Remove Unwanted HTTP Response Headers
The purpose of this blog post is to discuss how to remove unwanted HTTP response headers from the response. Typically we have 3 response headers which many people want to remove for security reason.
- Server - Specifies web server version.
- X-Powered-By - Indicates that the website is "powered by ASP.NET."
- X-AspNet-Version - Specifies the version of ASP.NET used.
Before you go any further, you should evaluate whether or not you need to remove these headers. If you have decided to remove these headers because of a security scan on your site, you may want to read the following blog post by David Wang.
https://blogs.msdn.com/b/david.wang/archive/2006/03/29/silly-security-scans.aspx
If you would like to go ahead and remove the headers then follow the following options.
Server Header
There are three ways to remove the Server header from the response. The best one is to use the third option.
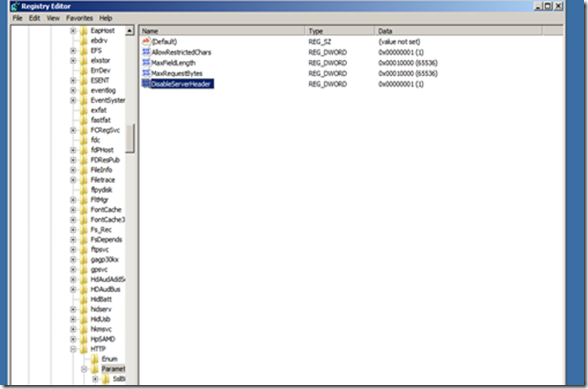
1. Using the Registry key.
Create a DWORD entry called DisableServerHeader in the following Registry key and set the value to 1.
HKLM\SYSTEM\CurrentControlSet\Services\HTTP\Parameters
After adding the Registry key, restart the HTTP service using the net stop http command and the net start http command. If the HTTP service doesn’t start up then use the iisreset command. If that also doesn’t work then you can restart the server.
Please note that this method is used only when the Server header comes as “Microsoft-HTTPAPI/2.0”.
When the request comes to IIS, it is first goes to http.sys driver. HTTP.SYS driver either handle the request on its own or send it to User mode for further processing. When the request goes to User mode that’s the time it returns the server header as “Microsoft-IIS/7.5.”.
However when the request returns from the HTTP.SYS driver then the server header comes as “Microsoft-HTTPAPI/2.0”. By placing the above registry key it will remove this specific header
If you would like to remove the Server header as “Microsoft-IIS/7.5.”, then follow the following methods.
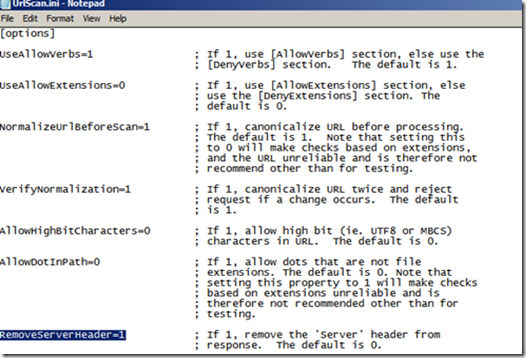
2. Using the URLScan tool.
Install the URLScan in your machine. Please follow the following link for that
https://www.iis.net/downloads/microsoft/urlscan
After installing URLScan, open the URLScan.ini file typically located in the %WINDIR%\System32\Inetsrv\URLscan folder. After opening it, search for the key RemoveServerHeader . By default it is set to 0, but to remove the Server header, change the value to 1.Doing so will remove the Server header Server: Microsoft-IIS/7.5 from the User mode response.
Please note that changes made by URLScan at global level apply to all of your sites. If you would like to setup this for particular site then look at the following article (site filter section)
https://www.iis.net/learn/extensions/working-with-urlscan/urlscan-setup
There are also some pitfalls to using URLScan. You can learn about those pitfalls at the following URL:
https://msdn.microsoft.com/en-us/library/ff648552.aspx\#ht\_urlscan\_008
3. Using URLRewrite
If you don’t want to go with URLScan, you can use the URLRewrite module to remove the value of the Server header. Please note that it will not remove the header all together but it will remove the value of it.
