Link query results to an incident
Applies to:
- Microsoft Defender XDR
You can use the link to incident feature to add advanced hunting query results to a new or existing incident under investigation. This feature helps you easily capture records from advanced hunting activities, which enables you to create a richer timeline or context of events regarding an incident.
Link results to new or existing incidents
In the advanced hunting query page, first enter your query in the query field provided then select Run query to get your results.
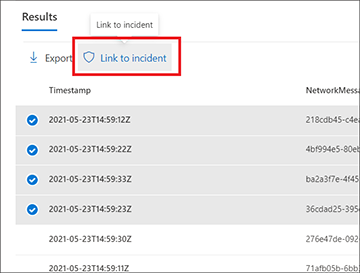
In the Results page, select the events or records that are related to a new or current investigation you're working on, then select Link to incident.
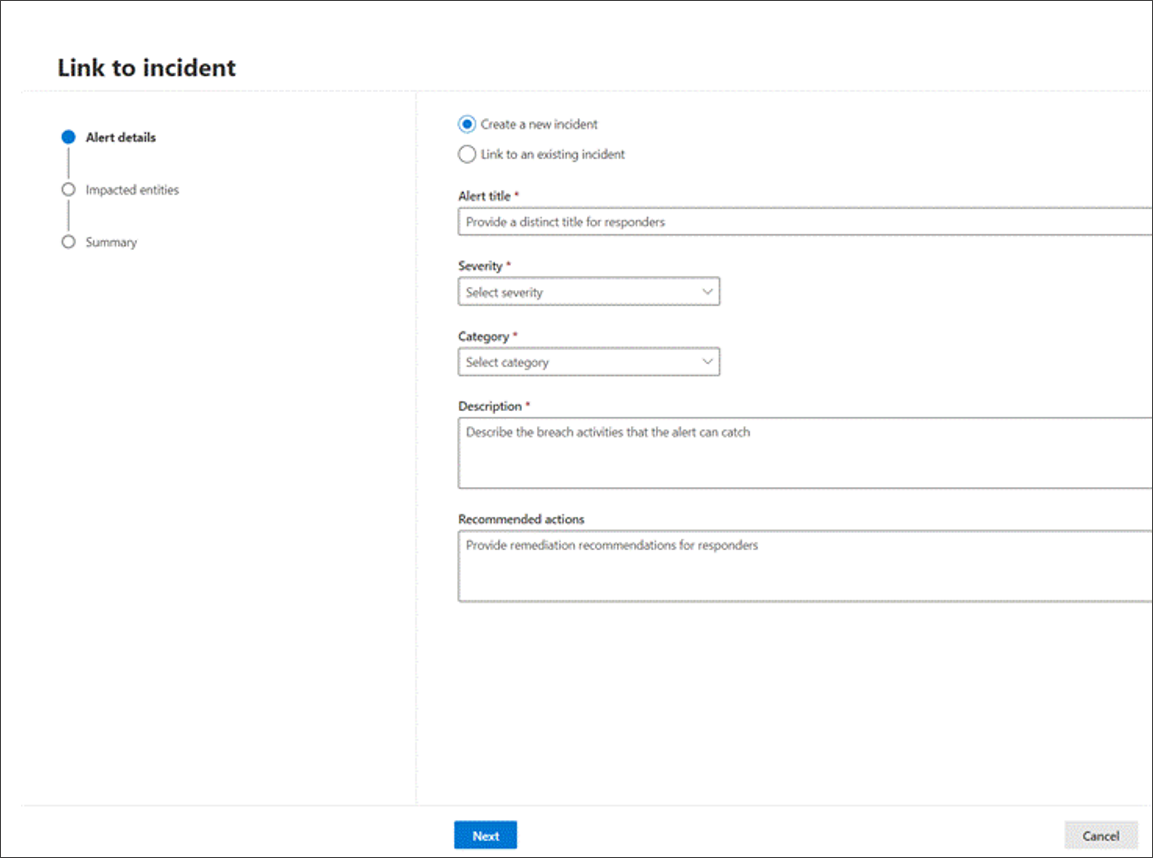
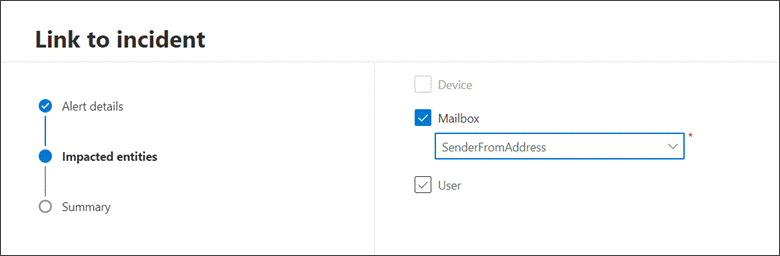
Find the Alert details section in the Link to incident pane, then select Create new incident to convert the events to alerts and group them to a new incident:
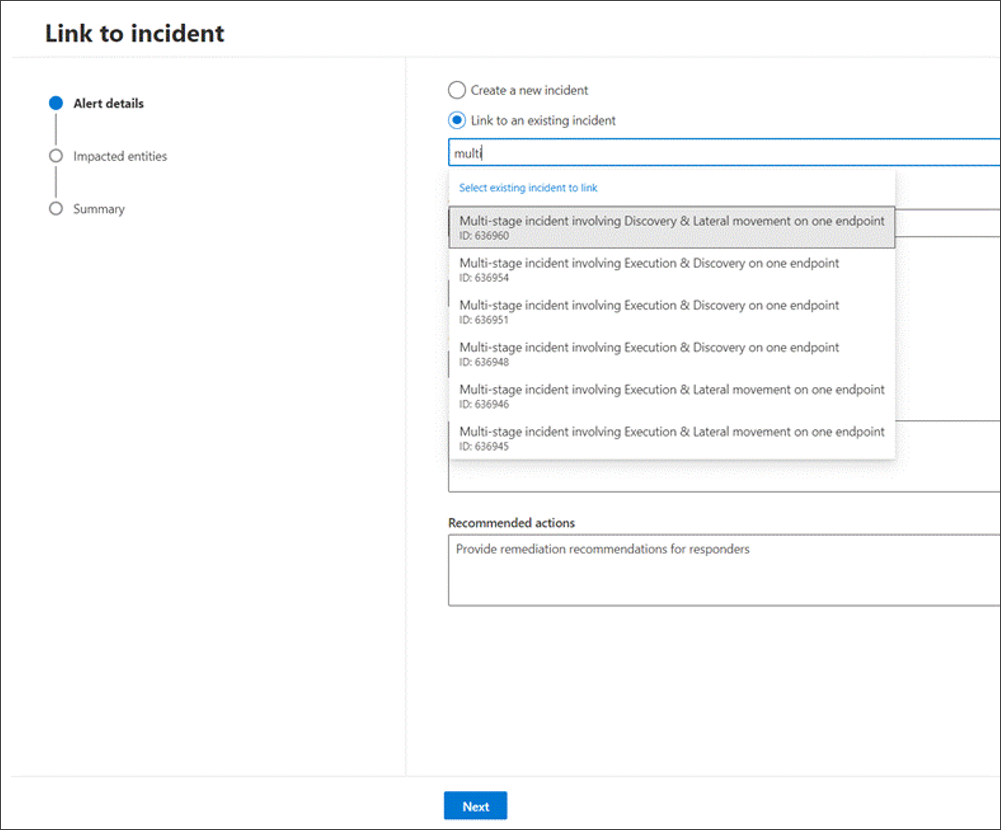
Or select Link to an existing incident to add the selected records to an existing one. Choose the related incident from the dropdown list of existing incidents. You can also enter the first few characters of the incident name or ID to find the existing incident.
