Merk
Tilgang til denne siden krever autorisasjon. Du kan prøve å logge på eller endre kataloger.
Tilgang til denne siden krever autorisasjon. Du kan prøve å endre kataloger.
GitHub Enterprise Cloud er en tjeneste som hjelper organisasjoner med å lagre og administrere koden, i tillegg til å spore og kontrollere endringer i koden. I tillegg til fordelene med å bygge og skalere koderepositorier i skyen, kan organisasjonens mest kritiske ressurser bli utsatt for trusler. Eksponerte ressurser inkluderer repositorier med potensielt sensitiv informasjon, samarbeids- og partnerskapsdetaljer og mer. Forebygging av eksponering av disse dataene krever kontinuerlig overvåking for å hindre at skadelige aktører eller sikkerhetsindikere fra å eksfiltrere sensitiv informasjon.
Å koble GitHub Enterprise Cloud til Defender for Cloud Apps gir deg forbedret innsikt i brukernes aktiviteter og gir trusselregistrering for uregelmessig atferd.
Bruk denne appkoblingen til å få tilgang til SSPM-funksjoner (SaaS Security Posture Management), via sikkerhetskontroller som gjenspeiles i Microsoft Secure Score. Finn ut mer.
Hovedtrusler
- Kompromitterte kontoer og insider-trusler
- Datalekkasje
- Utilstrekkelig sikkerhetsbevissthet
- Uadministrert ta med din egen enhet (BYOD)
Slik bidrar Defender for Cloud Apps til å beskytte miljøet ditt
- Oppdage skytrusler, kompromitterte kontoer og ondsinnede innsidere
- Bruk revisjonssporet for aktiviteter for rettsmedisinske undersøkelser
SaaS sikkerhet holdning ledelse
Hvis du vil se anbefalinger for sikkerhetsstilling for GitHub i Microsoft Secure Score, kan du opprette en API-kobling via Koblinger-fanen med eier- og enterprise-tillatelser . Velg Anbefalte handlinger i Sikker poengsum, og filtrer etterProdukt-GitHub = .
Anbefalinger for GitHub inkluderer for eksempel:
- Aktiver godkjenning med flere faktorer (MFA)
- Aktiver enkel pålogging (SSO)
- Deaktiver Tillat medlemmer å endre repositorium visibilities for denne organisasjonen
- Deaktiver «medlemmer med administratortillatelser for repositorier kan slette eller overføre repositorier»
Hvis det allerede finnes en kobling, og du ikke ser GitHub-anbefalinger ennå, kan du oppdatere tilkoblingen ved å koble fra API-koblingen og deretter koble den til eier- og enterprise-tillatelsene på nytt.
Hvis du vil ha mer informasjon, kan du se:
Beskytt GitHub i sanntid
Se gjennom våre anbefalte fremgangsmåter for å sikre og samarbeide med gjester.
Koble GitHub Enterprise Cloud til Microsoft Defender for Cloud Apps
Denne delen inneholder instruksjoner for hvordan du kobler Microsoft Defender for Cloud Apps til den eksisterende GitHub Enterprise Cloud-organisasjonen ved hjelp av API-ene for App Connector. Denne tilkoblingen gir deg innsyn i og kontroll over organisasjonens GitHub Enterprise Cloud-bruk. Hvis du vil ha mer informasjon om hvordan Defender for Cloud Apps beskytter GitHub Enterprise Cloud, kan du se Beskytt GitHub Enterprise.
Bruk denne appkoblingen til å få tilgang til SSPM-funksjoner (SaaS Security Posture Management), via sikkerhetskontroller som gjenspeiles i Microsoft Secure Score. Finn ut mer.
Forutsetninger
- Organisasjonen må ha en GitHub Enterprise Cloud-lisens .
- GitHub-kontoen som brukes til å koble til Defender for Cloud Apps, må ha eiertillatelser for organisasjonen.
- For SSPM-funksjoner må den angitte kontoen være eieren av bedriftskontoen.
- Hvis du vil bekrefte eierne av organisasjonen, kan du gå til organisasjonens side, velge Folk og deretter filtrere etter eier.
