Tutorial: Peer on-premises environments to Azure VMware Solution
After you deploy your Azure VMware Solution private cloud, connect it to your on-premises environment. ExpressRoute Global Reach connects your on-premises environment to your Azure VMware Solution private cloud. The ExpressRoute Global Reach connection is established between the private cloud ExpressRoute circuit and an existing ExpressRoute connection to your on-premises environments.
Note
You can connect through VPN, but that's out of scope for this quick start guide.
In this article, you'll:
- Create an ExpressRoute auth key in the on-premises ExpressRoute circuit
- Peer the private cloud with your on-premises ExpressRoute circuit
- Verify on-premises network connectivity
Once you completed this section, follow the next steps provided at the end of this tutorial.
Prerequisites
Review the documentation on how to enable connectivity in different Azure subscriptions.
A separate, functioning ExpressRoute circuit for connecting on-premises environments to Azure, which is circuit 1 for peering.
Ensure that all gateways, including the ExpressRoute provider's service, support 4-byte Autonomous System Number (ASN). Azure VMware Solution uses 4-byte public ASNs for advertising routes.
Note
If advertising a default route to Azure (0.0.0.0/0), ensure a more specific route containing your on-premises networks is advertised in addition to the default route to enable management access to Azure VMware Solution. A single 0.0.0.0/0 route will be discarded by Azure VMware Solution's management network to ensure successful operation of the service.
Create an ExpressRoute auth key in the on-premises ExpressRoute circuit
The circuit owner creates an authorization, which creates an authorization key to be used by a circuit user to connect their virtual network gateways to the ExpressRoute circuit. An authorization is valid for only one connection.
Note
Each connection requires a separate authorization.
From ExpressRoute circuits in the left navigation, under Settings, select Authorizations.
Enter the name for the authorization key and select Save.
Once created, the new key appears in the list of authorization keys for the circuit.
Copy the authorization key and the ExpressRoute ID to use them in the next step to complete the peering.
Peer private cloud to on-premises
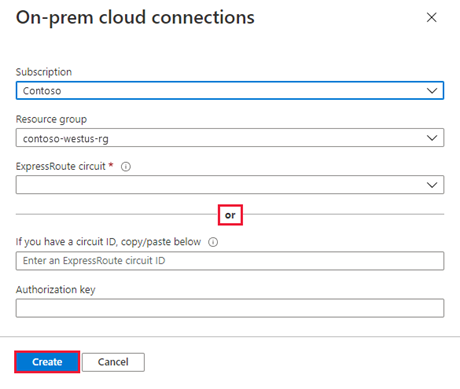
Now that you created an authorization key for the private cloud ExpressRoute circuit, you can peer it with your on-premises ExpressRoute circuit. The peering is done from the on-premises ExpressRoute circuit in the Azure portal. You use the resource ID (ExpressRoute circuit ID) and authorization key of your private cloud ExpressRoute circuit to finish the peering.
From the private cloud, under Manage, select Connectivity > ExpressRoute Global Reach > Add.
Enter the ExpressRoute ID and the authorization key created in the previous section.
Select Create. The new connection shows in the on-premises cloud connections list.
Verify on-premises network connectivity
In your on-premises edge router, you should now see where the ExpressRoute connects the NSX-T Data Center network segments and the Azure VMware Solution management segments.
Important
Everyone has a different environment, and some will need to allow these routes to propagate back into the on-premises network.
Next steps
Continue to the next tutorial to install VMware HCX add-on in your Azure VMware Solution private cloud.