Integrate Microsoft Entra single sign-on with Maverics Orchestrator SAML Connector
Strata's Maverics Orchestrator provides a simple way to integrate on-premises applications with Microsoft Entra ID for authentication and access control. The Maverics Orchestrator is capable of modernizing authentication and authorization for apps that currently rely on headers, cookies, and other proprietary authentication methods. Maverics Orchestrator instances can be deployed on-premises or in the cloud.
This hybrid access tutorial demonstrates how to migrate an on-premises web application that's currently protected by a legacy web access management product to use Microsoft Entra ID for authentication and access control. Here are the basic steps:
- Setting up the Maverics Orchestrator
- Proxying an application
- Registering an enterprise application in Microsoft Entra ID
- Authenticating via Microsoft Entra ID and authorizing access to the application
- Adding headers for seamless application access
- Working with multiple applications
Prerequisites
- A Microsoft Entra ID subscription. If you don't have a subscription, you can get a free account.
- A Maverics Identity Orchestrator Platform account. Sign up at maverics.strata.io.
- At least one application that uses header based authentication. In our examples, we'll be working against an application called Sonar that will be reachable at
https://localhost:8443.
Step 1: Setting up the Maverics Orchestrator
After signing up for a Maverics account at maverics.strata.io, use our Learning Center tutorial titled Getting Started: Evaluation Environment. This tutorial takes you through the step-by-step process of creating an evaluation environment, downloading an orchestrator, and installing the orchestrator on your machine.
Step 2: Extending Microsoft Entra ID to an app with a recipe
Next, use the Learning Center tutorial, Extend Microsoft Entra ID to a Legacy, Non-Standard App. This tutorial provides you with a .json recipe that automatically configures an identity fabric, header-based application, and partially complete user flow.
Step 3: Registering an enterprise application in Microsoft Entra ID
We'll now create a new enterprise application in Microsoft Entra ID that is used for authenticating end-users.
Note
When leveraging Microsoft Entra ID features such as Conditional Access it's important to create an enterprise application per on-premises application. This permits per-app conditional access, per-app risk evaluation, per-app assigned permissions, etc. Generally, an enterprise application in Microsoft Entra ID maps to an Azure connector in Maverics.
In your Microsoft Entra ID tenant, go to Enterprise applications, click New Application and search for Maverics Identity Orchestrator SAML Connector in the Microsoft Entra ID gallery, and then select it.
On the Maverics Identity Orchestrator SAML Connector Properties pane, set User assignment required? to No to enable the application to work for all users in your directory.
On the Maverics Identity Orchestrator SAML Connector Overview pane, select Set up single sign-on, and then select SAML.
On the Maverics Identity Orchestrator SAML Connector SAML-based sign on pane, edit the Basic SAML Configuration by selecting the Edit (pencil icon) button.
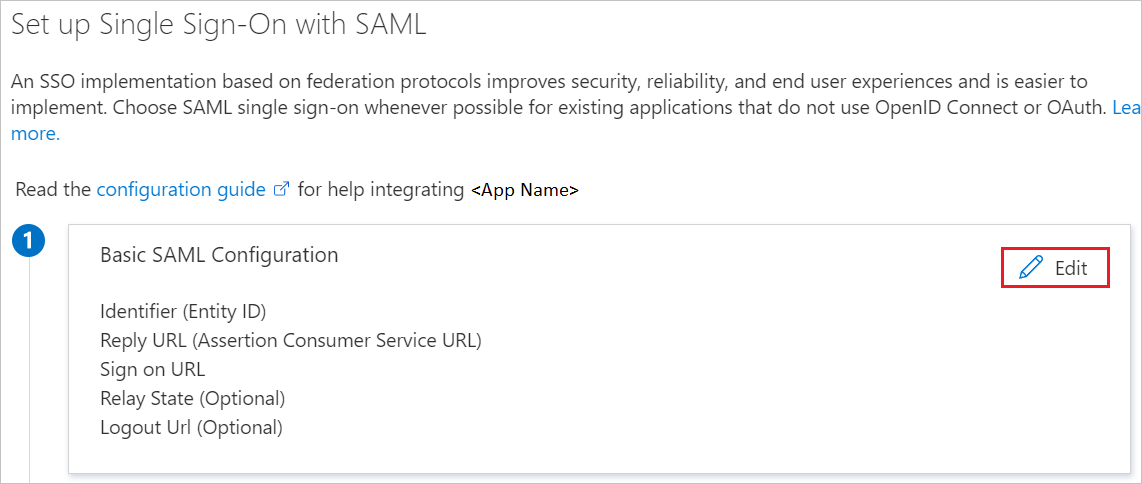
Enter an Entity ID of:
https://sonar.maverics.com. The Entity ID must be unique across the apps in the tenant, and can be an arbitrary value. We use this value when defining thesamlEntityIDfield for our Azure connector in the next section.Enter a Reply URL of:
https://sonar.maverics.com/acs. We use this value when defining thesamlConsumerServiceURLfield for our Azure connector in the next section.Enter a Sign on URL of:
https://sonar.maverics.com/. This field won't be used by Maverics, but it is required in Microsoft Entra ID to enable users to get access to the application through the Microsoft Entra ID My Apps portal.Select Save.
