Windows 2012 Core Survival Guide – PowerShell Remote Management
Learn about my 2012 Core Survival Guide here.
PowerShell Remote Management
Windows Server 2012 has PowerShell remoting enabled by default. In order to manage PowerShell Remote Management correctly you will need to logon with an account that is a member of the local administrators account.
How to determine if remoting is configured correctly
You can determine if remoting is configured by creating a new PowerShell session. If the session is created successfully then remoting is configured correctly. The cmdlet we use to create a new PowerShell session is New-PSSession.
PowerShell Command:
New-PSSession
In the screen shot below remoting is configured correctly.
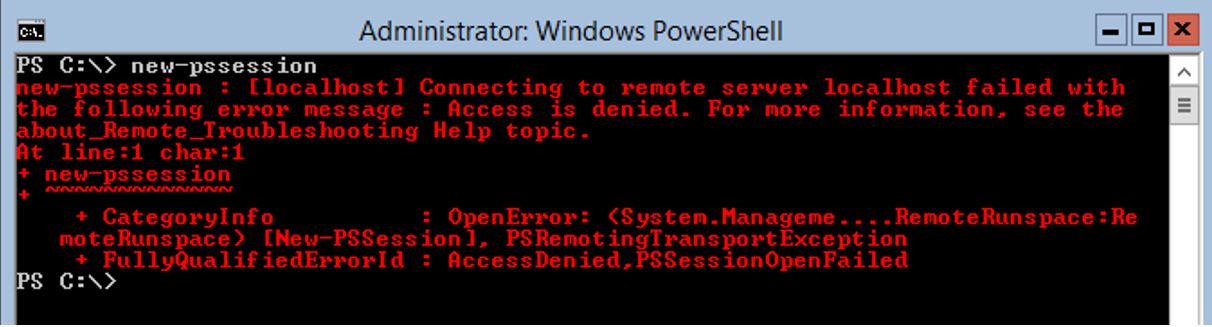
In the screen shot below remoting is not configured correctly. This is just one of the possible errors depending on what is not configured correctly.
How to enable remote management
The Scripting Guy wrote a good blog on remoting so I will share the link with you. No reason to recreate the wheel.
There is a simple PowerShell cmdlet (Enable-PSRemoting) to enable remoting. This command does the following:
- Starting or restarting the WinRM Service
- Setting the WinRM service to startup type to Automatic
- Creating a listener to accept requests on any IP address
- Enabling Windows Firewall inbounds rules exceptions for wm-management traffic
PowerShell Command:
Enable-PSRemoting
Below you can see it quite simple.
How to disable remote management