Step 1. Install URLRewrite. To install the URLRewrite please go to the following link
https://www.iis.net/downloads/microsoft/url-rewrite
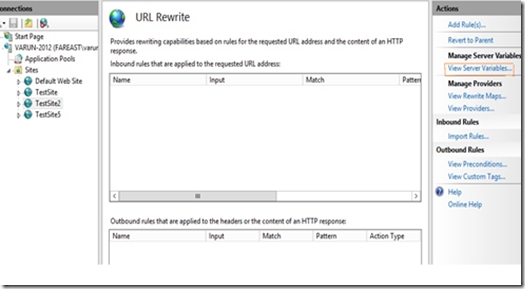
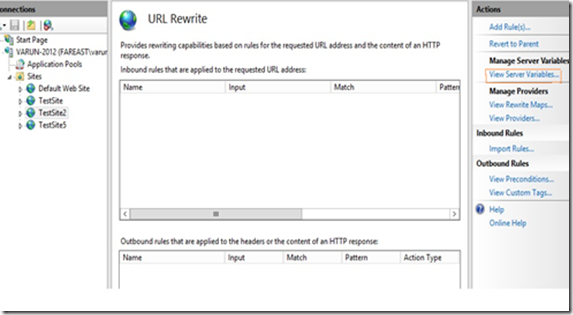
Step 2. Open the site on which you would like to remove the Server header and click on the URLRewrite section .
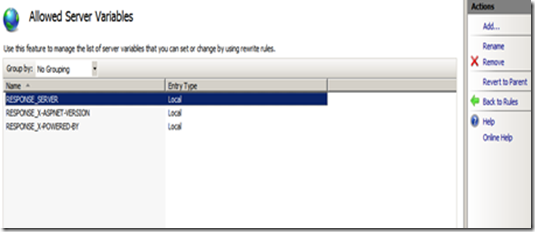
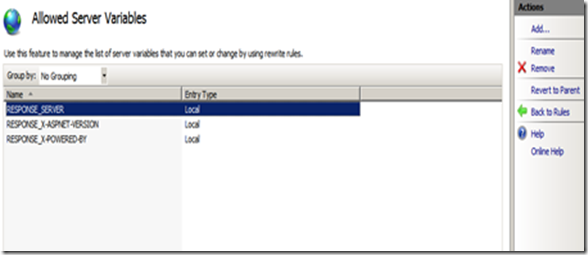
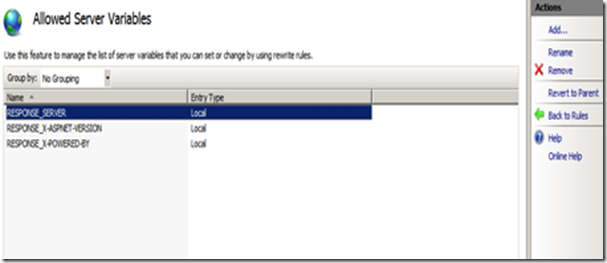
Step 4. Click on the “View Server Variables” in the Actions pane in the right hand side.
Step 5. Click on the Add button and then enter “RESPONSE_SERVER” in the textbox provided.