Bekreft GitHub-domenene dine
Det er valgfritt å bekrefte domenene. Vi anbefaler at du bekrefter domenene slik at Defender for Cloud Apps kan samsvare med domene-e-postmeldingene til GitHub-organisasjonens medlemmer til deres tilsvarende Azure Active Directory-bruker.
Disse trinnene er uavhengige av trinnene i Konfigurer GitHub Enterprise Cloud og kan hoppes over hvis domenene dine allerede er bekreftet.
Oppgrader organisasjonen til bedriftens vilkår for bruk.
Bekreft organisasjonens domener.
Obs!
Pass på å bekrefte hvert av de administrerte domenene som er oppført i innstillingene for Defender for Cloud Apps. Administrerte domener er oppført i Microsoft Defender Portal under Innstillinger>Cloud Apps>System>Organizational Detaljer>Administrerte domener.
Konfigurer GitHub Enterprise Cloud
Kopier organisasjonens påloggingsnavn. Du vil trenge det senere.
Obs!
Siden har en URL-adresse som
https://github.com/<your-organization>. Hvis for eksempel organisasjonens side erhttps://github.com/sample-organization, er organisasjonens påloggingsnavn eksempelorganisasjon.Opprett en OAuth-app for Defender for Cloud Apps for å koble til GitHub-organisasjonen.
Fyll ut detaljene for Registrer en ny OAuth-app , og velg deretter Registrer program.
- Skriv inn et navn på appen i programnavnboksen .
- Skriv inn nettadressen for appens hjemmeside i nettadresseboksen for hjemmesiden for hjemmesiden for appen.
- Skriv inn følgende verdi i boksen URL-adresse for tilbakeringing av autorisasjon :
https://portal.cloudappsecurity.com/api/oauth/connect.
Obs!
Angi følgende verdi for US Government GCC-kunder:
https://portal.cloudappsecuritygov.com/api/oauth/connectFor US Government GCC High-kunder angir du følgende verdi:
https://portal.cloudappsecurity.us/api/oauth/connectApper som eies av en organisasjon, har tilgang til organisasjonens apper. Hvis du vil ha mer informasjon, kan du se Om tilgangsbegrensninger for OAuth App.
Velg OAuth-appen du opprettet, og kopier klient-ID-en og klienthemmeligheten.
Konfigurer Defender for Cloud Apps
Velg Innstillinger i Microsoft Defender-portalen. Velg deretter Skyapper. Velg Appkoblinger under Tilkoblede apper.
Velg +Koble til en app, etterfulgt av GitHub, på appkoblingssiden.
Gi koblingen et beskrivende navn i neste vindu, og velg deretter Neste.
