Overview of service encryption with Microsoft Purview Customer Key
Microsoft 365 provides baseline, volume-level encryption enabled through BitLocker and Distributed Key Manager (DKM). Windows 365 Enterprise and Business Cloud PC disks are encrypted with Azure Storage server-side encryption (SSE). Microsoft 365 offers an added layer of encryption for your content through Customer Key. This content includes data from Exchange Online, Microsoft SharePoint, Microsoft OneDrive, Microsoft Teams, and Windows 365 Cloud PCs.
BitLocker isn't supported as an encryption option for Windows 365 Cloud PCs. For more information, see Using Windows 10 virtual machines in Intune.
Tip
If you're not an E5 customer, use the 90-day Microsoft Purview solutions trial to explore how additional Purview capabilities can help your organization manage data security and compliance needs. Start now at the Microsoft Purview compliance portal trials hub. Learn details about signing up and trial terms.
How service encryption, BitLocker, SSE, and Customer Key work together
Your Microsoft 365 data is always encrypted at rest in the Microsoft 365 service with BitLocker and DKM. For more information, see How Exchange Online secures your email secrets. Customer Key provides extra protection against viewing of data by unauthorized systems or personnel, and complements BitLocker disk encryption and SSE in Microsoft data centers. Service encryption isn't meant to prevent Microsoft personnel from accessing your data. Instead, Customer Key helps you meet regulatory or compliance obligations for controlling root keys. You explicitly authorize Microsoft 365 services to use your encryption keys to provide value added cloud services, such as eDiscovery, anti-malware, anti-spam, search indexing, and so on.
Customer Key is built on service encryption and lets you provide and control encryption keys. Microsoft 365 then uses these keys to encrypt your data at rest as described in the Online Services Terms (OST). Customer Key helps you meet compliance obligations because you control the encryption keys that Microsoft 365 uses to encrypt and decrypt data.
Customer Key enhances the ability of your organization to meet the demands of compliance requirements that specify key arrangements with the cloud service provider. With Customer Key, you provide and control the root encryption keys for your Microsoft 365 data at-rest at the application level. As a result, you exercise control over your organization's keys.
Customer Key with hybrid deployments
Customer Key only encrypts data at rest in the cloud. Customer Key doesn't work to protect your on-premises mailboxes and files. You can encrypt your on-premises data using another method, such as BitLocker.
Learn about data encryption policies
A data encryption policy (DEP) defines the encryption hierarchy. This hierarchy is used by the service to encrypt data using each of the keys you manage and the availability key that's protected by Microsoft. You create a DEP using PowerShell cmdlets, and then assign a DEP to encrypt application data. There are three types of data encryption policies (DEPs) supported by Customer Key. Each policy type uses different cmdlets and provides coverage for a different type of data. You can define these types:
DEP for multiple Microsoft 365 workloads These DEPs encrypt data across multiple Microsoft 365 workloads for all users within the tenant. These workloads include:
Windows 365 Cloud PCs. For more information, see Microsoft Purview Customer Key for Windows 365 Cloud PCs
Teams chat messages (1:1 chats, group chats, meeting chats and channel conversations)
Teams media messages (images, code snippets, video messages, audio messages, wiki images)
Teams call and meeting recordings stored in Teams storage
Teams chat notifications
Teams chat suggestions by Cortana
Teams status messages
Microsoft 365 Copilot interactions
User and signal information for Exchange Online
Exchange Online mailboxes without encryption applied from a mailbox DEP
Microsoft Purview Information Protection:
Exact data match (EDM) data, including data file schemas, rule packages, and the salts used to hash the sensitive data. For EDM and Microsoft Teams, the multi-workload DEP encrypts new data from the time you assign the DEP to the tenant. For Exchange Online, Customer Key encrypts all existing and new data.
Label configuration for sensitivity labels
Multi-workload DEPs don't encrypt the following types of data. Instead, Microsoft 365 uses other types of encryption to protect this data.
- SharePoint and OneDrive data.
