Example of a phishing email attack
Applies to:
- Microsoft Defender XDR
Microsoft Defender XDR can help detect malicious attachments delivered via email and security analysts can have visibility on threats coming in from Office 365, such as through email attachments.
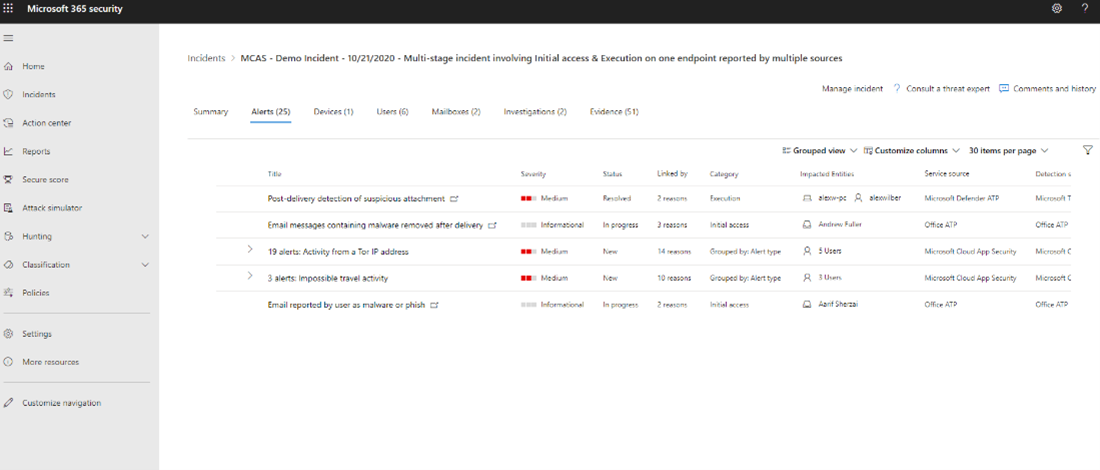
For example, an analyst was assigned a multi-stage incident.
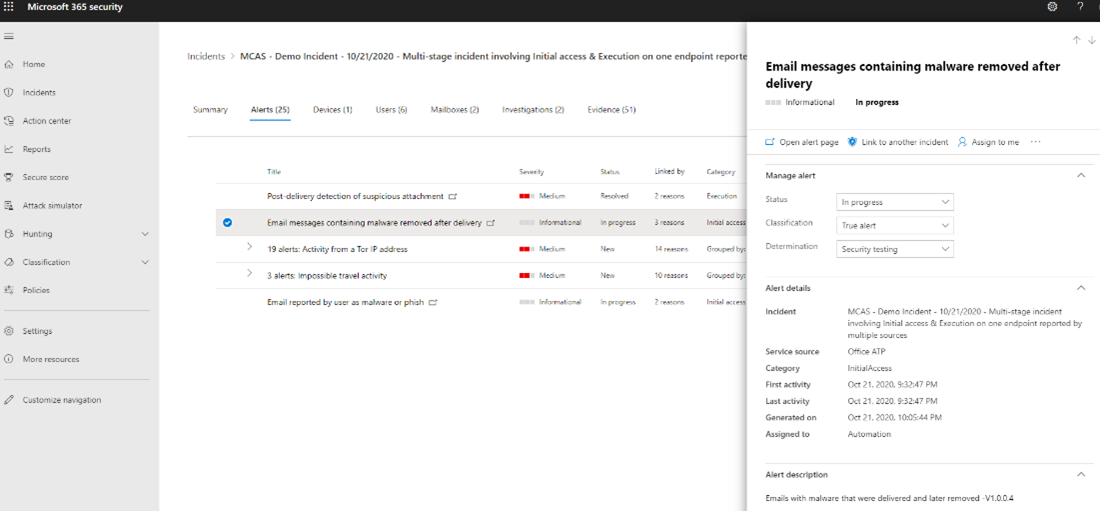
In the Alerts tab of the incident, alerts from Defender for Office 365 and Microsoft Defender for Cloud Apps are displayed. The analyst can drill down into the Defender for Office 365 alerts by selecting the email messages alerts. The details of the alert are displayed on the side pane.
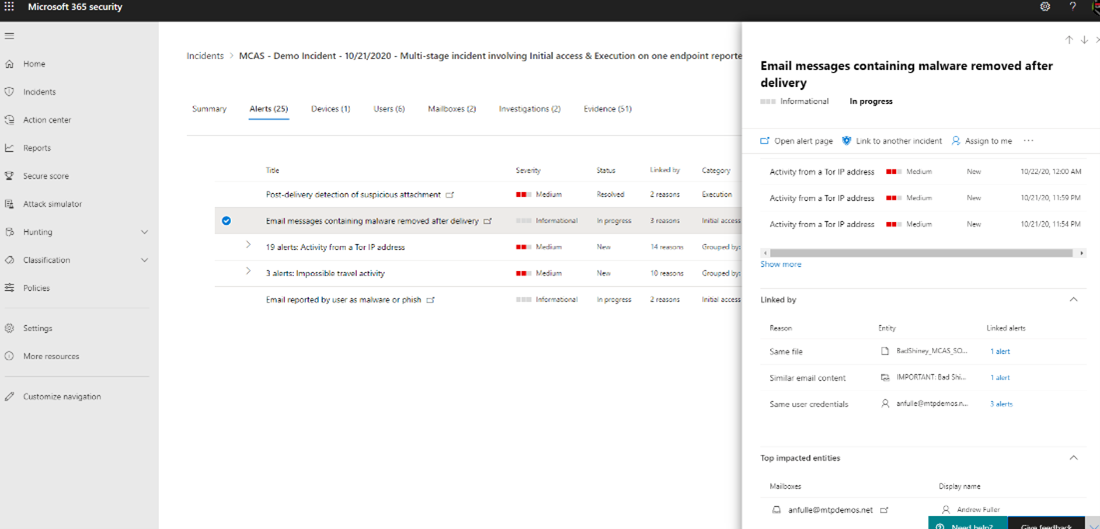
By scrolling down further, more information is displayed, showing the malicious files and user that was impacted.