Fyll ut navnet på klient-ID-en, klienthemmeligheten og organisasjonspåloggingen som du noterte deg tidligere, i vinduet Skriv inn detaljer.
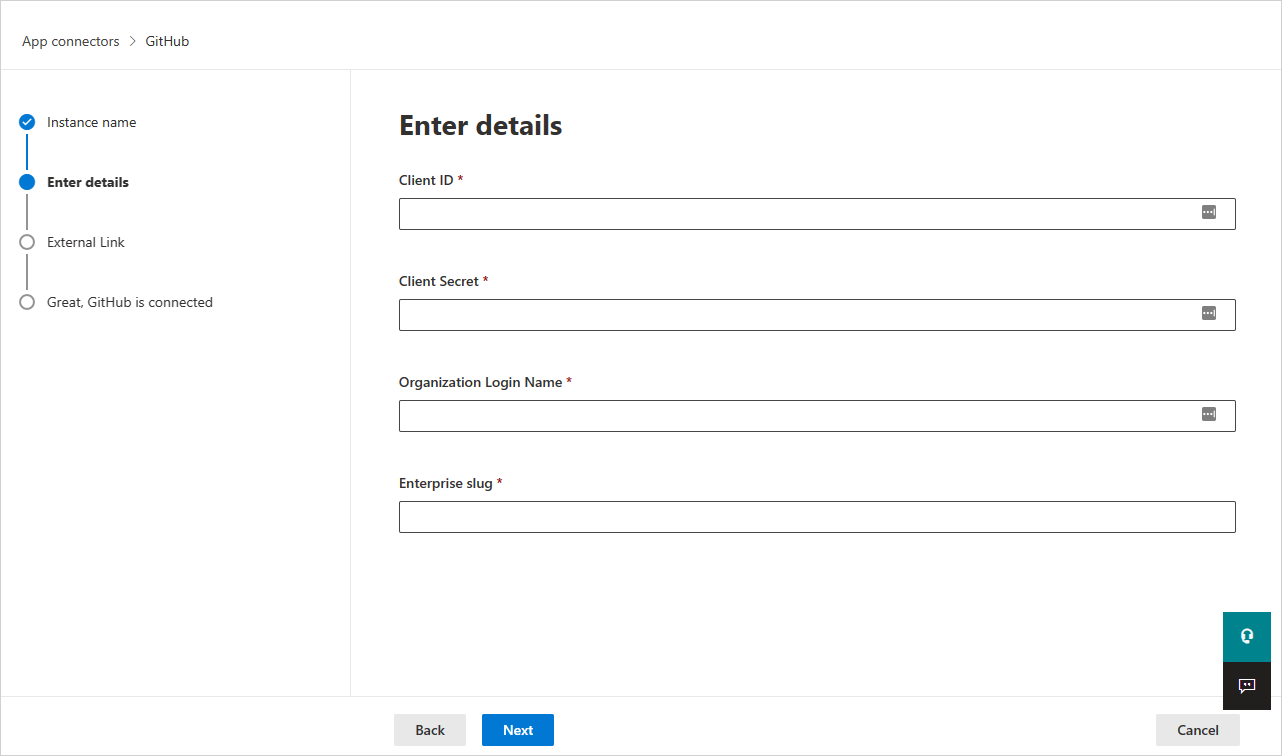
Enterprise-slugen, også kjent som virksomhetsnavnet, er nødvendig for å støtte SSPM-funksjoner. Slik finner du Enterprise-slugen:
- Velg GitHub-profilbildet –>bedriftene dine.
- Velg bedriftskontoen, og velg kontoen du vil koble til Microsoft Defender for Cloud Apps.
- Bekreft at URL-adressen inneholder virksomhetssneglen. For eksempel
https://github.com/enterprises/testEnterprise - Skriv bare inn virksomhetssneglen, ikke hele nettadressen. I dette eksemplet er testEnterprise virksomhetssneglen.
Velg Koble til GitHub.
Hvis det er nødvendig, angir du legitimasjonen for GitHub-administratoren for å gi Defender for Cloud Apps tilgang til teamets GitHub Enterprise Cloud-forekomst.
Be organisasjonen om tilgang og godkjenn appen for å gi Defender for Cloud Apps tilgang til GitHub-organisasjonen. Defender for Cloud Apps krever følgende OAuth-omfang:
- admin:org – kreves for å synkronisere organisasjonens overvåkingslogg
- les:bruker og bruker:e-post – kreves for å synkronisere organisasjonens medlemmer
- repo:status – obligatorisk for synkronisering av repositoriumrelaterte hendelser i overvåkingsloggen
- read:enterprise – obligatorisk for SSPM-funksjoner. Den angitte brukeren må være eier av virksomhetskontoen.
Hvis du vil ha mer informasjon om OAuth-omfang, kan du se Forstå omfang for OAuth-apper.
Tilbake i Defender for Cloud Apps-konsollen skal du motta en melding om at GitHub var koblet til.
Samarbeid med eieren av GitHub-organisasjonen for å gi organisasjonen tilgang til OAuth-appen som er opprettet under tilgangsinnstillingene for Tredjeparter i GitHub. Hvis du vil ha mer informasjon, kan du se GitHub-dokumentasjon.
Eieren av organisasjonen finner forespørselen fra OAuth-appen bare etter å ha koblet GitHub til Defender for Cloud Apps.
Velg Innstillinger i Microsoft Defender-portalen. Velg deretter Skyapper. Velg Appkoblinger under Tilkoblede apper. Kontroller at statusen for den tilkoblede App Connector er tilkoblet.
Når du har koblet til GitHub Enterprise Cloud, mottar du hendelser i sju dager før tilkoblingen.
Neste trinn
Hvis du har problemer med å koble til appen, kan du se Feilsøke appkoblinger.