Choose a traffic mirroring method for OT sensors
This article is one in a series of articles describing the deployment path for OT monitoring with Microsoft Defender for IoT, and describes the supported traffic mirroring methods for OT monitoring with Microsoft Defender for IoT.
The decision as to which traffic mirroring method to use depends on your network configuration and the needs of your organization.
To ensure that Defender for IoT only analyzes the traffic that you want to monitor, we recommend that you configure traffic mirroring on a switch or a terminal access point (TAP) that includes only industrial ICS and SCADA traffic.
Note
SPAN and RSPAN are Cisco terminology. Other brands of switches have similar functionality but might use different terminology.
Mirroring port scope recommendations
We recommend configuring your traffic mirroring from all of your switch's ports, even if no data is connected to them. If you don't, rogue devices can later be connected to an unmonitored port, and those devices won't be detected by the Defender for IoT network sensors.
For OT networks that use broadcast or multicast messaging, configure traffic mirroring only for RX (Receive) transmissions. Multicast messages will be repeated for any relevant active ports, and you'll be using more bandwidth unnecessarily.
Compare supported traffic mirroring methods
Defender for IoT supports the following methods:
| Method | Description | More information |
|---|---|---|
| A switch SPAN port | Mirrors local traffic from interfaces on the switch to a different interface on the same switch | Configure mirroring with a switch SPAN port |
| Remote SPAN (RSPAN) port | Mirrors traffic from multiple, distributed source ports into a dedicated remote VLAN | Remote SPAN (RSPAN) ports Configure traffic mirroring with a Remote SPAN (RSPAN) port |
| Active or passive aggregation (TAP) | Installs an active / passive aggregation TAP inline to your network cable, which duplicates traffic to the OT network sensor. Best method for forensic monitoring. | Active or passive aggregation (TAP) |
| An encapsulated remote switched port analyzer (ERSPAN) | Mirrors input interfaces to your OT sensor's monitoring interface | ERSPAN ports Update a sensor's monitoring interfaces (configure ERSPAN). |
| An ESXi vSwitch | Mirrors traffic using Promiscuous mode on an ESXi vSwitch. | Traffic mirroring with virtual switches Configure traffic mirroring with a ESXi vSwitch. |
| A Hyper-V vSwitch | Mirrors traffic using Promiscuous mode on a Hyper-V vSwitch. | Traffic mirroring with virtual switches Configure traffic mirroring with a Hyper-V vSwitch |
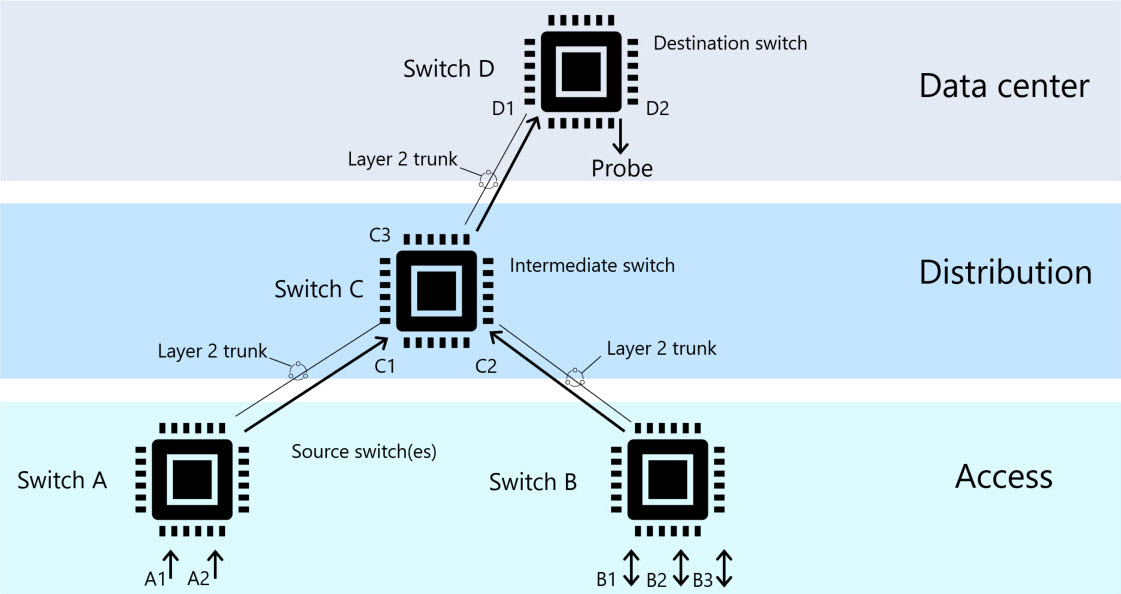
Remote SPAN (RSPAN) ports
Configure a remote SPAN (RSPAN) session on your switch to mirror traffic from multiple, distributed source ports into a dedicated remote VLAN.
