What's new in Microsoft Sentinel
This article lists recent features added for Microsoft Sentinel, and new features in related services that provide an enhanced user experience in Microsoft Sentinel. For new features in Microsoft's unified security operations (SecOps) platform, see the unified SecOps platform documentation.
The listed features were released in the last three months. For information about earlier features delivered, see our Tech Community blogs.
Get notified when this page is updated by copying and pasting the following URL into your feed reader:
https://aka.ms/sentinel/rss
Note
For information about feature availability in US Government clouds, see the Microsoft Sentinel tables in Cloud feature availability for US Government customers.
January 2025
- Optimize threat intelligence feeds with ingestion rules
- Matching analytics rule now generally available (GA)
- Threat intelligence management interface updated
- Unlock advanced hunting with new STIX objects by opting in to new threat intelligence tables
- Threat intelligence upload API now supports more STIX objects
- Microsoft Defender Threat Intelligence data connectors now generally available (GA)
- Bicep template support for repositories (Preview)
- SOC optimization updates for unified coverage management
- View granular solution content in the Microsoft Sentinel content hub
Optimize threat intelligence feeds with ingestion rules
Optimize threat intelligence feeds by filtering and enhancing objects before they're delivered to your workspace. Ingestion rules update threat intel object attributes, or filter objects out all together. Check out the blog announcement here!
For more information, see Understand threat intelligence ingestion rules.
Matching analytics rule now generally available (GA)
Microsoft provides access to its premium threat intelligence through the Defender Threat Intelligence analytics rule which is now generally available (GA). For more information on how to take advantage of this rule, which generates high-fidelity alerts and incidents, see Use matching analytics to detect threats.
Threat intelligence management interface has moved
Threat intelligence for Microsoft Sentinel in the Defender portal has changed! We've renamed the page Intel management and moved it with other threat intelligence workflows. There's no change for customers using Microsoft Sentinel in the Azure experience.

Enhancements to threat intelligence capabilities are available for customers using both Microsoft Sentinel experiences. The management interface streamlines the creation and curation of threat intel with these key features:
- Define relationships as you create new STIX objects.
- Curate existing threat intelligence with the new relationship builder.
- Create multiple objects quickly by copying common metadata from a new or existing TI object using a duplication feature.
- Use advanced search to sort and filter your threat intelligence objects without even writing a Log Analytics query.
For more information, see the following articles:
- New STIX objects in Microsoft Sentinel
- Understand threat intelligence
- Uncover adversaries with threat intelligence in Microsoft's unified SecOps platform
Unlock advanced hunting with new STIX objects by opting in to new threat intelligence tables
Tables supporting the new STIX object schema aren't available publicly. In order to query threat intelligence for STIX objects with KQL and unlock the hunting model that uses them, request to opt in with this form. Ingest your threat intelligence into the new tables, ThreatIntelIndicator and ThreatIntelObjects alongside with or instead of the current table, ThreatIntelligenceIndicator, with this opt-in process.
For more information, see the blog announcement New STIX objects in Microsoft Sentinel.
Threat intelligence upload API now supports more STIX objects
Make the most of your threat intelligence platforms when you connect them to Microsoft Sentinel with the upload API. Now you can ingest more objects than just indicators, reflecting the varied threat intelligence available. The upload API supports the following STIX objects:
indicatorattack-patternidentitythreat-actorrelationship
For more information, see the following articles:
- Connect your threat intelligence platform with the upload API (Preview)
- Import threat intelligence to Microsoft Sentinel with the upload API (Preview)
- New STIX objects in Microsoft Sentinel
Microsoft Defender Threat Intelligence data connectors now generally available (GA)
Both premium and standard Microsoft Defender Threat Intelligence data connectors are now generally available (GA) in content hub. For more information, see the following articles:
- Explore Defender Threat Intelligence licenses
- Enable the Microsoft Defender Threat Intelligence data connector
Bicep template support for repositories (Preview)
Use Bicep templates alongside or as a replacement of ARM JSON templates in Microsoft Sentinel repositories. Bicep provides an intuitive way to create templates of Azure resources and Microsoft Sentinel content items. Not only is it easier to develop new content items, Bicep makes reviewing and updating content easier for anyone that's a part of the continuous integration and delivery of your Microsoft Sentinel content.
For more information, see Plan your repository content.
SOC optimization updates for unified coverage management
In workspaces enabled for unified security operations, SOC optimizations now support both SIEM and XDR data, with detection coverage from across Microsoft Defender services.
