Integrate LogRhythm with Microsoft Defender for IoT
This article describes how to send Microsoft Defender for IoT alerts to LogRhythm. Integrating Defender for IoT with LogRhythm provides visibility into the security and resiliency of OT networks and a unified approach to IT and OT security.
Prerequisites
Before you begin, make sure that you have the following prerequisites:
- Access to a Defender for IoT OT sensor as an Admin user. For more information, see On-premises users and roles for OT monitoring with Defender for IoT.
Create a Defender for IoT forwarding rule
This procedure describes how to create a forwarding rule from your OT sensor to send Defender for IoT alerts from that sensor to LogRhythm.
Forwarding alert rules run only on alerts triggered after the forwarding rule is created. Alerts already in the system from before the forwarding rule was created aren't affected by the rule.
For more information, see Forward alert information.
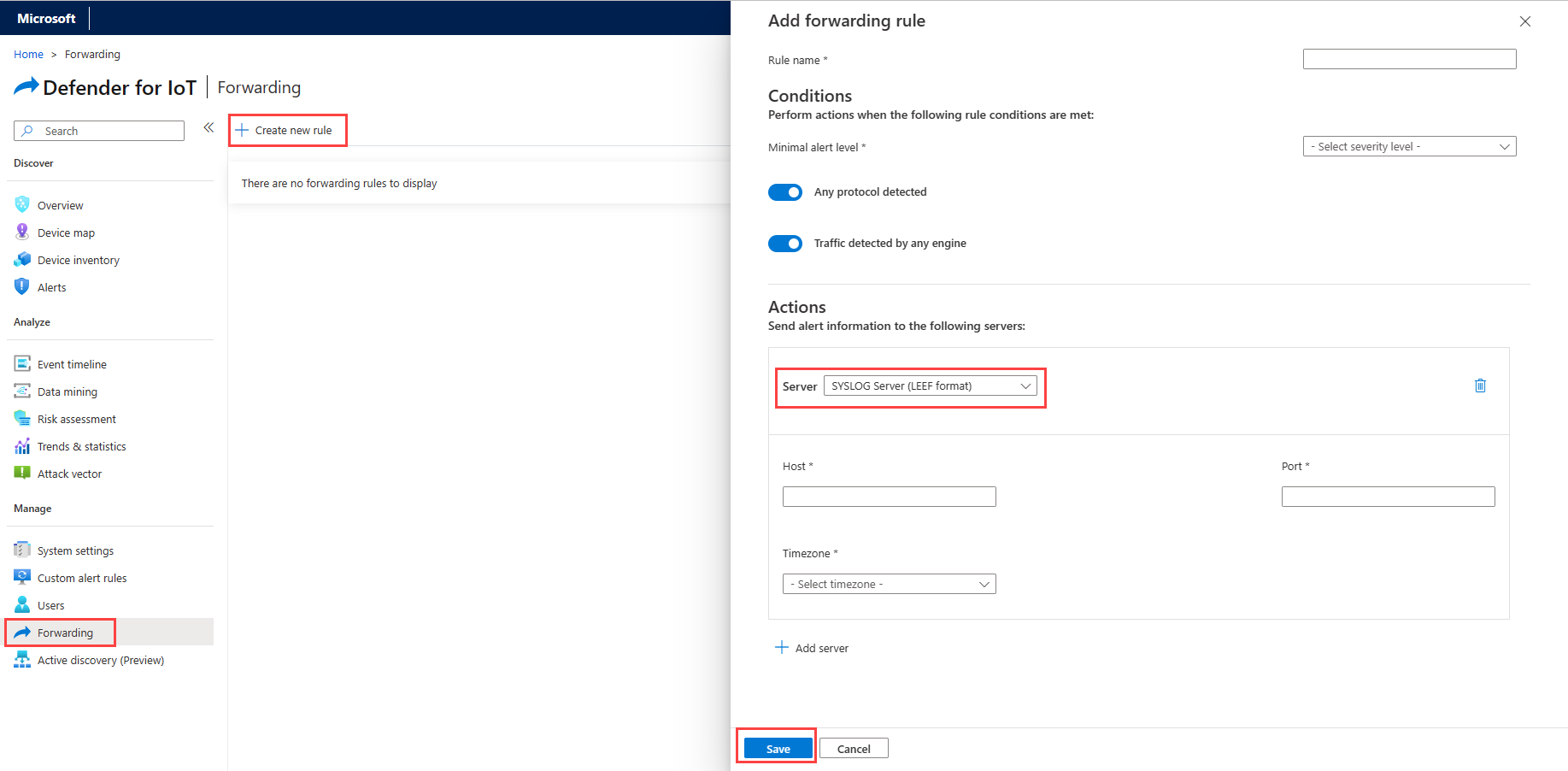
Sign in to your OT sensor console and select Forwarding.
Select + Create new rule.
In the Add forwarding rule pane, define the rule parameters:
Parameter Description Rule name Enter a meaningful name for your rule. Minimal alert level The minimal security level incident to forward. For example, if you select Minor, you're notified about all minor, major and critical incidents. Any protocol detected Toggle off to select the protocols you want to include in the rule. Traffic detected by any engine Toggle off to select the traffic you want to include in the rule. In the Actions area, define the following values:
Parameter Description Server Select a SYSLOG server option, such as SYSLOG Server (LEEF format). Host The IP or hostname of your LogRhythm collector Port Enter 514. Timezone Enter your timezone. Select Save.
Configure LogRhythm to collect logs
After configuring a forwarding rule from your OT sensor console, configure LogRhythm to collect your Defender for IoT logs.
For more information, see the LogRhythm documentation.