Data in the VLAN is then delivered through trunked ports, across multiple switches to a specified switch that contains the physical destination port. Connect the destination port to your OT network sensor to monitor traffic with Defender for IoT.
The following diagram shows an example of a remote VLAN architecture:
For more information, see Configure traffic mirroring with a Remote SPAN (RSPAN) port.
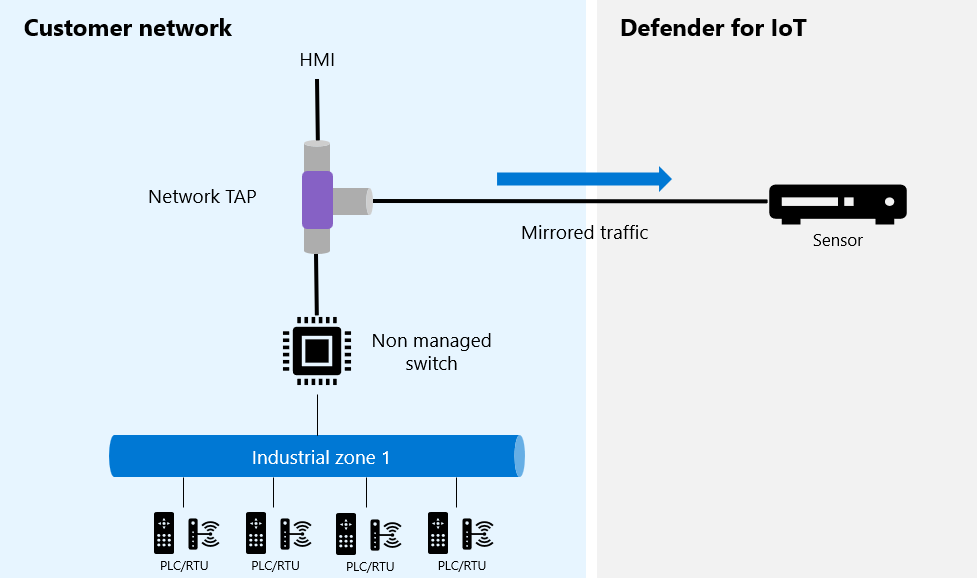
Active or passive aggregation (TAP)
When using active or passive aggregation to mirror traffic, an active or passive aggregation terminal access point (TAP) is installed inline to the network cable. The TAP duplicates both Receive and Transmit traffic to the OT network sensor so that you can monitor the traffic with Defender for IoT.
A TAP is a hardware device that allows network traffic to flow back and forth between ports without interruption. The TAP creates an exact copy of both sides of the traffic flow, continuously, without compromising network integrity.
For example:
Some TAPs aggregate both Receive and Transmit, depending on the switch configuration. If your switch doesn't support aggregation, each TAP uses two ports on your OT network sensor to monitor both Receive and Transmit traffic.
Advantages of mirroring traffic with a TAP
We recommend TAPs especially when traffic mirroring for forensic purposes. Advantages of mirroring traffic with TAPs include:
TAPs are hardware-based and can't be compromised
TAPs pass all traffic, even damaged messages that are often dropped by the switches
TAPs aren't processor-sensitive, which means that packet timing is exact. In contrast, switches handle mirroring functionality as a low-priority task, which can affect the timing of the mirrored packets.
You can also use a TAP aggregator to monitor your traffic ports. However, TAP aggregators aren't processor-based, and aren't as intrinsically secure as hardware TAPs. TAP aggregators may not reflect exact packet timing.
Common TAP models
The following TAP models have been tested for compatibility with Defender for IoT. Other vendors and models might also be compatible.
Garland P1GCCAS
When using a Garland TAP, make sure to set up your network to support aggregation. For more information, see the Tap Aggregation diagram under the Network Diagrams tab in the Garland installation guide.
