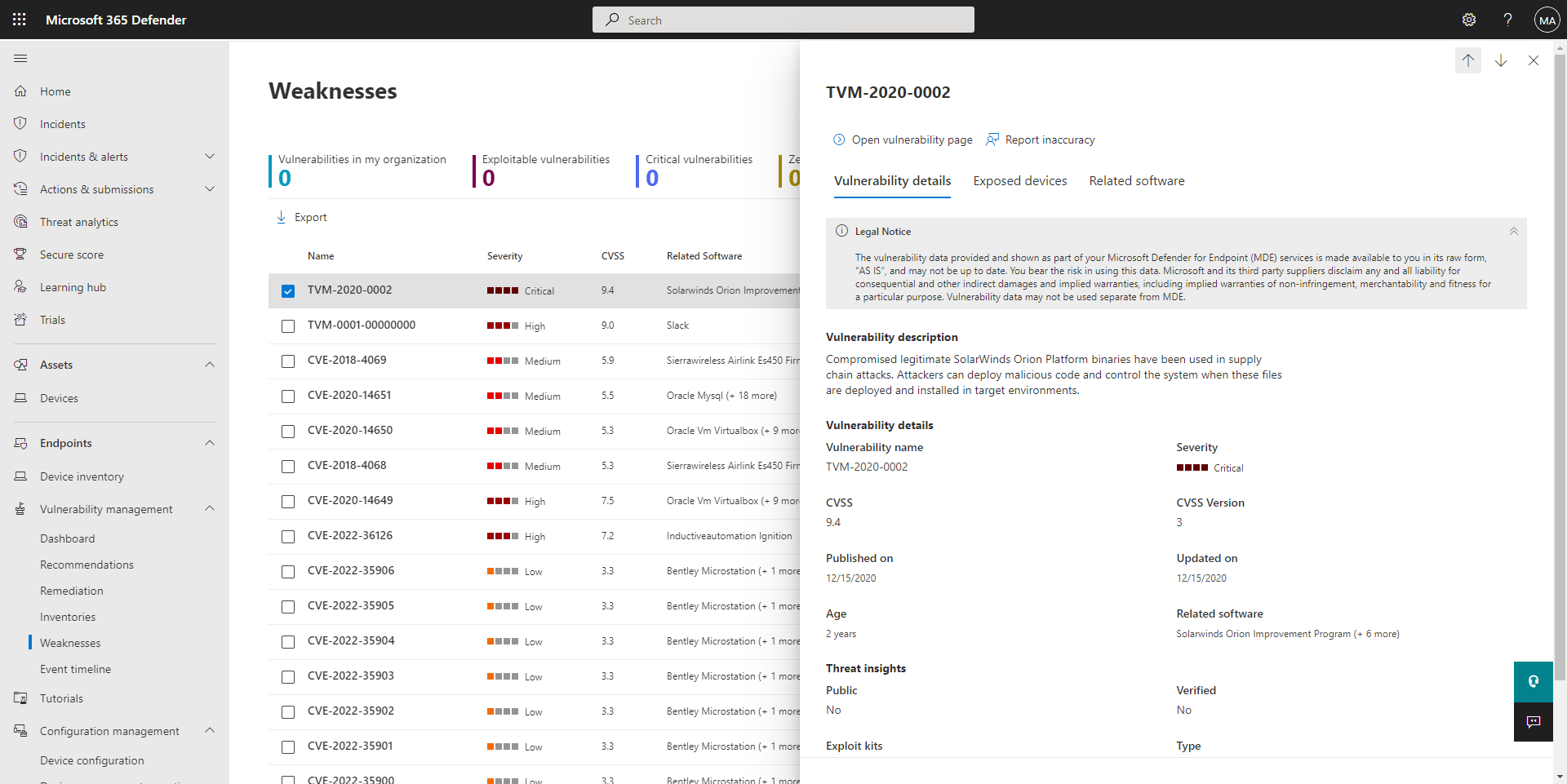
Weaknesses: Lists vulnerabilities along with the number of exposed devices in your organization. If you see "0" in the Exposed devices column, you do not have to take any immediate action. However, you can learn more about each vulnerability listed on this page. Select an item to learn more about it and what you can do to mitigate the potential threat to your company.
Event timeline: Lists vulnerabilities that affect your organization in a timeline view.
Learn more about Microsoft Defender Vulnerability Management.