Microsoft Defender XDR integration with Microsoft Sentinel
Applies to:
- Microsoft Defender XDR
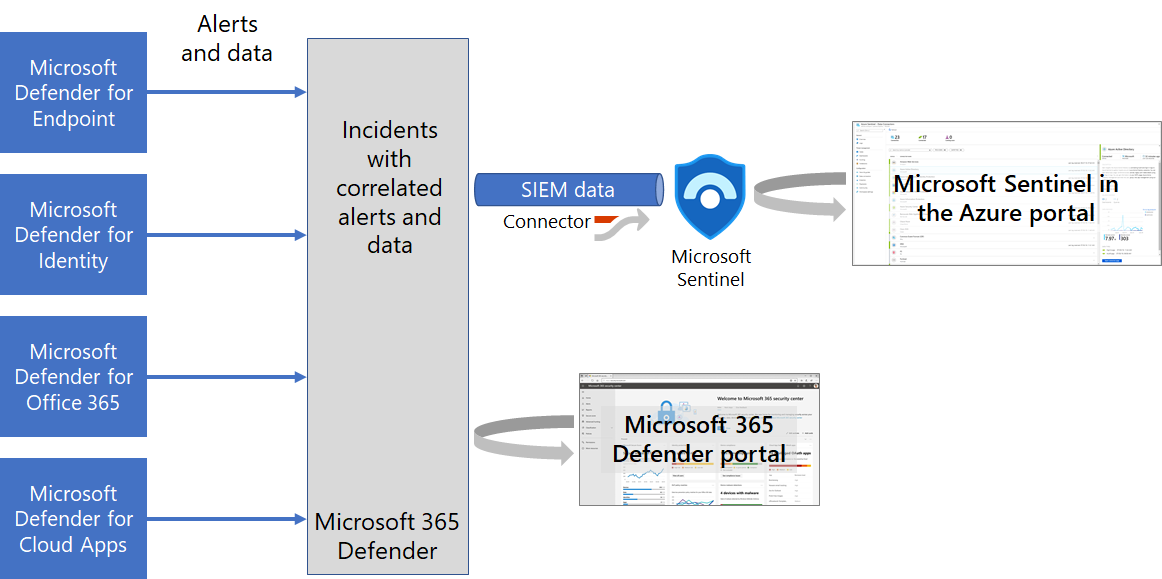
The Microsoft Defender XDR connector for Microsoft Sentinel sends all Microsoft Defender XDR incidents and alerts information to Microsoft Sentinel and keeps the incidents synchronized.
Once you add the connector, Microsoft Defender XDR incidents—which include all associated alerts, entities, and relevant information received from Microsoft Defender for Endpoint, Microsoft Defender for Identity, Microsoft Defender for Office 365, and Microsoft Defender for Cloud Apps—are streamed to Microsoft Sentinel as security information and event management (SIEM) data, providing you with context to perform triage and incident response with Microsoft Sentinel.
Once in Microsoft Sentinel, incidents remain bi-directionally synchronized with Microsoft Defender XDR, allowing you to take advantage of the benefits of both the Microsoft Defender portal and Microsoft Sentinel in the Azure portal for incident investigation and response.
Watch this short overview of Microsoft Sentinel integration with Microsoft Defender XDR (4 minutes).
Here's how it works.
Next steps
- Get a deeper understanding of Microsoft Defender XDR integration with Microsoft Sentinel.
- Connect data from Microsoft Defender XDR to Microsoft Sentinel.
See also
Tip
Do you want to learn more? Engage with the Microsoft Security community in our Tech Community: Microsoft Defender XDR Tech Community.