IXIA TPA2-CU3
When using an Ixia TAP, make sure Aggregation mode is active. For more information, see the Ixia install guide.
US Robotics USR 4503
When using a US Robotics TAP, make sure to toggle the aggregation mode on by setting the selectable switch to AGG. For more information, see the US Robotics installation guide.
ERSPAN ports
Use an encapsulated remote switched port analyzer (ERSPAN) to mirror input interfaces over an IP network to your OT sensor's monitoring interface, when securing remote networks with Defender for IoT.
The sensor's monitoring interface is a promiscuous interface and doesn't have a specifically allocated IP address. When ERSPAN support is configured, traffic payloads that are ERSPAN encapsulated with GRE tunnel encapsulation will be analyzed by the sensor.
Use ERSPAN encapsulation when there's a need to extend monitored traffic across Layer 3 domains. ERSPAN is a Cisco proprietary feature and is available only on specific routers and switches. For more information, see the Cisco documentation.
Note
This article provides high-level guidance for configuring traffic mirroring with ERSPAN. Specific implementation details will vary depending on your equiptment vendor.
ERSPAN architecture
ERSPAN sessions include a source session and a destination session configured on different switches. Between the source and destination switches, traffic is encapsulated in GRE, and can be routed over layer 3 networks.
For example:
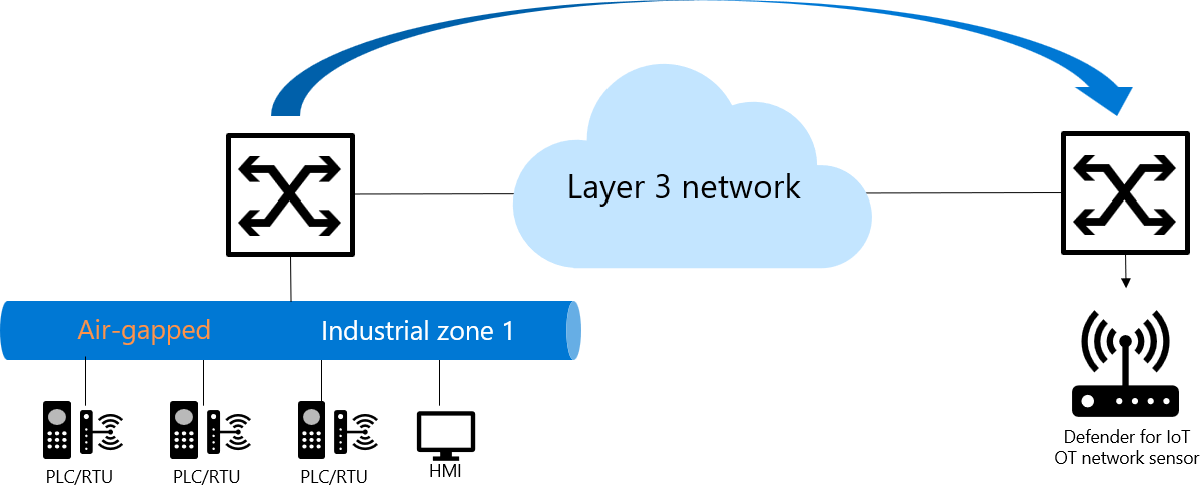
ERSPAN transports mirrored traffic over an IP network using the following process:
- A source router encapsulates the traffic and sends the packet over the network.
- At the destination router, the packet is de-capsulated and sent to the destination interface.
ERSPAN source options include elements such as:
- Ethernet ports and port channels
- VLANs; all supported interfaces in the VLAN are ERSPAN sources
- Fabric port channels
- Satellite ports and host interface port channels
For more information, see Update a sensor's monitoring interfaces (configure ERSPAN).
Traffic mirroring with virtual switches
While a virtual switch doesn't have mirroring capabilities, you can use Promiscuous mode in a virtual switch environment as a workaround for configuring a monitoring port, similar to a SPAN port. A SPAN port on your switch mirrors local traffic from interfaces on the switch to a different interface on the same switch.
Connect the destination switch to your OT network sensor to monitor traffic with Defender for IoT.
Promiscuous mode is a mode of operation and a security, monitoring, and administration technique that is defined at the virtual switch or portgroup level. When promiscuous mode is used, any of the virtual machine’s network interfaces in the same portgroup can view all network traffic that goes through that virtual switch. By default, promiscuous mode is turned off.
For more information, see: