Approve or deny requests for Azure resource roles in Privileged Identity Management
Microsoft Entra Privileged Identity Management (PIM) enables you to configure roles so that they require approval for activation, and choose users or groups from your Microsoft Entra organization as delegated approvers. We recommend selecting two or more approvers for each role to reduce workload for the Privileged Role Administrator. Delegated approvers have 24 hours to approve requests. If a request isn't approved within 24 hours, then the eligible user must re-submit a new request. The 24 hour approval time window isn't configurable.
Follow the steps in this article to approve or deny requests for Azure resource roles.
View pending requests
As a delegated approver, you receive an email notification when an Azure resource role request is pending your approval. You can view these pending requests in Privileged Identity Management.
Sign in to the Microsoft Entra admin center as at least a Privileged Role Administrator.
Browse to Identity governance > Privileged Identity Management > Approve requests.
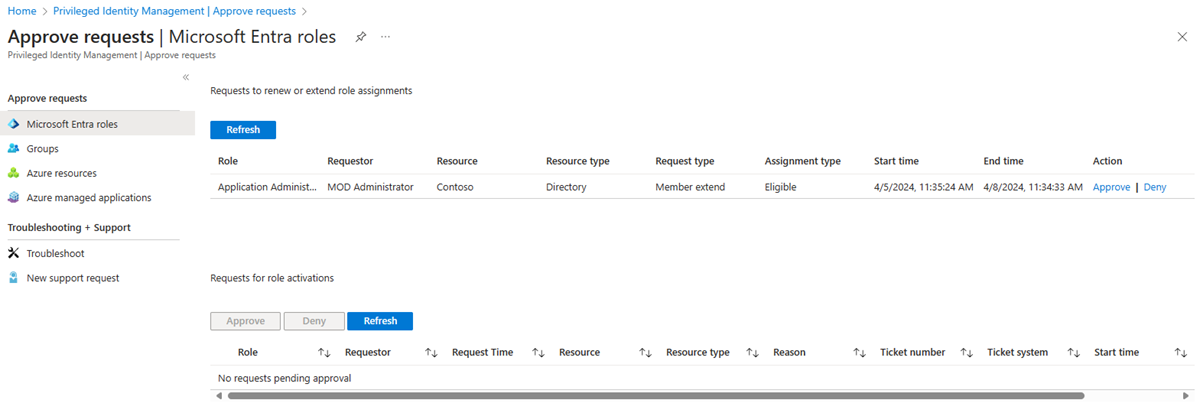
In the Requests for role activations section, you see a list of requests pending your approval.
Approve requests
- Find and select the request that you want to approve. An approve or deny page appears.
- In the Justification box, enter the business justification.
- Select Approve. You will receive an Azure notification of your approval.
Approve pending requests using Microsoft ARM API
Note
Approval for extend and renew requests is currently not supported by the Microsoft ARM API
Get IDs for the steps that require approval
To get the details of any stage of a role assignment approval, you can use Role Assignment Approval Step - Get By ID REST API.
HTTP request
GET https://management.azure.com/providers/Microsoft.Authorization/roleAssignmentApprovals/{approvalId}/stages/{stageId}?api-version=2021-01-01-preview
Approve the activation request step
HTTP request
PATCH
PATCH https://management.azure.com/providers/Microsoft.Authorization/roleAssignmentApprovals/{approvalId}/stages/{stageId}?api-version=2021-01-01-preview
{
"reviewResult": "Approve", // or "Deny"
"justification": "Trusted User"
}
HTTP response
Successful PATCH calls generate an empty response.
For more information, see Use Role Assignment Approvals to approve PIM role activation requests with REST API
Deny requests
- Find and select the request that you want to approve. An approve or deny page appears.
- In the Justification box, enter the business justification.
- Select Deny. A notification appears with your denial.
Workflow notifications
Here's some information about workflow notifications:
- Approvers are notified by email when a request for a role is pending their review. Email notifications include a direct link to the request, where the approver can approve or deny.
- Requests are resolved by the first approver who approves or denies.
- When an approver responds to the request, all approvers are notified of the action.
- Resource administrators are notified when an approved user becomes active in their role.
Note
A resource administrator who believes that an approved user should not be active can remove the active role assignment in Privileged Identity Management. Although resource administrators are not notified of pending requests unless they are an approver, they can view and cancel pending requests for all users by viewing pending requests in Privileged Identity Management.