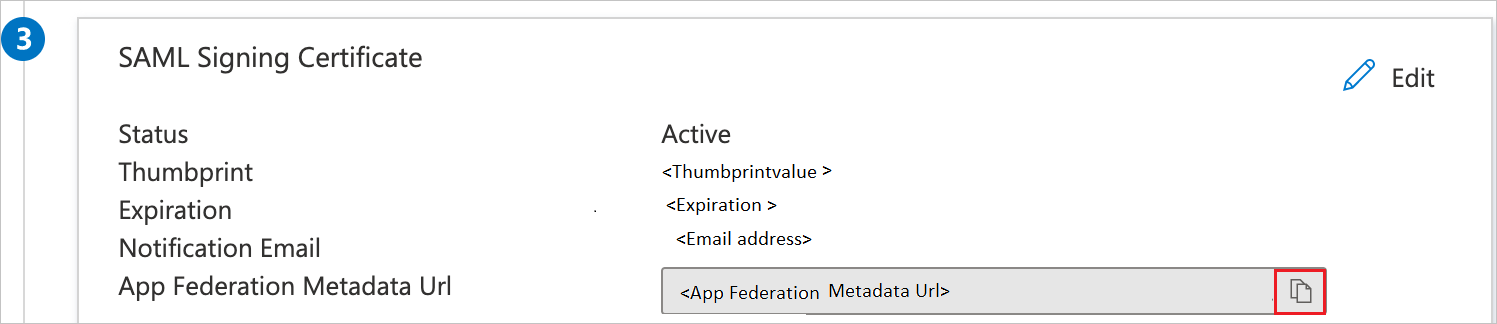
In the SAML Signing Certificate section, select the Copy button to copy the App Federation Metadata URL, and then save it to your computer.
Step 4: Authenticating via Microsoft Entra ID and authorizing access to the application
Continue on with step 4 of the Learning Center topic, Extend Microsoft Entra ID to a Legacy, Non-Standard App to edit your user flow in Maverics. These steps walk you through the process of adding headers to the upstream application and deploying the user flow.
Once you've deployed the user flow, to confirm authentication is working as expected, make a request to an application resource through the Maverics proxy. The protected application should now be receiving headers on the request.
Feel free to edit the header keys if your application expects different headers. All claims that come back from Microsoft Entra ID as part of the SAML flow are available to use in headers. For example, we could include another header of secondary_email: azureSonarApp.email, where azureSonarApp is the connector name and email is a claim returned from Microsoft Entra ID.
Advanced Scenarios
Identity Migration
Can't stand your end-of-life'd web access management tool, but don't have a way to migrate your users without mass password resets? The Maverics Orchestrator supports identity migration by using migrationgateways.
Web Server Modules
Don't want to rework your network and proxy traffic through the Maverics Orchestrator? Not a problem, the Maverics Orchestrator can be paired with web server modules to offer the same solutions without proxying.
Wrapping Up
At this point, we have installed the Maverics Orchestrator, created and configured an enterprise application in Microsoft Entra ID, and configured the Orchestrator to proxy to a protected application while requiring authentication and enforcing policy. To learn more about how the Maverics Orchestrator can be used for distributed identity management use cases please contact Strata.