In the Defender portal, the SOC optimizations and MITRE ATT&CK pages also now provide extra functionality for threat-based coverage optimizations to help you understand the impact of the recommendations on your environment and help you prioritize which to implement first.
Enhancements include:
| Area | Details |
|---|---|
| SOC optimizations Overview page | - A High, Medium, or Low score for your current detection coverage. This sort of scoring can help you decide which recommendations to prioritize at a glance. - An indication of the number of active Microsoft Defender products (services) out of all available products. This helps you understand whether there's a whole product that you're missing in your environment. |
| Optimization details side pane, shown when you drill down to a specific optimization |
- Detailed coverage analysis, including the number of user-defined detections, response actions, and products you have active. - Detailed spider charts that show your coverage across different threat categories, for both user-defined and out-of-the-box detections. - An option to jump to the specific threat scenario in the MITRE ATT&CK page instead of viewing MITRE ATT&CK coverage only in the side pane. - An option to View full threat scenario to drill down to even further details about the security products and detections available to provide security coverage in your environment. |
| MITRE ATT&CK page | - A new toggle to view coverage by threat scenario. If you've jumped to the MITRE ATT&CK page from either a recommendation details side pane or from the View full threat scenario page, the MITRE ATT&CK page is pre-filtered for your threat scenario. - The technique details pane, shown on the side when you select a specific MITRE ATT&CK technique, now shows the number of active detections out of all available detections for that technique. |
For more information, see Optimize your security operations and Understand security coverage by the MITRE ATT&CK framework.
View granular solution content in the Microsoft Sentinel content hub
Now you can view the individual content available in a specific solution directly from the Content hub, even before you've installed the solution. This new visibility helps you understand the content available to you, and more easily identify, plan, and install the specific solutions you need.
Expand each solution in the Content hub to view included security content. For example:
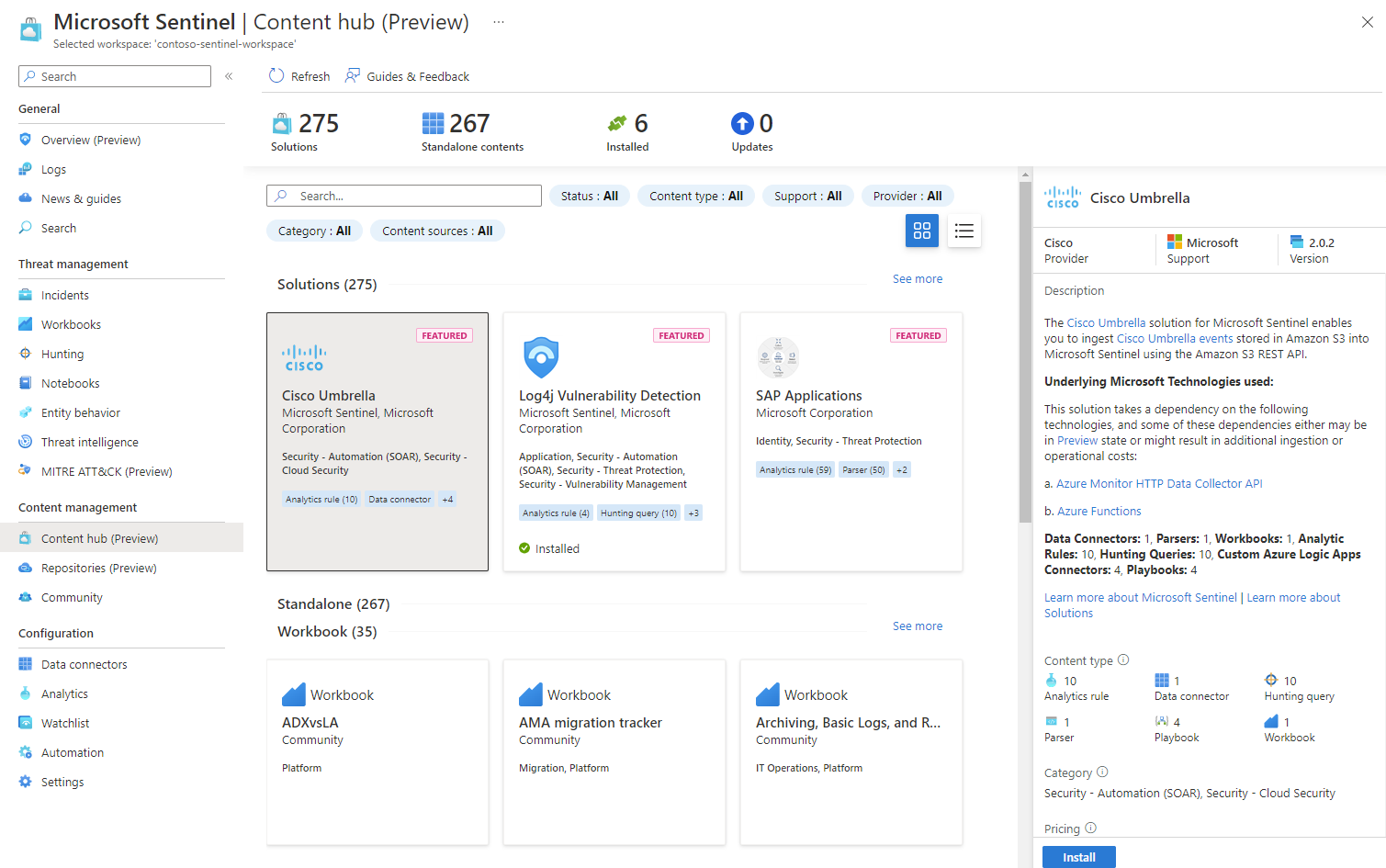
The granular solution content updates also include a generative AI-based search engine that helps you run more robust searches, diving deep into the solution content and returning results for similar terms.
For more information, see Discover content.
December 2024
- New SOC optimization recommendation based on similar organizations (Preview)
- Agentless deployment for SAP applications (Limited preview)
- Microsoft Sentinel workbooks now available to view directly in the Microsoft Defender portal
- Unified Microsoft Sentinel solution for Microsoft Business Apps
- New documentation library for Microsoft's unified security operations platform
- New S3-based data connector for Amazon Web Services WAF logs (Preview)
New SOC optimization recommendation based on similar organizations (Preview)
SOC optimization now includes new recommendations for adding data sources to your workspace based on the security posture of other customers in similar industries and sectors as you, and with similar data ingestion patterns. Add the recommended data sources to improve security coverage for your organization.
For more information, see SOC optimization reference of recommendations.
Agentless deployment for SAP applications (Limited preview)
The Microsoft Sentinel solution for SAP applications now supports an agentless deployment, using SAP's own cloud platform features to provide simplified, agentless deployment and connectivity. Instead of deploying a virtual machine and containerized agent, use the SAP Cloud Connector and its existing connections to back-end ABAP systems to connect your SAP system to Microsoft Sentinel.
The Agentless solution uses the SAP Cloud Connector and SAP Integration Suite, which are already familiar to most SAP customers. This significantly reduces deployment times, especially for those less familiar with Docker, Kubernetes, and Linux administration. By using the SAP Cloud Connector, the solution profits from already existing setups and established integration processes. This means you don't have to tackle network challenges again, as the people running your SAP Cloud Connector have already gone through that process.
The Agentless solution is compatible with SAP S/4HANA Cloud, Private Edition RISE with SAP, SAP S/4HANA on-premises, and SAP ERP Central Component (ECC), ensuring continued functionality of existing security content, including detections, workbooks, and playbooks.
Important
Microsoft Sentinel's Agentless solution is in limited preview as a prereleased product, which may be substantially modified before it's commercially released. Microsoft makes no warranties expressed or implied, with respect to the information provided here. Access to the Agentless solution also requires registration and is only available to approved customers and partners during the preview period.
For more information, see:
- Microsoft Sentinel for SAP goes agentless
- Sign up for the limited preview
- Microsoft Sentinel solution for SAP applications: Deployment overview
Microsoft Sentinel workbooks now available to view directly in the Microsoft Defender portal
Microsoft Sentinel workbooks are now available for viewing directly in the Microsoft Defender portal with Microsoft's unified security operations (SecOps) platform. Now, in the Defender portal, when you select Microsoft Sentinel > Threat management> Workbooks, you remain in the Defender portal instead of a new tab being opened for workbooks in the Azure portal. Continue tabbing out to the Azure portal only when you need to edit your workbooks.
Microsoft Sentinel workbooks are based on Azure Monitor workbooks, and help you visualize and monitor the data ingested to Microsoft Sentinel. Workbooks add tables and charts with analytics for your logs and queries to the tools already available.
For more information, see Visualize and monitor your data by using workbooks in Microsoft Sentinel and Connect Microsoft Sentinel to Microsoft Defender XDR.
Unified Microsoft Sentinel solution for Microsoft Business Apps
Microsoft Sentinel now provides a unified solution for Microsoft Power Platform, Microsoft Dynamics 365 Customer Engagement, and Microsoft Dynamics 365 Finance and Operations. The solution includes data connectors and security content for all platforms.
The updated solution removes the Dynamics 365 CE Apps and the Dynamics 365 Finance and Operations solutions from the Microsoft Sentinel Content hub. Existing customers will see that these solutions are renamed to the Microsoft Business Applications solution.
The updated solution also removes the Power Platform Inventory data connector. While the Power Platform Inventory data connector continues to be supported on workspaces where it's already deployed, it isn't available for new deployments in other workspaces.
For more information, see:
What is the Microsoft Sentinel solution for Microsoft Business Apps?
Microsoft Power Platform and Microsoft Dynamics 365 Customer Engagement:
Microsoft Dynamics 365 Finance and Operations:
New documentation library for Microsoft's unified security operations platform
Find centralized documentation about Microsoft's unified SecOps platform in the Microsoft Defender portal. Microsoft's unified SecOps platform brings together the full capabilities of Microsoft Sentinel, Microsoft Defender XDR, Microsoft Security Exposure Management, and generative AI into the Defender portal. Learn about the features and functionality available with Microsoft's unified SecOps platform, then start to plan your deployment.
New S3-based data connector for Amazon Web Services WAF logs (Preview)
Ingest logs from Amazon Web Services' web application firewall (WAF) with Microsoft Sentinel's new S3-based connector. This connector features, for the first time, a quick and easy automated setup, making use of AWS CloudFormation templates for resource creation. Send your AWS WAF logs to an S3 bucket, where our data connector retrieves and ingests them.
For more details and setup instructions, see Connect Microsoft Sentinel to Amazon Web Services to ingest AWS WAF logs.
November 2024
Microsoft Sentinel availability in Microsoft Defender portal
We previously announced Microsoft Sentinel is generally available within Microsoft's unified security operations platform in the Microsoft Defender portal.
Now, in preview, Microsoft Sentinel is available in the Defender portal even without Microsoft Defender XDR or a Microsoft 365 E5 license. For more information, see:
- Microsoft Sentinel in the Microsoft Defender portal
- Connect Microsoft Sentinel to the Microsoft Defender portal
October 2024
Updates for the Microsoft Sentinel solution for Microsoft Power Platform
Starting on October 17, 2024, audit logging data for Power Apps, Power Platform DLP, and Power Platform Connectors is routed to the PowerPlatformAdminActivity table instead of the PowerAppsActivity, PowerPlatformDlpActivity and PowerPlatformConnectorActivity tables.
Security content in the Microsoft Sentinel solution for Microsoft Power Platform is updated with the new table and schemas for the Power Apps, Power Platform DLP, and Power Platform Connectors. We recommend that you update the Power Platform solution in your workspace to the latest version and apply the updated analytics rule templates to benefit from the changes. For more information, see Install or update content.
Customers using deprecated data connectors for Power Apps, Power Platform DLP, and Power Platform Connectors can safely disconnect and remove these connectors from their Microsoft Sentinel workspace. All associated data flows are ingested using Power Platform Admin Activity connector.
For more information, see Message center.
September 2024
- Schema mapping added to the SIEM migration experience
- Third-party enrichment widgets to be retired in February 2025
- Azure reservations now have pre-purchase plans available for Microsoft Sentinel
- Import/export of automation rules now generally available (GA)
- Google Cloud Platform data connectors are now generally available (GA)
- Microsoft Sentinel now generally available (GA) in Azure Israel Central
Schema mapping added to the SIEM migration experience
Since the SIEM migration experience became generally available in May 2024, steady improvements have been made to help migrate your security monitoring from Splunk. The following new features let customers provide more contextual details about their Splunk environment and usage to the Microsoft Sentinel SIEM Migration translation engine:
- Schema Mapping
- Support for Splunk Macros in translation
- Support for Splunk Lookups in translation
To learn more about these updates, see SIEM migration experience.
For more information about the SIEM migration experience, see the following articles:
- Become a Microsoft Sentinel ninja - migration section
- SIEM migration update - Microsoft Sentinel blog
Third-party enrichment widgets to be retired in February 2025
Effective immediately, you can no longer enable the feature to create enrichment widgets that retrieve data from external, third-party data sources. These widgets are displayed on Microsoft Sentinel entity pages and in other locations where entity information is presented. This change is happening because you can no longer create the Azure key vault required to access these external data sources.
If you already use any third-party enrichment widgets, that is, if this key vault already exists, you can still configure and use widgets that you weren't using before, though we don't recommend doing so.
As of February 2025, any existing enrichment widgets that retrieve data from third-party sources will stop being displayed, on entity pages or anywhere else.
If your organization uses third-party enrichment widgets, we recommend disabling them in advance, by deleting the key vault you created for this purpose from its resource group. The key vault's name begins with "widgets".
Enrichment widgets based on first-party data sources are not affected by this change, and will continue to function as before. "First-party data sources" include any data that's already ingested into Microsoft Sentinel from external sources—in other words, anything in tables in your Log Analytics workspace—and Microsoft Defender Threat Intelligence.
Pre-purchase plans now available for Microsoft Sentinel
Pre-purchase plans are a type of Azure reservation. When you buy a pre-purchase plan, you get commit units (CUs) at discounted tiers for a specific product. Microsoft Sentinel commit units (SCUs) apply towards eligible costs in your workspace. When you have predictable costs, choosing the right pre-purchase plan saves you money!
For more information, see Optimize costs with a pre-purchase plan.
Import/export of automation rules now generally available (GA)
The ability to export automation rules to Azure Resource Manager (ARM) templates in JSON format, and to import them from ARM templates, is now generally available after a short preview period.
Learn more about exporting and importing automation rules.
Google Cloud Platform data connectors are now generally available (GA)
Microsoft Sentinel's Google Cloud Platform (GCP) data connectors, based on our Codeless Connector Platform (CCP), are now generally available. With these connectors, you can ingest logs from your GCP environment using the GCP Pub/Sub capability:
The Google Cloud Platform (GCP) Pub/Sub Audit Logs connector collects audit trails of access to GCP resources. Analysts can monitor these logs to track resource access attempts and detect potential threats across the GCP environment.
The Google Cloud Platform (GCP) Security Command Center connector collects findings from Google Security Command Center, a robust security and risk management platform for Google Cloud. Analysts can view these findings to gain insights into the organization's security posture, including asset inventory and discovery, detections of vulnerabilities and threats, and risk mitigation and remediation.
For more information on these connectors, see Ingest Google Cloud Platform log data into Microsoft Sentinel.
Microsoft Sentinel now generally available (GA) in Azure Israel Central
Microsoft Sentinel is now available in the Israel Central Azure region, with the same feature set as all other Azure Commercial regions.
For more information, see as Microsoft Sentinel feature support for Azure commercial/other clouds and Geographical availability and data residency in Microsoft Sentinel.
August 2024
- Log Analytics agent retirement
- Export and import automation rules (Preview)
- Microsoft Sentinel support in Microsoft Defender multitenant management (Preview)
- Premium Microsoft Defender Threat Intelligence data connector (Preview)
- Unified AMA-based connectors for syslog ingestion
- Better visibility for Windows security events
- New Auxiliary logs retention plan (Preview)
- Create summary rules for large sets of data (Preview)
Log Analytics agent retirement
As of August 31, 2024, the Log Analytics Agent (MMA/OMS) is retired.
Log collection from many appliances and devices is now supported by the Common Event Format (CEF) via AMA, Syslog via AMA, or Custom Logs via AMA data connector in Microsoft Sentinel. If you've been using the Log Analytics agent in your Microsoft Sentinel deployment, we recommend that you migrate to the Azure Monitor Agent (AMA).
For more information, see:
- Find your Microsoft Sentinel data connector
- Migrate to Azure Monitor Agent from Log Analytics agent
- AMA migration for Microsoft Sentinel
- Blogs:
Export and import automation rules (Preview)
Manage your Microsoft Sentinel automation rules as code! You can now export your automation rules to Azure Resource Manager (ARM) template files, and import rules from these files, as part of your program to manage and control your Microsoft Sentinel deployments as code. The export action will create a JSON file in your browser's downloads location, that you can then rename, move, and otherwise handle like any other file.
The exported JSON file is workspace-independent, so it can be imported to other workspaces and even other tenants. As code, it can also be version-controlled, updated, and deployed in a managed CI/CD framework.
The file includes all the parameters defined in the automation rule. Rules of any trigger type can be exported to a JSON file.