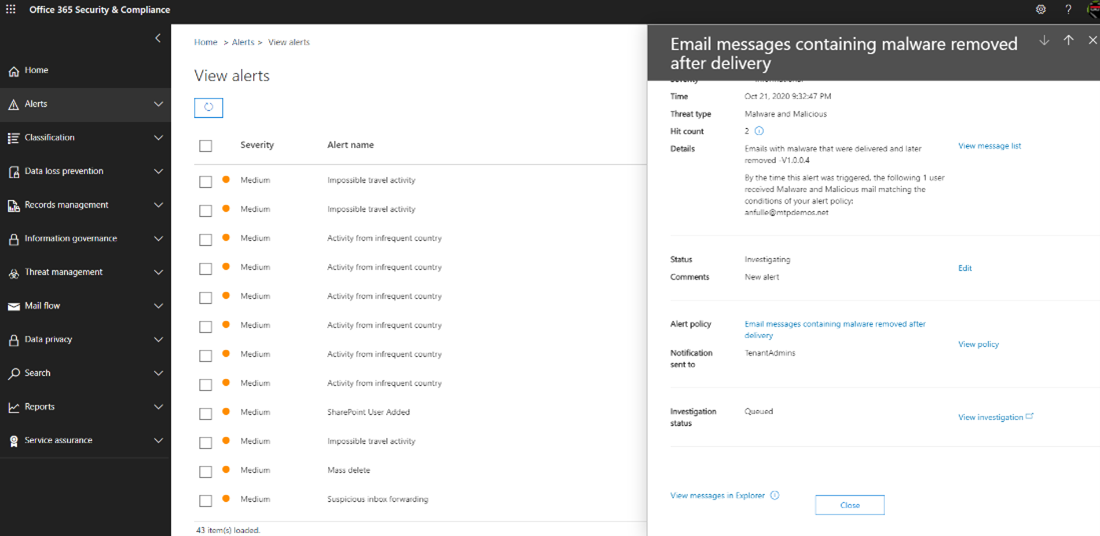
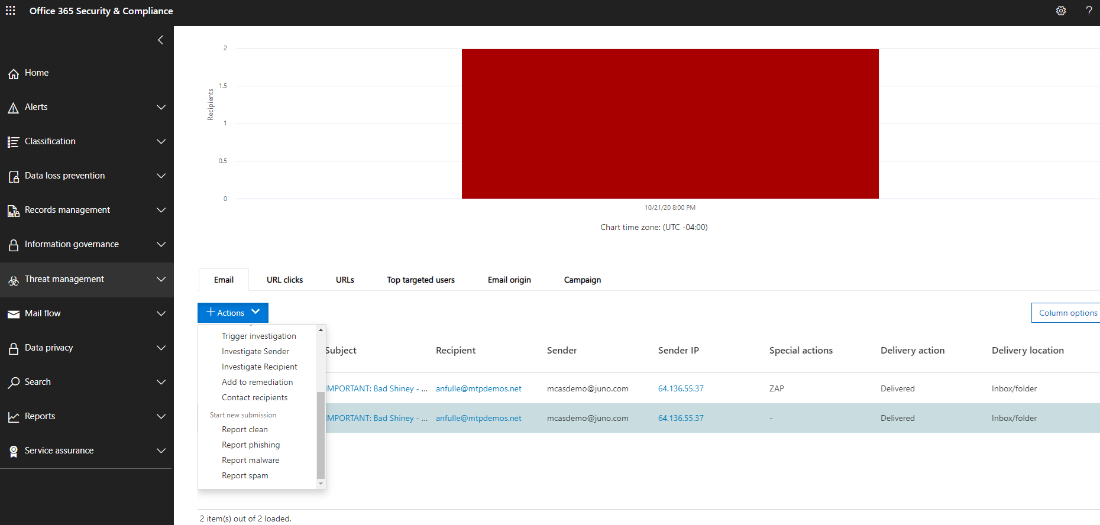
Selecting Open alert page takes you to the specific alert where various information can be viewed in greater detail by selecting the link. The actual email message can be viewed by selecting View messages in Explorer toward the bottom of the panel.
This takes the analyst to the Threat Management page where the email Subject, Recipient, Sender, and other information are displayed. ZAP under Special Actions tells the analyst that the Zero-hour auto purge feature was implemented. ZAP automatically detects and removes malicious and spam messages from mailboxes across the organization. For more information, see Zero-hour auto purge (ZAP) in Exchange Online.
Other actions can be taken on specific messages by selecting Actions.
Next step
See the identity-based attack investigation path.
See also
Tip
Do you want to learn more? Engage with the Microsoft Security community in our Tech Community: Microsoft Defender XDR Tech Community.