Access Control Service Sample
Microsoft .NET Services are part of the Azure Services Platform. The Microsoft .NET Access Control Service provides an easy way to control web applications and services while integrating with standards-based identity providers, including enterprise directories and web identity systems such as Windows Live ID.
ACS is currently available as a CTP. The CTP provides federation with Live IDs and is the easiest way I've found to integrate Live ID into a web site. Even though there are some CTP maturity issues, you can still do quite a lot with the CTP and we are very excited about the direction ACS is headed. While investigating ACS for RXG, I put together a simple example that shows how to integrate ACS into a web app. The Visual Studio 2008 sample code is available below. Many thanks to Justin for providing most of the code and answering my questions.
Before you download the code ...
There are a couple of things you need to do in order to get the sample to work. The first is to register for the .NET Services CTP, install the SDKs, and setup a .NET Services solution. You will also need to install the Geneva beta.
Next, go to the portal and setup ACS by signing in then clicking on Getting Started then "Access Control Service" on the getting started page.
Once on the ACS page, click the Basic button.
On the Basic View page, click the Next button
On the Wizard page, enter https://localhost into the Application URL field, leave the certificate field blank, and click next. In a production app, you would want to supply a certificate for security reasons.
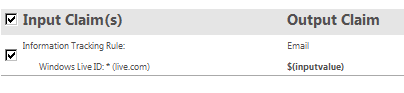
On the Access Control Rules page, change the type of the claim to Windows Live ID. Enter an * in the value field and change the issuer to live.com. Change the output claim type to e-mail, check the copy input value box, and click save.
You should end up on the Rules page with a single rule that looks like this:
Download the sample code from here, unzip, and open the solution. Make sure to stop IIS if it’s running as the sample requires port 80 on localhost.
Open web.config and change the [[solution]] value in the Issuer url to the correct solution name (it’s displayed on the ACS portal pages).
Open global.asax.cs and set a breakpoint in the Application_AuthenticateRequest event.
Press F5 and you will hit the breakpoint. Press F5 again time and the default page will load.
Click on the Page 2 link and you will be redirected to the live.com login page. After logging in with a valid Live ID, you should see your authentication information on the default page. Click on the Page 2 link again and you should be taken to Page2.aspx.
What just happened?
The Application_AuthenticateRequest event redirects to live.com to get the token which is automatically handled by the Geneva provider. The rediretion code in the AuthenticateRequest event is exactly the same as the code in the btnFederate_Click event. The code is very simple as it just gets a reference to the WSFederationAuthenticationModule in ApplicationInstance.Modules, creates a SignInRequestMessage, then redirects.
Geneva is configured with the <microsoft.identityModel> section in web.config. As mentioned above, make sure to modify the issuer value to point to your solution. Also note that authentication mode is set to None. Most of the Geneva magic happens because of the web.config values. I still don't fully understand all of the options, but the basics make sense once you play around with it a little.
Keep it simple
I tried to keep this as simple as possible as I found it difficult to get everything setup correctly the first time.
Comments
Anonymous
February 20, 2009
PingBack from http://www.clickandsolve.com/?p=12500Anonymous
February 24, 2009
In a previous post , I wrote about a very simple Access Control Service example that I assembled duringAnonymous
February 24, 2009
In a previous post , I wrote about a very simple Access Control Service example that I assembled during