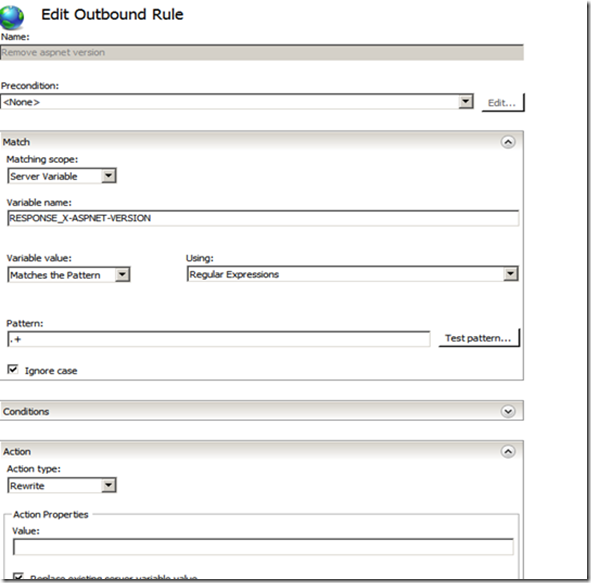
Step 6. Now we need to create an outbound rule. To know how to create an outbound rule, look at the following link
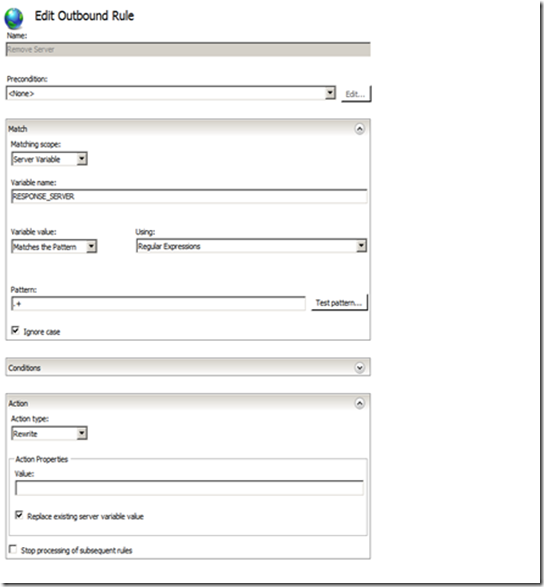
Step 7. Create an Outbound rule as the following.
Please note that this is a website-specific rule. If you want to create the rule for all of your applications, create the rule at the server level. Also, some applications, especially third party applications, may require the Server header, so you may need to remove this rule for those applications.
X-Powered-By
There are two ways to do remove this header as well. Second method would be the preferred one.
1. Using IIS HTTP Response headers.
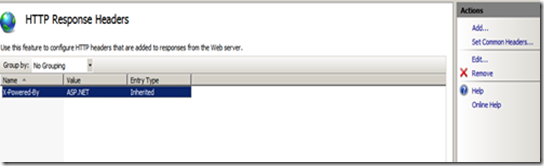
Open the site which you would like to open and then click on the HTTP Response Headers option.
Click on the X-Powered-By header and then click Remove on the Actions Pane to remove it from the response.
2. Using URLRewite Rule.
Please note that it will not remove the header all together but it will remove the value of it.
Step 1. Install URLRewrite. To install the URLRewrite please go to the following link
https://www.iis.net/downloads/microsoft/url-rewrite
Step 2. Open the site on which you would like to remove the X-Powered-By header and Click on the URLRewrite section .
Step 3. Click on the “View Server Variables” in the Actions pane in the right hand side.
Step 4. Click on the Add button and then enter “RESPONSE_X-POWERED-BY” in the textbox provided.
Step 5. Now we need to create an outbound rule. To know how to create an outbound rule, look at the following link
Step 6. Create an Outbound rule as the following
Please note that this is a website-specific rule. If you want to create the rule for all of your applications, create the rule at the server level. Also, some applications, especially third party applications, may require the x-powered-by header, so you may need to remove this rule for those applications.
X-AspNet-Version
There are two ways to do remove this header as well. Preferred one is the first one.
1. Using the httpRuntime element.
Add the following line in your web.config in the <system. Web> section
<httpRuntime enableVersionHeader="false" />
2. Using an URLRewite rule.
Please note that it will not remove the header all together but it will remove the value of it.
Step 1. Install URLRewrite. To install the URLRewrite please go to the following link
https://www.iis.net/downloads/microsoft/url-rewrite
Step 2. Open the site on which you would like to remove the Server header and go to the URLRewrite section .
Step 3. Click on the “View Server Variables” in the Actions pane in the right hand side.
Step 4. Click on the Add button and then enter “RESPONSE_X-ASPNET-VERSION” in the textbox provided.
Step 5. Now we need to create an outbound rule. To know how to create an outbound rule, look at the following link
Step 6. Create an Outbound rule as the following.
Please note that this is a website-specific rule. If you want to create the rule for all of your applications, create the rule at the server level. Also, some applications, especially third party applications, may require the x-aspnet-version header, so you may need to remove this rule for those applications.