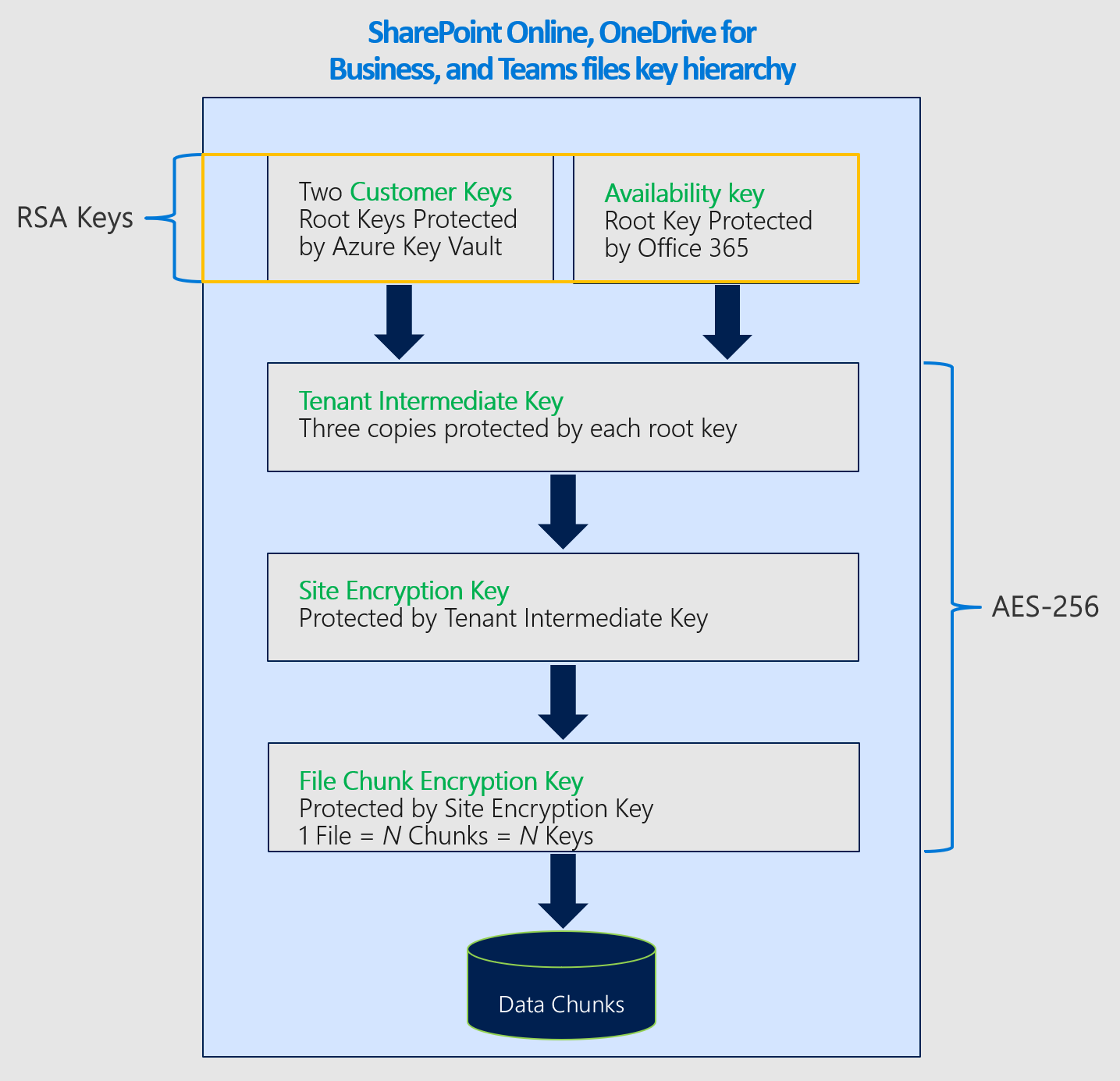
- Microsoft Teams files and some Teams call and meeting recordings saved in OneDrive and SharePoint are encrypted using the SharePoint DEP.
- Other Microsoft 365 workloads that Customer Key doesn't support, such as Viva Engage and Planner.
- Teams Live Event data.
You can create multiple DEPs per tenant but only assign one DEP at a time. When you assign the DEP, encryption begins automatically but takes some time to complete depending on the size of your tenant.
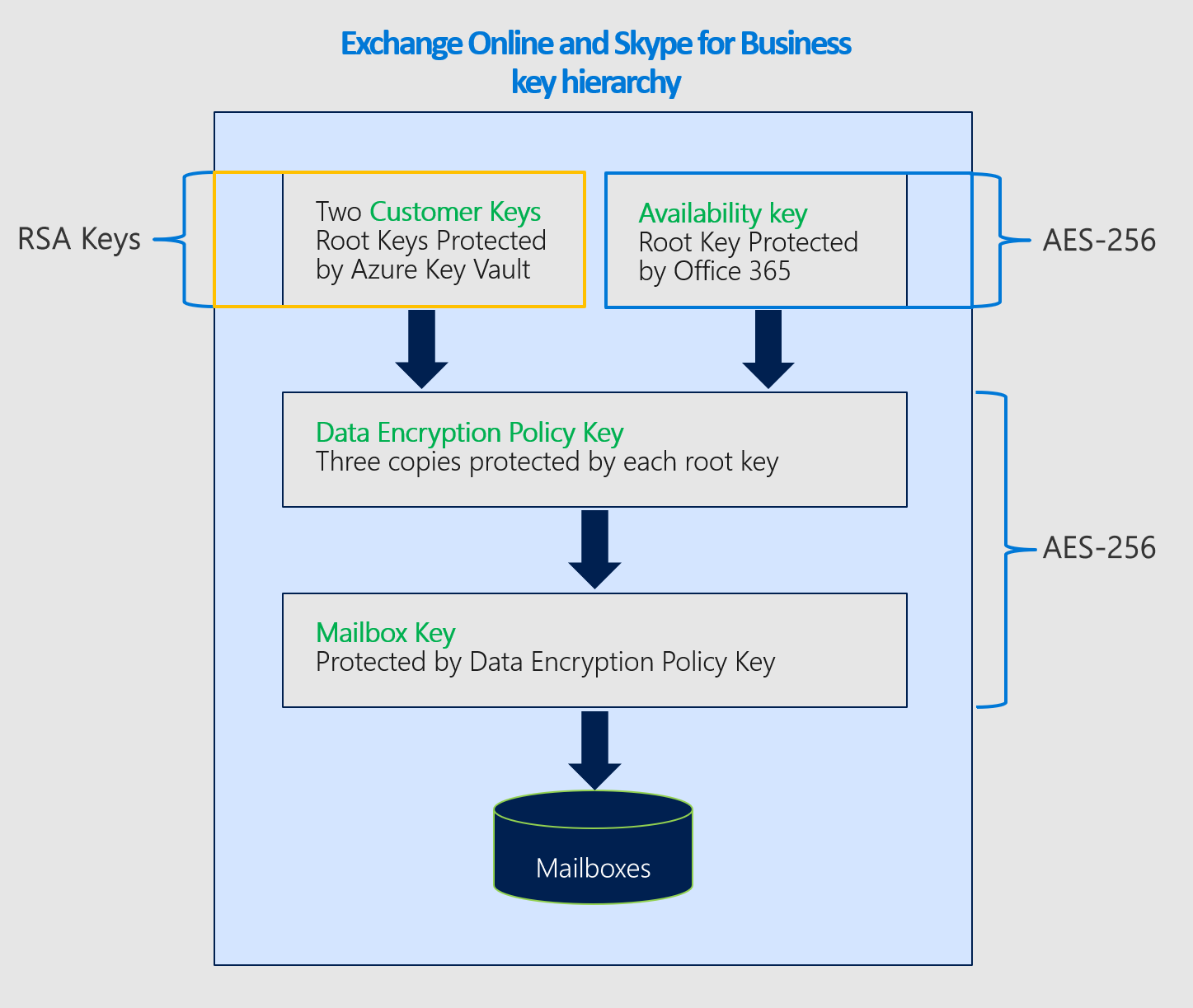
DEPs for Exchange Online mailboxes Mailbox DEPs provide more precise control over individual mailboxes within Exchange Online. Use mailbox DEPs to encrypt data stored in EXO mailboxes of different types such as UserMailbox, MailUser, Group, PublicFolder, and Shared mailboxes. You can have up to 50 active DEPs per tenant and assign those DEPs to individual mailboxes. You can assign one DEP to multiple mailboxes.
By default your mailboxes get encrypted using Microsoft-managed keys. When you assign a Customer Key DEP to a mailbox:
If the mailbox is encrypted using a multi-workload DEP, the service rewraps the mailbox using the new mailbox DEP as long as a user or a system operation accesses the mailbox data.
If the mailbox is already encrypted using Microsoft-managed keys, the service rewraps the mailbox using the new mailbox DEP as long as a user or a system operation accesses the mailbox data.
If the mailbox isn't yet encrypted using default encryption, then the service marks the mailbox for a move. The encryption takes place once the move is complete. Mailbox moves are governed based on priorities set for all of Microsoft 365. For more information, see, Move requests in the Microsoft 365 service. If the mailboxes aren't encrypted within the specified time, contact Microsoft.
