Kerberos Delegation
Kerberos Delegation is a feature that allows an application to reuse the end-user credentials to access recourses hosted on a different server. You should only allow that if you really trust the application server, otherwise the application may use your credentials to purposes that you didn't think of, like sending e-mails on your behalf or changing data in a mission critical application pretending that you made that change.
For that reason, delegation is not enabled by default in Active Directory. You - or more likely the domain administrator - must explicit make the decision that this particular application is trusted for delegation. This is also a partial answer to the quiz in the previous post: no, the list of task was not sufficient to satisfy the business requirements because the list did not include any task related to Kerberos delegation.
The Kerberos Delegation is configured as a property for the domain account that is used by the application as a service account. For an IIS application that is the application pool account configured for that particular application. That is the also the same domain account that you used when you configured the SPN.
Kerberos Delegation comes in different flavors. The first implementation of Kerberos delegation that was introduced in Windows 2000 was an all or nothing implementation: you allowed that the domain account could use your credentials to connect to any server in the world. (Or more exactly at least any server that were reachable in the current Domain, the current Forrest or any domain in any forest with a forest trust).
When you are configuring Active Directory in Windows Server 2003, the default Domain Functional Level is Windows 2000 mixed mode. In that mode, the configuration of delegation is different for a computer account (Local System) compared to a user account.
To configure the delegation for a Local System account, put a check mark in "Trust computer for delegation" on the General tab page.
For user account, you must put a checkmark on the "Account is trusted for delegation" option on the Account tab for the account.
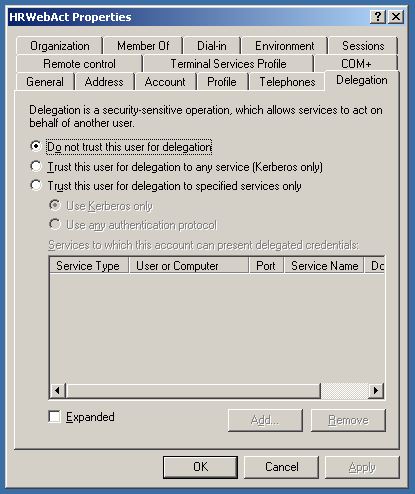
If you have raised the Domain Functional level to Windows Server 2003, the Delegation property is moved for both computer accounts and user accounts to a dedicated tab page "Delegation" and you are also giving more options to control the scope of the delegation. I will come back to constrained delegation in a future post.
The delegation tab is only visible on the user account when you have created a SPN for that account.
As mentioned, the delegation was only a partial answer to the question from the last post. In addition to that, you must also configure Kernel mode authentication in IIS 7.x. That is a topic for my next post.