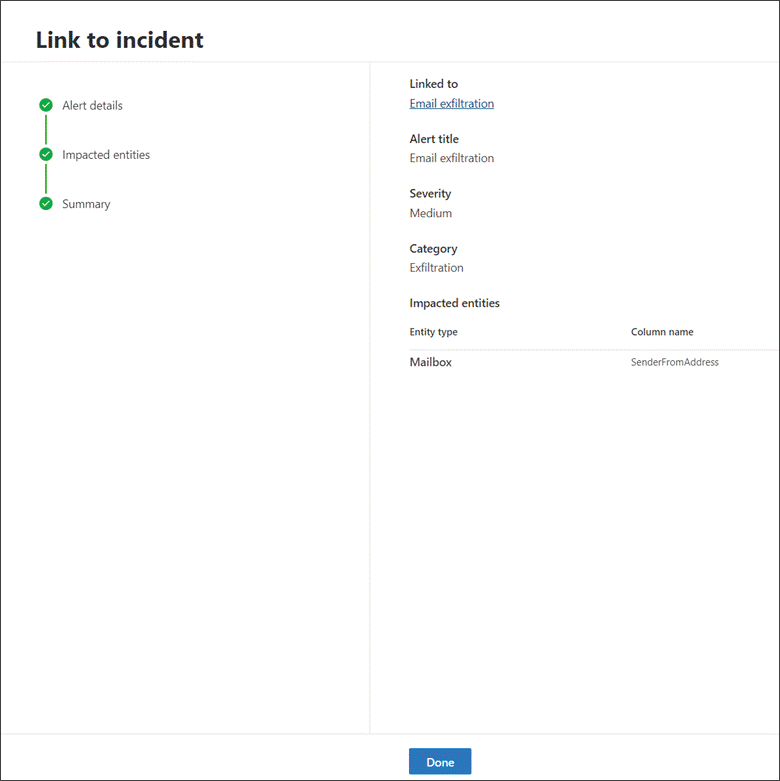
For either selection, provide the following details, then select Next:
- Alert title - provide a descriptive title for the results that your incident responders can understand. This descriptive title becomes the alert title.
- Severity - Choose the severity applicable to the group of alerts.
- Category - Choose the appropriate threat category for the alerts.
- Description - Give a helpful description for the grouped alerts.
- Recommended actions - Provide remediation actions.
In the Impacted entities section, select the main affected or impacted entity. Only the applicable entities based on the query results appear in this section. In our example, we used a query to find events related to a possible email exfiltration incident, therefore the Sender is the impacted entity. If there are four different senders, for instance, four alerts are created and linked to the chosen incident.
Select Next.
Select Done.
View linked records in the incident
You can select the incident name to view the incident that the events are linked to.
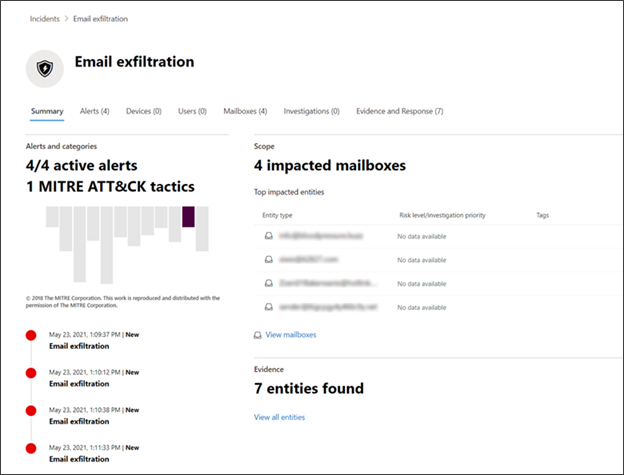
In our example, the four alerts, representing the four selected events, were linked successfully to a new incident.
In each of the alert pages, you can find the complete information on the event or events in timeline view (if available) and query results view.
