How Defender for Cloud Apps helps protect your Asana environment
Asana is a cloud-based project management tool that enables your users to collaborate on projects and tasks across your organization and partners in a streamlined and efficient way. Asana holds critical data of your organization, and this makes it a target for malicious actors.
Connecting Asana to Defender for Cloud Apps gives you improved insights into your users' activities and provides threat detection using machine learning based anomaly detections.
Main threats include:
- Compromised accounts and insider threats
- Data leakage
- Insufficient security awareness
- Unmanaged bring your own device (BYOD)
Control Asana with policies
| Type | Name |
|---|---|
| Built-in anomaly detection policy | Activity from anonymous IP addresses Activity from infrequent country Activity from suspicious IP addresses Impossible travel Activity performed by terminated user (requires Microsoft Entra ID as IdP) Multiple failed login attempts |
| Activity policy | Built a customized policy by using the Asana Audit Log activities |
For more information about creating policies, see Create a policy.
Automate governance controls
In addition to monitoring for potential threats, you can apply and automate the following Asana governance actions to remediate detected threats:
| Type | Action |
|---|---|
| User governance | Notify user on alert (via Microsoft Entra ID) Require user to sign in again (via Microsoft Entra ID) Suspend user (via Microsoft Entra ID) |
For more information about remediating threats from apps, see Governing connected apps.
Connect Asana to Defender for Cloud Apps
This sections describes how to connect Microsoft Defender for Cloud Apps to your existing Asana account using the App Connector APIs. This connection gives you visibility into and control over your organization's Asana use.
Prerequisites:
- An Asana enterprise account is a pre-requisite for this connection. You must be signed-in as an admin to Asana.
To connect Asana:
Sign into Asana portal with an admin account.
Navigate to Admin Console>Apps>Service accounts and click on your service account. If you don’t have a Service account, create one using the guidance provided here.
Copy the service account Token. You may have to Reset and generate new token to copy the token if you have an existing service account.
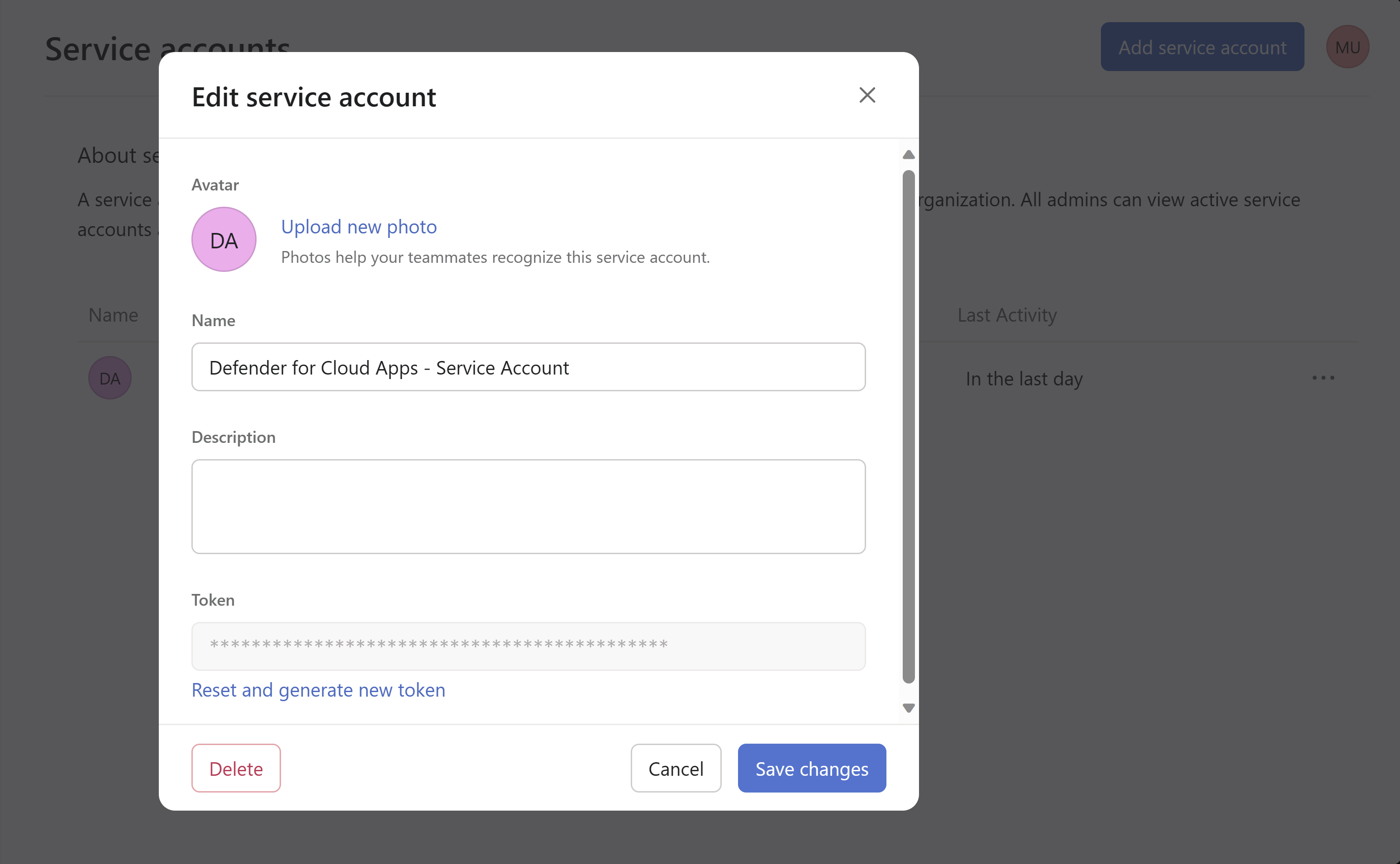
Copy the workspace ID from the URL and save it for future reference.
In the Microsoft Defender portal, navigate to Settings>Cloud Apps>Connected apps>App Connectors.
Click on Connect an app and select Asana.
Provide an Instance name in the connection wizard and click on Next.
Enter the copied access token and workspace ID in API Key and workspace ID fields respectively. Once entered click on Submit.
Defender for Cloud Apps will start fetch Asana audit logs once connection is successfully established.
If you have any problems connecting the app, see Troubleshooting App Connectors.
Related content
Atsiliepimai
Jau greitai: 2024 m. palaipsniui atsisakysime „GitHub“ problemų, kaip turiniui taikomo atsiliepimų mechanizmo, ir pakeisime jį nauja atsiliepimų sistema. Daugiau informacijos žr. https://aka.ms/ContentUserFeedback.
Pateikti ir peržiūrėti atsiliepimą, skirtą