Comments
Anonymous
April 23, 2013
This is an extremely helpful post; I like how you've spelled it all out. I'm surprised there aren't more responses.Anonymous
April 23, 2013
You COULD do all of what you have described, OR, if you are running an ASP.NET MVC website, you could just install this package: nuget.org/.../Dinheiro.RemoveUnnecessaryHeaders :-)Anonymous
May 03, 2013
thanks for this post budy azad chouhan crazydotnetlover.blogspot.inAnonymous
May 06, 2013
Nice Post...quite helpful!!!Thanks!!!Anonymous
May 06, 2013
Thank you allAnonymous
May 07, 2013
awesome post Varun :) Really helpfulAnonymous
May 07, 2013
Nice article..will it improve the performance of the website too? Regards Kshitish <a href='http://www.studyalways.com'>www.studyalways.com</a>Anonymous
May 09, 2013
Here is a similar post: www.troyhunt.com/.../shhh-dont-let-your-response-headers.htmlAnonymous
June 01, 2013
Hello Kshitish, Its just for the security purpose. I don't think so it will make any significant improvement in performance.Anonymous
October 01, 2013
Options 1 & 2 simple do not work for our Win2k8R2 IIS 7.5 server and I am loathe to install third party plugins.Anonymous
December 22, 2013
Finally, RESPONSE_X-ASPNET-VERSION is live <a href="taikhoanforex.weebly.com/.../a>Anonymous
March 03, 2014
@Orac - the 'third party plugins' you refer to are actually Microsoft addons for IIS.Anonymous
March 16, 2014
Best post I found, tells the whole story and explains what and why needs to be done. Other posts I found suggested solutions but didn't explain what does what. Both steps 1 and 2 (for Server header) work fine on Windows Server 2008 R2 II 7.5.Anonymous
March 23, 2014
Hello, are the solutions also for IIS 7.5 ?Anonymous
July 13, 2014
The comment has been removedAnonymous
August 18, 2014
The comment has been removedAnonymous
September 11, 2014
You should get a gold medal for this post Man..!!Anonymous
November 18, 2014
my site http://codeplussoft.com is using share hosting any solution for that ?Anonymous
November 18, 2014
check this for more info and share agen.yoobooy.com/.../rakebackAnonymous
December 05, 2014
The comment has been removedAnonymous
December 20, 2014
wow…thank you for this awesome post. It really shows your immense knowledge and research on this topic. Please keep sharing.Anonymous
December 25, 2014
Dear Sir, your Blog is superb and it will help me. you can also visit My ideas startupaccelerator.blogspot.inAnonymous
February 02, 2015
How about Cache-Control Pragma Expires Date ?Anonymous
May 12, 2015
I don't think the reg key for removing the Server key works in IIS 8 on Server 2012. Doesn't for me, anyway.Anonymous
May 13, 2015
Hi There, Thank you for this. Is there a way to block the Server and X-Powered-By information from the response headers when a file is not found. I was testing and I noticed that I could get the above server details from Fiddler by just using the website url and looking for a file that doesn't exist . E.g. www.someUrl.com/fileThatDoesNotExist. ThanksAnonymous
June 18, 2015
Hi there, Try this. www.nuget.org/.../RemoveUnwantedHeaderModuleAnonymous
July 05, 2015
Thanks for this post. really awesome.Anonymous
July 07, 2015
The comment has been removedAnonymous
September 14, 2015
Why... Why MS should make things so difficult. Especially the Server variable that requires you to use regedit... Shouldn't there be a switch on IIS Manager to disable this thing? Not to go on the topic of why these things are included by default in the first place... I understand that it's some sort of advertisement, but at least make it easier to rip them off. At least, I would expect all ASP.NET related headers to be turned on/off at the same place. But, no.... I had to turn off one in web.config and the other one in C# code: MvcHandler.DisableMvcResponseHeader = true; // Remove "X-AspNetMvc-Version" header. This article misses that last one ^^^.Anonymous
January 13, 2016
Thank You Very Much. Its helps me a lot.Anonymous
January 18, 2016
Is there a way to make it appear to be Apache or Nginx?Anonymous
January 28, 2016
Insane that they made this so hard. It's a terrible security threat!Anonymous
February 01, 2016
Awesome post - greatly appreciated.Anonymous
February 04, 2016
The comment has been removed