Summarize an incident with Microsoft Copilot in Microsoft Defender
Microsoft Defender XDR applies the capabilities of Copilot for Security to summarize incidents, delivering impactful information and insights to simplify investigation tasks. Attack investigation is a crucial step for incident response teams to successfully defend an organization against further damage from a cyber threat. Investigations can often be time-consuming as it involves numerous steps. Incident response teams need to understand how the attack happened: sort through numerous alerts, identify which assets and entities are involved, and assess the scope and impact of an attack.
This guide outlines what to expect and how to access the summarizing capability of Copilot in Defender, including information on providing feedback.
Know before you begin
If you're new to Copilot for Security, you should familiarize yourself with it by reading the following articles:
- What is Copilot for Security?
- Copilot for Security experiences
- Get started with Copilot for Security
- Understand authentication in Copilot for Security
- Prompting in Copilot for Security
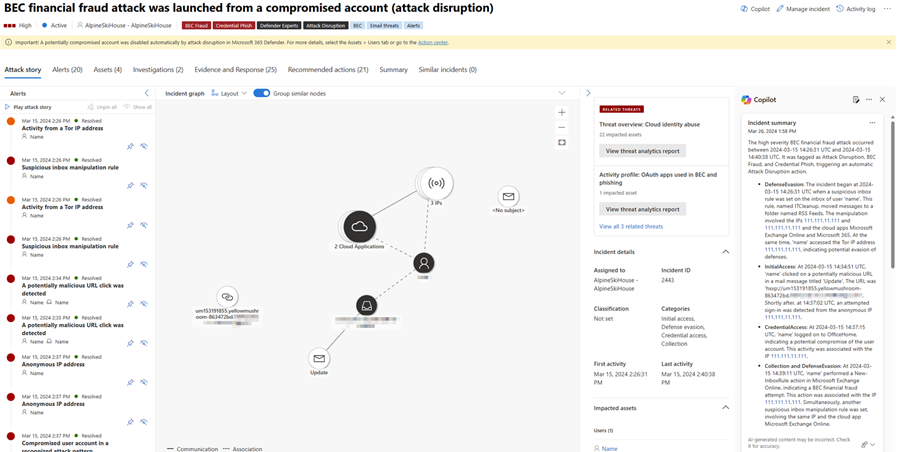
Incident responders can easily gain the right context to investigate and remediate incidents through Defender XDR's correlation capabilities and Copilot for Security's AI-powered data processing and contextualization. With an incident summary, responders can quickly get important information to help in their investigation.
Copilot for Security integration in Microsoft Defender
The incident summary capability is available in the Microsoft Defender portal for customers who have provisioned access to Copilot for Security.
This capability is also available in the Copilot for Security standalone experience through the Microsoft Defender XDR plugin. Know more about preinstalled plugins in Copilot for Security.
Key features
Incidents containing up to 100 alerts can be summarized into one incident summary. An incident summary, depending on the availability of the data, includes the following:
- The time and date when an attack started.
- The entity or asset where the attack started.
- A summary of timelines of how the attack unfolded.
- The assets involved in the attack.
- Indicators of compromise (IoCs).
- Names of threat actors involved.
To summarize an incident, perform the following steps:
Open an incident page. Copilot automatically creates an incident summary upon opening the page. You can stop the summary creation by selecting Cancel or restart creation by selecting Regenerate.
The incident summary card loads on the Copilot pane. Review the generated summary on the card.
Tip
You can navigate to a file, IP, or URL page from the Copilot results pane by clicking on the evidence in the results.
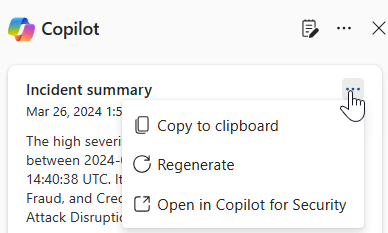
Select the More actions ellipsis (...) at the top of the incident summary card to copy or regenerate the summary, or view the summary in the Copilot for Security portal. Selecting Open in Copilot for Security opens a new tab to the Copilot for Security standalone portal where you can input prompts and access other plugins.
Review the summary and use the information to guide your investigation and response to the incident.
Sample incident summary prompt
In the Copilot for Security standalone portal, you can use the following prompt to generate incident summaries:
- Provide a summary for Defender incident {incident ID}.
Tip
When generating an incident summary in the Copilot for Security portal, Microsoft recommends including the word Defender in your prompts to ensure that the incident summary capability delivers the results.
Provide feedback
Microsoft highly encourages you to provide feedback to Copilot, as it’s crucial for a capability’s continuous improvement. You can provide feedback on the summary by selecting the feedback icon  found on the bottom of the Copilot pane.
found on the bottom of the Copilot pane.
See also
- Learn about other Copilot for Security embedded experiences
- Privacy and data security in Copilot for Security
Tip
Do you want to learn more? Engage with the Microsoft Security community in our Tech Community: Microsoft Defender XDR Tech Community.