Learn more about exporting and importing automation rules.
Microsoft Sentinel support in Microsoft Defender multitenant management (Preview)
If you've onboarded Microsoft Sentinel to the Microsoft unified security operations platform, Microsoft Sentinel data is now available with Defender XDR data in Microsoft Defender multitenant management. Only one Microsoft Sentinel workspace per tenant is currently supported in the Microsoft unified security operations platform. So, Microsoft Defender multitenant management shows security information and event management (SIEM) data from one Microsoft Sentinel workspace per tenant. For more information, see Microsoft Defender multitenant management and Microsoft Sentinel in the Microsoft Defender portal.
Premium Microsoft Defender Threat Intelligence data connector (Preview)
Your premium license for Microsoft Defender Threat Intelligence (MDTI) now unlocks the ability to ingest all premium indicators directly into your workspace. The premium MDTI data connector adds more to your hunting and research capabilities within Microsoft Sentinel.
For more information, see Understand threat intelligence.
Unified AMA-based connectors for syslog ingestion
With the impending retirement of the Log Analytics Agent, Microsoft Sentinel has consolidated the collection and ingestion of syslog, CEF, and custom-format log messages into three multi-purpose data connectors based on the Azure Monitor Agent (AMA):
- Syslog via AMA, for any device whose logs are ingested into the Syslog table in Log Analytics.
- Common Event Format (CEF) via AMA, for any device whose logs are ingested into the CommonSecurityLog table in Log Analytics.
- New! Custom Logs via AMA (Preview), for any of 15 device types, or any unlisted device, whose logs are ingested into custom tables with names ending in _CL in Log Analytics.
These connectors replace nearly all the existing connectors for individual device and appliance types that have existed until now, that were based on either the legacy Log Analytics agent (also known as MMA or OMS) or the current Azure Monitor Agent. The solutions provided in the content hub for all of these devices and appliances now include whichever of these three connectors are appropriate to the solution.* The replaced connectors are now marked as "Deprecated" in the data connector gallery.
The data ingestion graphs that were previously found in each device's connector page can now be found in device-specific workbooks packaged with each device's solution.
* When installing the solution for any of these applications, devices, or appliances, to ensure that the accompanying data connector is installed, you must select Install with dependencies on the solution page, and then mark the data connector on the following page.
For the updated procedures for installing these solutions, see the following articles:
- CEF via AMA data connector - Configure specific appliance or device for Microsoft Sentinel data ingestion
- Syslog via AMA data connector - Configure specific appliance or device for Microsoft Sentinel data ingestion
- Custom Logs via AMA data connector - Configure data ingestion to Microsoft Sentinel from specific applications
Better visibility for Windows security events
We've enhanced the schema of the SecurityEvent table that hosts Windows Security events, and have added new columns to ensure compatibility with the Azure Monitor Agent (AMA) for Windows (version 1.28.2). These enhancements are designed to increase the visibility and transparency of collected Windows events. If you're not interested in receiving data in these fields, you can apply an ingestion-time transformation ("project-away" for example) to drop them.
New Auxiliary logs retention plan (Preview)
The new Auxiliary logs retention plan for Log Analytics tables allows you to ingest large quantities of high-volume logs with supplemental value for security at a much lower cost. Auxiliary logs are available with interactive retention for 30 days, in which you can run simple, single-table queries on them, such as to summarize and aggregate the data. Following that 30-day period, auxiliary log data goes to long-term retention, which you can define for up to 12 years, at ultra-low cost. This plan also allows you to run search jobs on the data in long-term retention, extracting only the records you want to a new table that you can treat like a regular Log Analytics table, with full query capabilities.
To learn more about Auxiliary logs and compare with Analytics logs, see Log retention plans in Microsoft Sentinel.
For more in-depth information about the different log management plans, see Table plans in the Azure Monitor Logs overview article from the Azure Monitor documentation.
Create summary rules in Microsoft Sentinel for large sets of data (Preview)
Microsoft Sentinel now provides the ability to create dynamic summaries using Azure Monitor summary rules, which aggregate large sets of data in the background for a smoother security operations experience across all log tiers.
- Access summary rule results via Kusto Query Language (KQL) across detection, investigation, hunting, and reporting activities.
- Run high performance Kusto Query Language (KQL) queries on summarized data.
- Use summary rule results for longer periods in investigations, hunting, and compliance activities.
For more information, see Aggregate Microsoft Sentinel data with summary rules.