Tutorial: Configure ThousandEyes for automatic user provisioning
The objective of this tutorial is to show you the steps you need to perform in ThousandEyes and Microsoft Entra ID to automatically provision and de-provision user accounts from Microsoft Entra ID to ThousandEyes.
Prerequisites
The scenario outlined in this tutorial assumes that you already have the following items:
- A Microsoft Entra tenant
- A ThousandEyes tenant with the Standard plan or better enabled
- A user account in ThousandEyes with Admin permissions
Note
The Microsoft Entra provisioning integration relies on the ThousandEyes SCIM API, which is available to ThousandEyes teams on the Standard plan or better.
Assigning users to ThousandEyes
Microsoft Entra ID uses a concept called "assignments" to determine which users should receive access to selected apps. In the context of automatic user account provisioning, only the users and groups that have been "assigned" to an application in Microsoft Entra ID is synchronized.
Before configuring and enabling the provisioning service, you need to decide what users and/or groups in Microsoft Entra ID represent the users who need access to your ThousandEyes app. Once decided, you can assign these users to your ThousandEyes app by following the instructions here:
Assign a user or group to an enterprise app
Important tips for assigning users to ThousandEyes
It's recommended that a single Microsoft Entra user is assigned to ThousandEyes to test the provisioning configuration. More users and/or groups may be assigned later.
When assigning a user to ThousandEyes, you must select either the User role, or another valid application-specific role (if available) in the assignment dialog. The Default Access role doesn't work for provisioning, and these users are skipped.
Configuring user provisioning to ThousandEyes
This section guides you through connecting your Microsoft Entra ID to ThousandEyes's user account provisioning API, and configuring the provisioning service to create, update, and disable assigned user accounts in ThousandEyes based on user and group assignment in Microsoft Entra ID.
Tip
You may also choose to enabled SAML-based Single Sign-On for ThousandEyes, following the instructions provided in the Azure portal. Single sign-on can be configured independently of automatic provisioning, though these two features complement each other.
Configure automatic user account provisioning to ThousandEyes in Microsoft Entra ID
Sign in to the Microsoft Entra admin center as at least a Cloud Application Administrator.
Browse to Identity > Applications > Enterprise applications
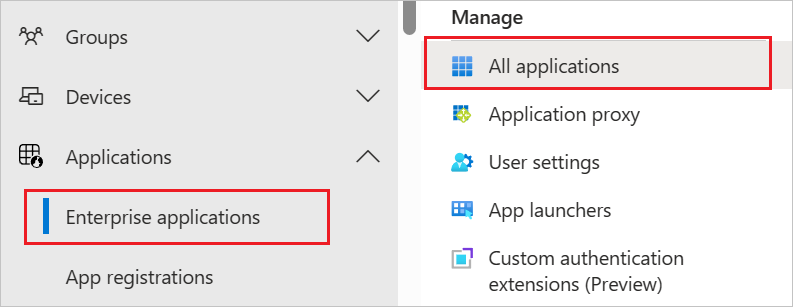
If you have already configured ThousandEyes for single sign-on, search for your instance of ThousandEyes using the search field. Otherwise, select Add and search for ThousandEyes in the application gallery. Select ThousandEyes from the search results, and add it to your list of applications.
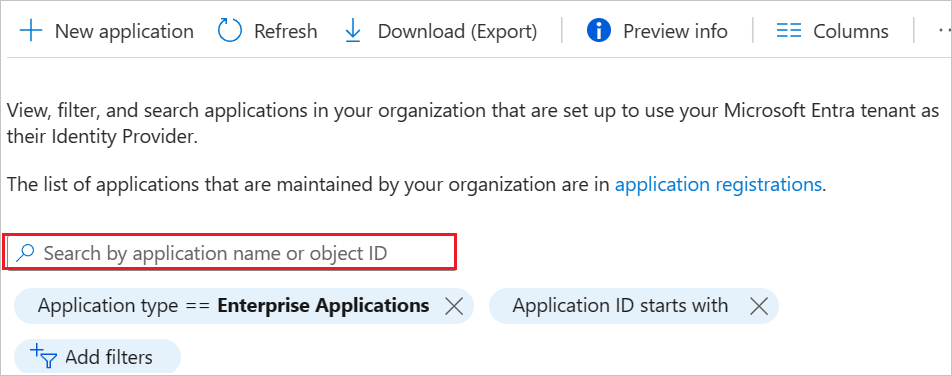
Select your instance of ThousandEyes, then select the Provisioning tab.
Set the Provisioning Mode to Automatic.

Under the Admin Credentials section, input the OAuth Bearer Token generated by your ThousandEyes's account (you can find and or generate a token under your ThousandEyes account Profile section).

Select Test Connection to ensure Microsoft Entra ID can connect to your ThousandEyes app. If the connection fails, ensure your ThousandEyes account has Admin permissions and try step 5 again.
In the Notification Email field, enter the email address of a person or group who should receive the provisioning error notifications and select the Send an email notification when a failure occurs check box.
Click Save.
Under the Mappings section, select Synchronize Microsoft Entra users to ThousandEyes.
Review the user attributes that are synchronized from Microsoft Entra ID to ThousandEyes in the Attribute-Mapping section. The attributes selected as Matching properties are used to match the user accounts in Parsable for update operations. If you choose to change the matching target attribute, you need to ensure that the Parsable API supports filtering users based on that attribute. Select the Save button to commit any changes.
Attribute Type Supported for filtering externalId String ✓ userName String ✓ active Boolean displayName String emails[type eq "work"].value String name.formatted String To configure scoping filters, refer to the following instructions provided in the Scoping filter tutorial.
To enable the Microsoft Entra provisioning service for ThousandEyes, change the Provisioning Status to On in the Settings section.

Define the users and/or groups that you would like to provision to ThousandEyes by choosing the desired values in Scope in the Settings section.
When you're ready to provision, click Save.

This operation starts the initial synchronization cycle of all users and groups defined in Scope in the Settings section. The initial cycle takes longer to perform than subsequent cycles, which occur approximately every 40 minutes as long as the Microsoft Entra provisioning service is running.
Step 6: Monitor your deployment
Once you've configured provisioning, use the following resources to monitor your deployment:
- Use the provisioning logs to determine which users have been provisioned successfully or unsuccessfully
- Check the progress bar to see the status of the provisioning cycle and how close it is to completion
- If the provisioning configuration seems to be in an unhealthy state, the application goes into quarantine. Learn more about quarantine states here.
Additional resources
- Managing user account provisioning for Enterprise Apps
- What is application access and single sign-on with Microsoft Entra ID?