By default on Windows Server 2012 remote management is enabled. It is NOT a best practice to disable this setting. With that said this is how it can be done. It will requires several steps to complete.
PowerShell Command:
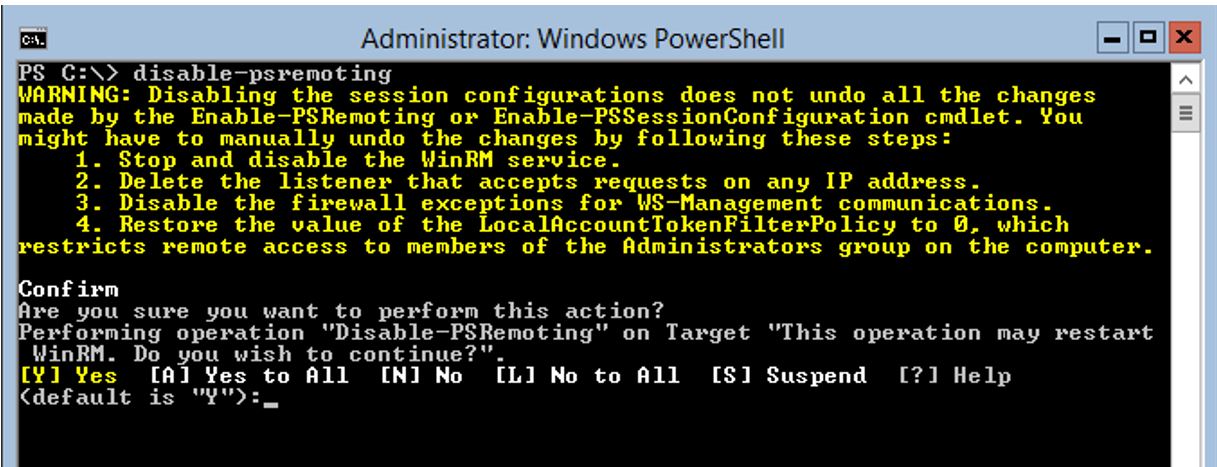
Disable-PSRemoting
To stop the WinRM service use the following command
Stop-Service -name WinRM
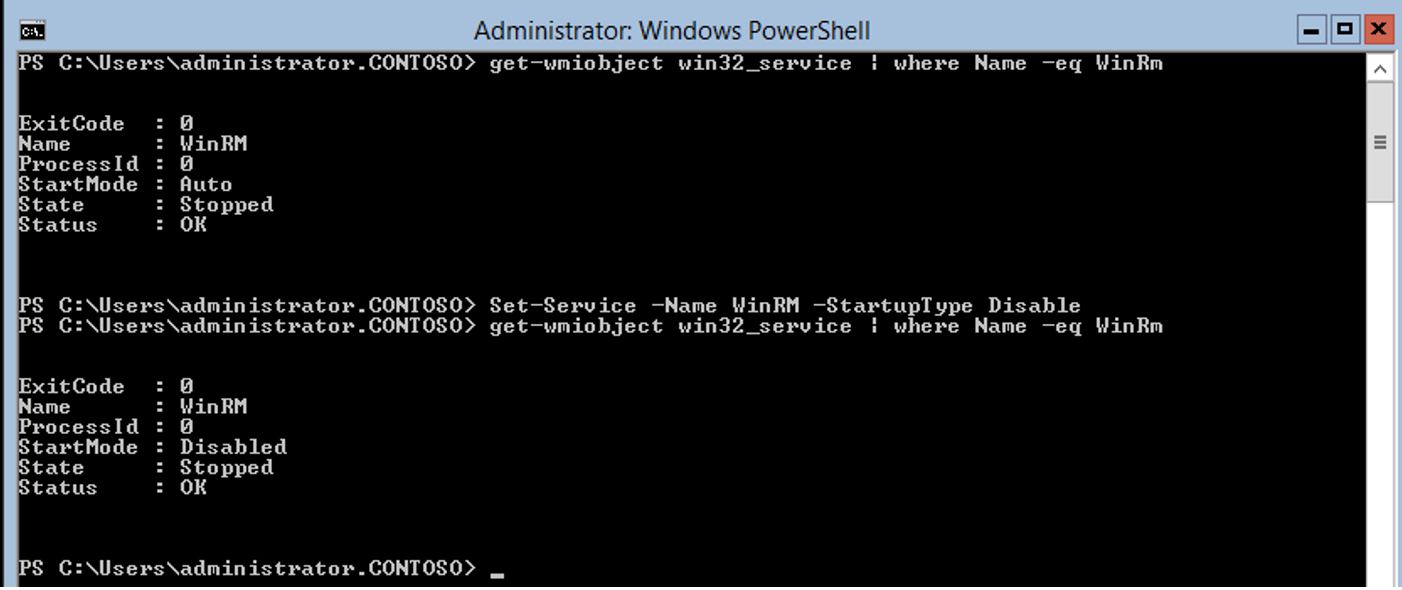
How to disable the WinRM service
Set-Service -Name WinRM -StartupType Disable
To restore the value of LocalAccountTokenFilterPolicy to zero use the following:
PowerShell Command:
set-ItemProperty -Path "HKLM:\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system" -name "LocalAccountTokenFilterPolicy" -Value 0
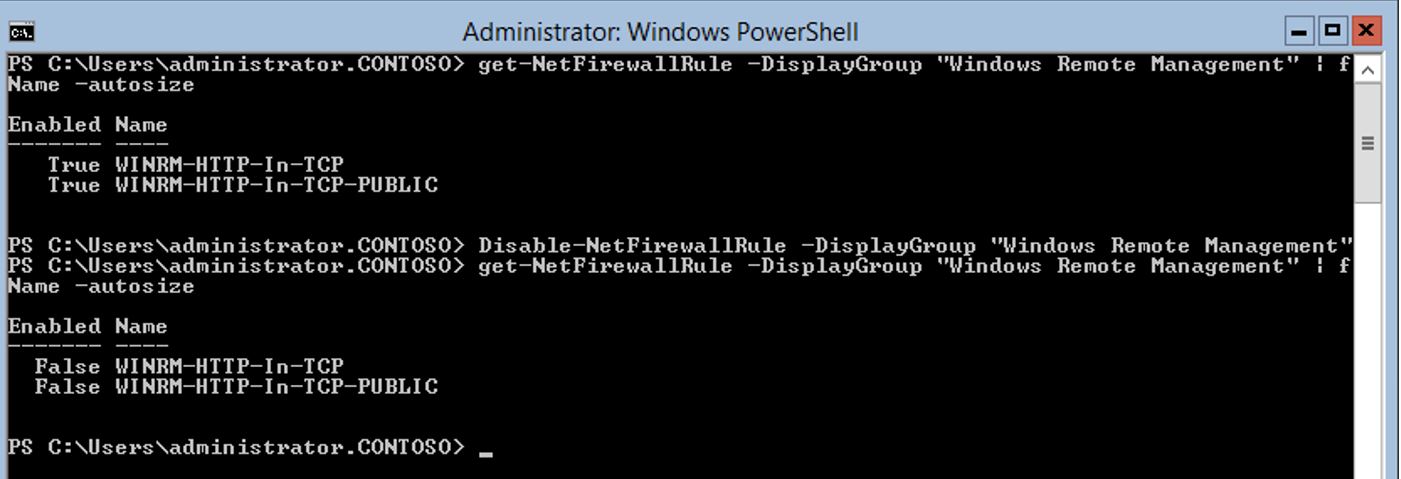
To disable the Windows Remote Management firewall rules use the following:
PowerShell Command:
Enable-NetFirewallRule -DisplayGroup "Windows Remote Management"
I hope you found this useful. Please leave me a comment
Bruce
Comments
- Anonymous
December 23, 2013
Pingback from How to Setting up Hyper-V server 2012 R2 on workgroup | Luca's Space - Anonymous
December 23, 2013
Pingback from How to Setting up Hyper-V server 2012 R2 on workgroup | Luca's Space - Anonymous
December 23, 2013
Pingback from How to Setting up Hyper-V server 2012 R2 on workgroup | Luca's Space - Anonymous
February 24, 2014
The correct command to disable the Windows Remote Management firewall rules is Disable-NetFirewallRule -DisplayGroup "Windows Remote Management" as you can see from relative image.
Regards