Access Key Vault secret when deploying Azure Managed Applications
When you need to pass a secure value (like a password) as a parameter during deployment, you can retrieve the value from an Azure Key Vault. To access the Key Vault when deploying Managed Applications, you must grant access to the Appliance Resource Provider service principal. The Managed Applications service uses this identity to run operations. To successfully retrieve a value from a Key Vault during deployment, the service principal must be able to access the Key Vault.
This article describes how to configure the Key Vault to work with Managed Applications.
Enable template deployment
Sign in to the Azure portal.
Open your key vault. Enter key vaults in the search box or select Key vaults.
Select Access configuration.
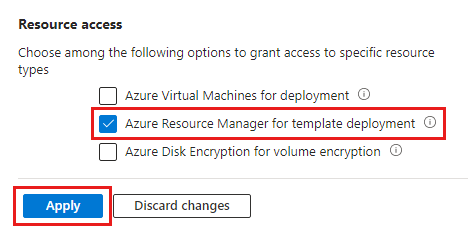
Select Azure Resource Manager for template deployment. Then, select Apply.
Add service as contributor
Assign the Contributor role to the Appliance Resource Provider user at the key vault scope. The Contributor role is a privileged administrator role for the role assignment. For detailed steps, go to Assign Azure roles using the Azure portal.
The Appliance Resource Provider is a service principal in your Microsoft Entra tenant. From the Azure portal, you can verify its registration at Microsoft Entra ID > Enterprise applications and change the search filter to Microsoft Applications. Search for Appliance Resource Provider. If the service principal isn't found, register the Microsoft.Solutions resource provider.
Reference Key Vault secret
To pass a secret from a Key Vault to a template in your Managed Application, you must use a linked or nested template and reference the Key Vault in the parameters for the linked or nested template. Provide the resource ID of the Key Vault and the name of the secret.
{
"$schema": "https://schema.management.azure.com/schemas/2019-04-01/deploymentTemplate.json#",
"contentVersion": "1.0.0.0",
"parameters": {
"location": {
"type": "string",
"defaultValue": "[resourceGroup().location]",
"metadata": {
"description": "The location where the resources will be deployed."
}
},
"vaultName": {
"type": "string",
"metadata": {
"description": "The name of the key vault that contains the secret."
}
},
"secretName": {
"type": "string",
"metadata": {
"description": "The name of the secret."
}
},
"vaultResourceGroupName": {
"type": "string",
"metadata": {
"description": "The name of the resource group that contains the key vault."
}
},
"vaultSubscription": {
"type": "string",
"defaultValue": "[subscription().subscriptionId]",
"metadata": {
"description": "The name of the subscription that contains the key vault."
}
}
},
"resources": [
{
"type": "Microsoft.Resources/deployments",
"apiVersion": "2022-09-01",
"name": "dynamicSecret",
"properties": {
"mode": "Incremental",
"expressionEvaluationOptions": {
"scope": "inner"
},
"template": {
"$schema": "https://schema.management.azure.com/schemas/2019-04-01/deploymentTemplate.json#",
"contentVersion": "1.0.0.0",
"parameters": {
"adminLogin": {
"type": "string"
},
"adminPassword": {
"type": "securestring"
},
"location": {
"type": "string"
}
},
"variables": {
"sqlServerName": "[concat('sql-', uniqueString(resourceGroup().id, 'sql'))]"
},
"resources": [
{
"type": "Microsoft.Sql/servers",
"apiVersion": "2022-05-01-preview",
"name": "[variables('sqlServerName')]",
"location": "[parameters('location')]",
"properties": {
"administratorLogin": "[parameters('adminLogin')]",
"administratorLoginPassword": "[parameters('adminPassword')]"
}
}
],
"outputs": {
"sqlFQDN": {
"type": "string",
"value": "[reference(variables('sqlServerName')).fullyQualifiedDomainName]"
}
}
},
"parameters": {
"location": {
"value": "[parameters('location')]"
},
"adminLogin": {
"value": "ghuser"
},
"adminPassword": {
"reference": {
"keyVault": {
"id": "[resourceId(parameters('vaultSubscription'), parameters('vaultResourceGroupName'), 'Microsoft.KeyVault/vaults', parameters('vaultName'))]"
},
"secretName": "[parameters('secretName')]"
}
}
}
}
}
],
"outputs": {
}
}
Next steps
You configured your Key Vault to be accessible during deployment of a Managed Application.
- For information about passing a value from a Key Vault as a template parameter, go to Use Azure Key Vault to pass secure parameter value during deployment.
- To learn more about key vault security, go to Azure Key Vault security and Authentication in Azure Key Vault.
- For managed application examples, go to Sample projects for Azure managed applications.
- To learn how to create a UI definition file for a managed application, go to Get started with CreateUiDefinition.