Later, you can either refresh the DEP or assign a different DEP to the mailbox as described in Manage Customer Key for Office 365. Each mailbox must have appropriate licenses to be assigned a DEP. For more information about licensing, see Before you set up Customer Key.
You can assign DEPs to a shared mailbox, public folder mailbox, and Microsoft 365 group mailbox for tenants that meet the licensing requirement for user mailboxes. You don't need separate licenses for non-user-specific mailboxes to assign Customer Key DEP.
For Customer Key DEPs that you assign to individual mailboxes, you can request that Microsoft purge specific DEPs when you leave the service. For information about the data purge process and key revocation, see Revoke your keys and start the data purge path process.
When you revoke access to your keys as part of leaving the service, the availability key is deleted, resulting in cryptographic deletion of your data. Cryptographic deletion mitigates the risk of data remanence, which is important for meeting both security and compliance obligations.
DEP for SharePoint and OneDrive This DEP is used to encrypt content stored in SharePoint and OneDrive, including Microsoft Teams files stored in SharePoint. If you're using the multi-geo feature, you can create one DEP per geo for your organization. If you're not using the multi-geo feature, you can only create one DEP per tenant. Refer to the details in Set up Customer Key.
Encryption ciphers used by Customer Key
Customer Key uses various encryption ciphers to encrypt keys as shown in the following figures.
The key hierarchy used for DEPs that encrypt data for multiple Microsoft 365 workloads is similar to the hierarchy used for DEPs for individual Exchange Online mailboxes. The only difference is that the Mailbox Key is replaced with the corresponding Microsoft 365 Workload Key.
Encryption ciphers used to encrypt keys for Exchange Online
Encryption ciphers used to encrypt keys for SharePoint and OneDrive