Protect against potentially unwanted applications (PUAs)
This article explains how you can protect against potentially unwanted applications (PUAs) using Microsoft Edge or by using Windows Defender Antivirus.
Overview
Potentially unwanted applications aren't considered to be viruses or malware, but these apps might perform actions on endpoints that adversely affect endpoint performance or use. For example, Evasion software actively tries to evade detection by security products. This kind of software can increase the risk of your network being infected with actual malware. PUA can also refer to applications that are considered to have poor reputation.
For a description of the criteria used to classify software as a PUA, see Potentially unwanted application.
Protect against PUA with Microsoft Edge
Microsoft Edge (version 80.0.361.50 or later) blocks PUA downloads and associated resource URLs.
You can set up protection by enabling the Block potentially unwanted apps feature in Microsoft Edge.
Note
The Microsoft Edge Team blog post describes this new feature and explains how to handle a mislabeled app or report an app as unwanted.
To enable PUA protection:
Open Settings in the browser.
Select Privacy and services.
In the Services section, check to see that Microsoft Defender SmartScreen is turned on. If not, then turn on Microsoft Defender SmartScreen. The example in the following screenshot shows the browser is managed by the organization and that Microsoft Defender SmartScreen is turned on.
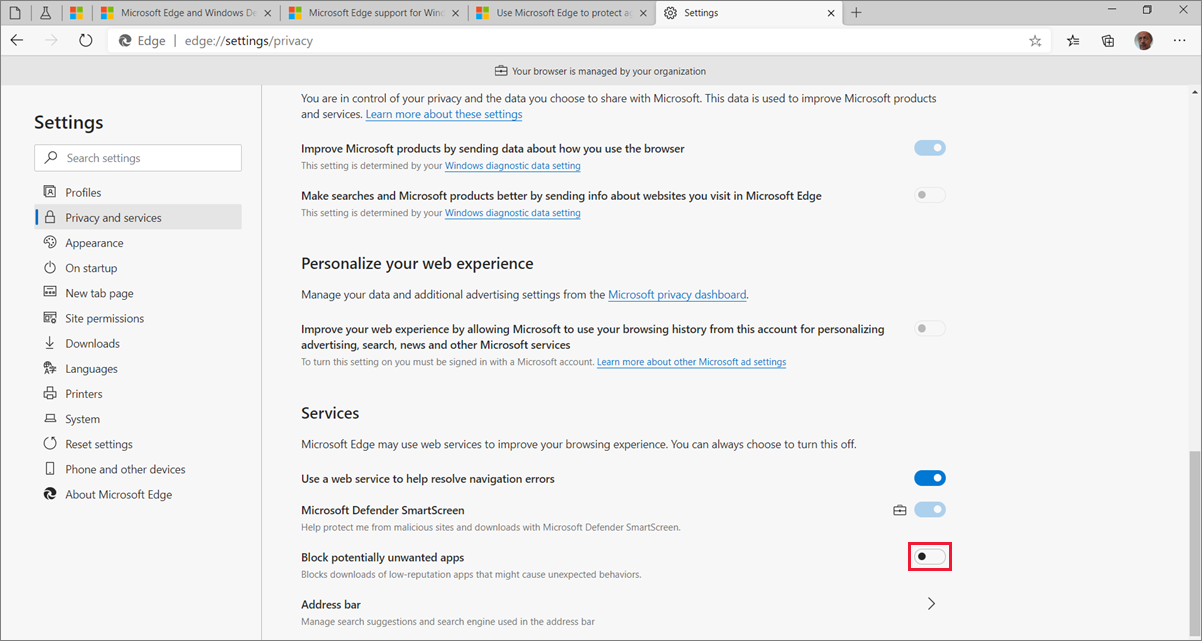
In the Services section, use the toggle shown in the preceding screenshot to turn on Block potentially unwanted apps.
Tip
You can safely explore the URL-blocking feature of PUA protection by testing it out on one of our Windows Defender SmartScreen demo pages.
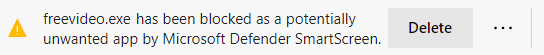
When Microsoft Edge detects a PUA, you'll see a message like the one in the next screenshot.
To block against PUA-associated URLs
After you turn on PUA protection in Microsoft Edge, Windows Defender SmartScreen will protect you from PUA-associated URLs.
There are several ways admins can configure how Microsoft Edge and Windows Defender SmartScreen work together to protect users from PUA-associated URLs. For more information, see:
- Configure Microsoft Edge policy settings on Windows
- SmartScreen settings
- SmartScreenPuaEnabled policy
- Configure Windows Defender SmartScreen
Admins can also customize the Microsoft Defender Advanced Threat Protection (ATP) blocklist. They can use the Microsoft Defender ATP portal to create and manage indicators for IPs and URLs.
Protect against PUA with Windows Defender Antivirus
The Detect and block potentially unwanted applications article also describes how you can configure Windows Defender Antivirus to enable PUA protection. You can configure protection using any of the following options:
When Windows Defender detects a PUA file on an endpoint, it quarantines the file and notifies the user (unless notifications are disabled) in the same format as a normal threat detection (prefaced with "PUA:".) Detected threats also appear in the quarantine list in the Windows Security app.
PUA notifications and events
There are several ways an admin can see PUA events:
- In the Windows Event Viewer, but not in Microsoft Endpoint Configuration Manager or Intune.
- In an email if email notifications for PUA detections is turned on.
- In Windows Defender Antivirus event logs, where a PUA event is recorded under event ID 1116 with the message: "The antimalware platform detected malware or other potentially unwanted software."
Note
Users will see "*.exe has been blocked as a potentially unwanted app by Microsoft Defender SmartScreen".
Allowlist an app
Like Microsoft Edge, Windows Defender Antivirus provides a way to allow files blocked by mistake or needed to complete a task. If this happens, you can allowlist a file. For more information, see How to Configure Endpoint Protection in Configuration Manager to learn how to exclude specific files or folders.