Custom roles in role-based access control for Microsoft Defender portal services
By default, access to services available in the Microsoft Defender portal are managed collectively using Microsoft Entra global roles. If you need greater flexibility and control over access to specific product data, and aren't yet using the Microsoft Defender XDR Unified role-based access control (RBAC) for centralized permissions management, we recommend creating custom roles for each service.
For example, create a custom role for Microsoft Defender for Endpoint to manage access to specific Defender for Endpoint data, or create a custom role for Microsoft Defender for Office to manage access to specific email and collaboration data.
Applies to:
- Microsoft Defender for Cloud
- Microsoft Defender for Cloud Apps
- Microsoft Defender for Endpoint
- Microsoft Defender for Identity
- Microsoft Defender for IoT
- Microsoft Defender for Office 365
- Microsoft Defender XDR
- Microsoft Security Exposure Management (preview)
- Microsoft Sentinel
Important
Some information in this article relates to a prereleased product which may be substantially modified before it's commercially released. Microsoft makes no warranties, expressed or implied, with respect to the information provided here.
Locate custom role management settings in the Microsoft Defender portal
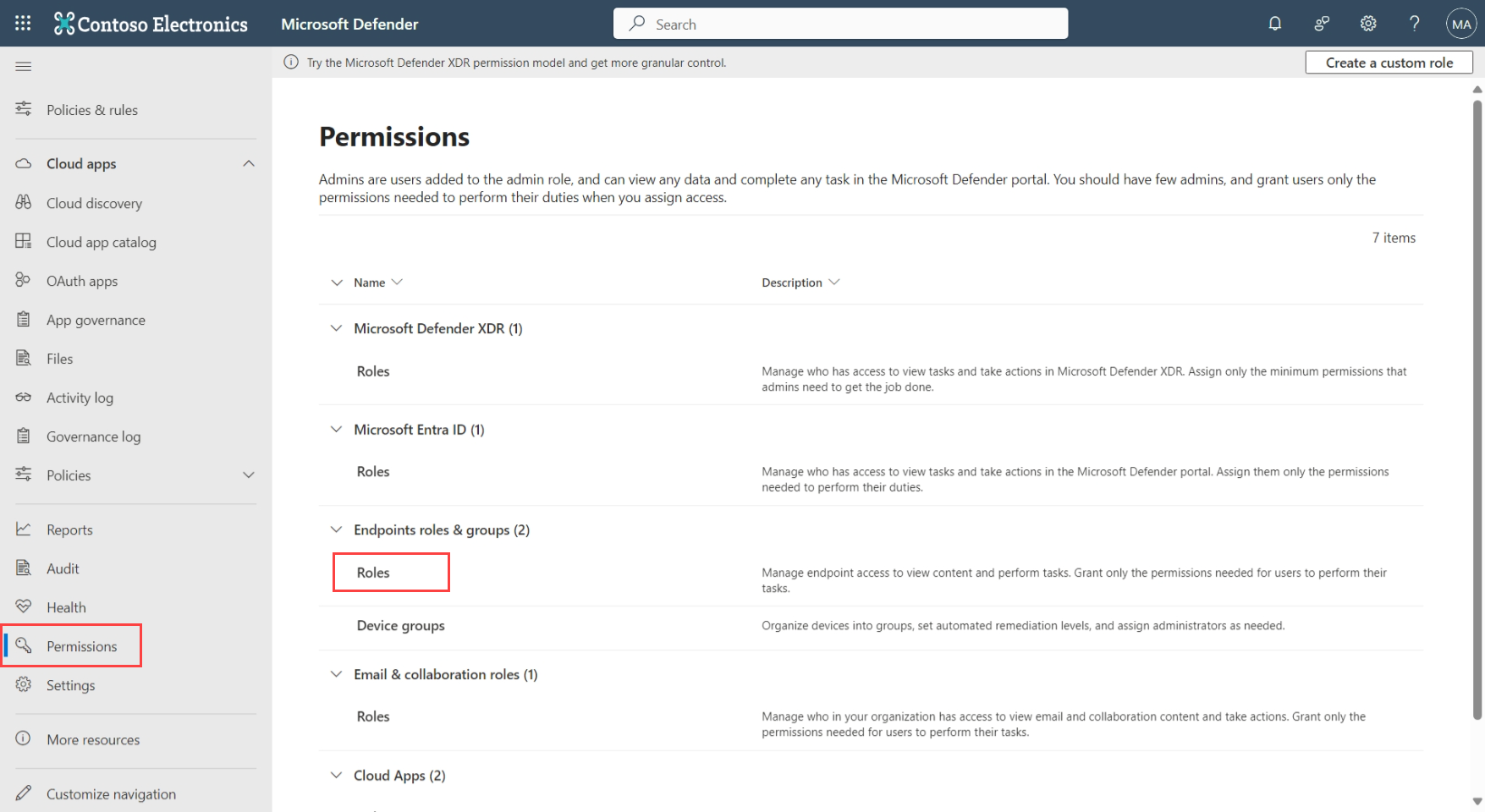
Each Microsoft Defender service has its own custom role management settings, with some services being represented in a central location in the Microsoft Defender portal. To locate custom role management settings in the Microsoft Defender portal:
- Sign in to the Microsoft Defender portal at security.microsoft.com.
- In the navigation pane, select Permissions.
- Select the Roles link for the service where you want to create a custom role. For example, for Defender for Endpoint:
In each service, custom role names aren't connected to global roles in Microsoft Entra ID, even if similarly named. For example, a custom role named Security Admin in Microsoft Defender for Endpoint isn't connected to the global Security Admin role in Microsoft Entra ID.
Reference of Defender portal service content
For information about the permissions and roles for each Microsoft Defender XDR service, see the following articles:
- Microsoft Defender for Cloud user roles and permissions
- Configure access for Defender for Cloud Apps
- Create and manage roles in Defender for Endpoint
- Roles and permissions in Defender for Identity
- Microsoft Defender for IoT user management
- Microsoft Defender for Office 365 permissions
- Manage access to Microsoft Defender XDR
- Microsoft Security Exposure Management permissions
- Roles and permissions in Microsoft Sentinel
Microsoft recommends that you use roles with the fewest permissions. This helps improve security for your organization. Global Administrator is a highly privileged role that should be limited to emergency scenarios when you can't use an existing role.