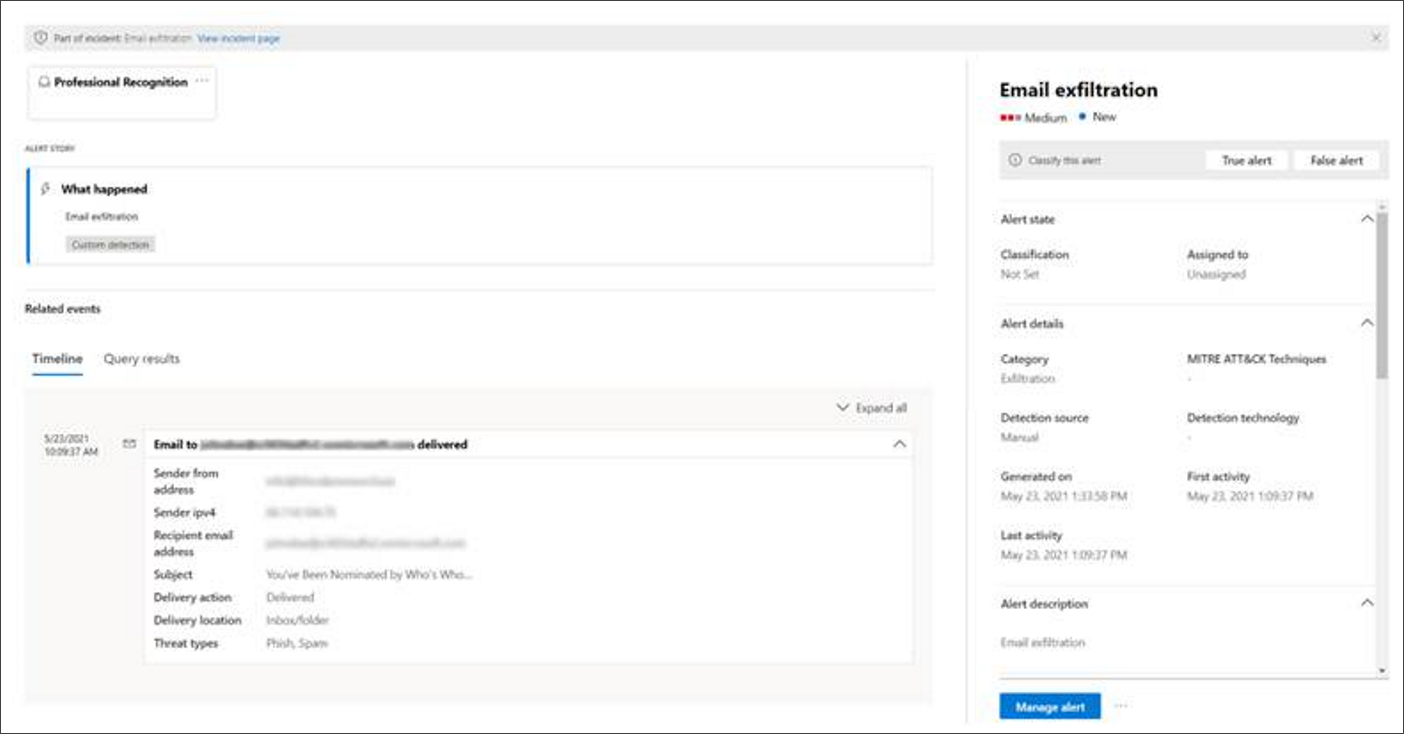
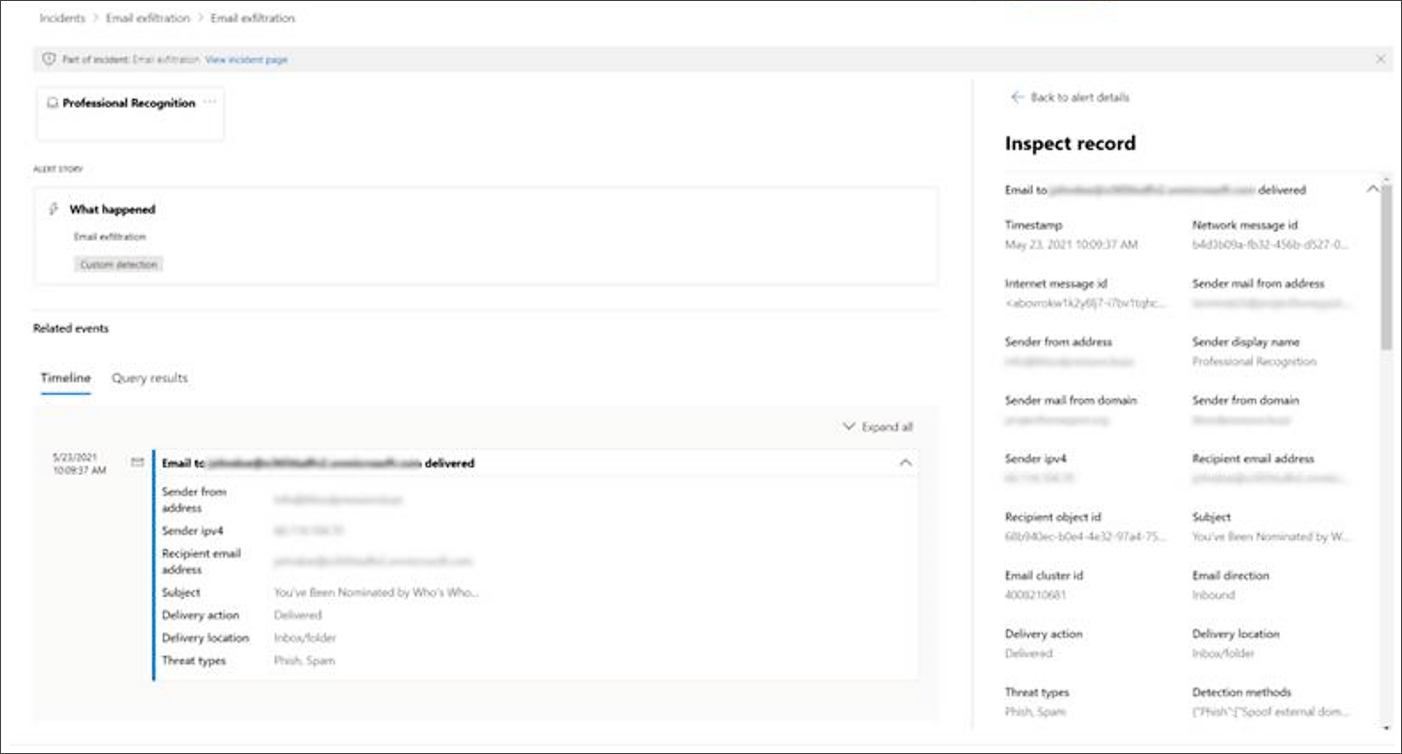
You can also select the event to open the Inspect record pane.
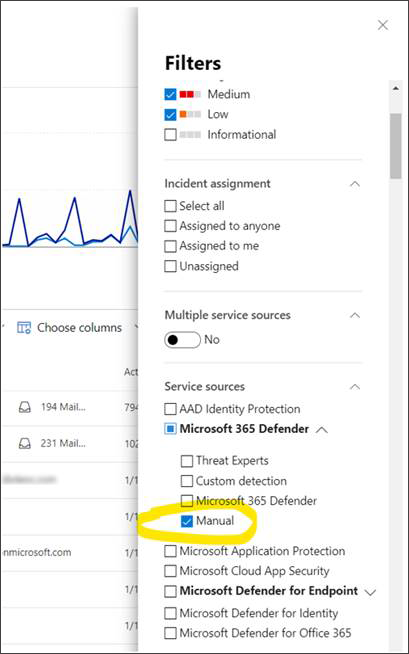
Filter for events added using advanced hunting
You can view which alerts were generated from advanced hunting by filtering the Incidents queue and Alerts queue by Manual detection source.
Tip
Do you want to learn more? Engage with the Microsoft Security community in our Tech Community: Microsoft Defender XDR Tech Community.
Atsauksmes
Drīzumā: 2024. gada laikā mēs pakāpeniski pārtrauksim izmantot “GitHub problēmas” kā atsauksmju par saturu mehānismu un aizstāsim to ar jaunu atsauksmju sistēmu. Papildinformāciju skatiet: https://aka.ms/ContentUserFeedback.
Iesniegt un skatīt atsauksmes par