Notitie
Voor toegang tot deze pagina is autorisatie vereist. U kunt proberen u aan te melden of de directory te wijzigen.
Voor toegang tot deze pagina is autorisatie vereist. U kunt proberen de mappen te wijzigen.
Customer Key lets you control your organization's encryption keys and configure Microsoft 365 to use those keys to encrypt your data at rest in Microsoft's datacenters. In other words, it allows you to add a layer of encryption that you own and manage.
Before using Customer Key, you need to set up the required Azure resources. This article walks you through creating and configuring those resources, followed by the steps to enable Customer Key. After setting up the Azure resources, you choose which policy applies, and in turn, which keys will encrypt data across Microsoft 365 workloads in your organization.
For a general overview and more information, see Overview of Customer Key.
Important
Be sure to follow the best practices in this article marked as TIP, IMPORTANT, and NOTE. Customer Key gives you control over root encryption keys that can affect your entire organization. Mistakes with these keys can lead to service interruptions or permanent data loss.
Important
Microsoft recommends that you use roles with the fewest permissions. Minimizing the number of users with the Global Administrator role helps improve security for your organization. Learn more about Microsoft Purview roles and permissions.
Before you set up Customer Key
Before you begin, make sure your organization has the right Azure subscriptions; and Microsoft 365, Office 365, and Windows 365 licenses. You must use paid Azure subscriptions. Subscriptions acquired through Free, Trial, Sponsorship, MSDN, or Legacy Support programs aren't eligible.
Important
Microsoft 365 and Office 365 licenses that offer Microsoft 365 Customer Key are:
- Office 365 E5
- Microsoft 365 E5
- Microsoft Purview Suite (formerly known as Microsoft 365 E5 Compliance)
- Microsoft 365 E5 Information Protection & Governance SKUs
- Microsoft 365 Security and Compliance for FLW
Existing Office 365 Advanced Compliance licenses are still supported.
To better understand the concepts and procedures in this article, review the Microsoft Azure Key Vault documentation. You should also be familiar with key Azure terms like Microsoft Entra tenant.
If you need help beyond the documentation, contact Microsoft Support. To share feedback or suggestions about Customer Key or this documentation, visit the Microsoft 365 Community.
Overview of steps to set up Customer Key
To set up Customer Key, complete the following tasks in order. The rest of this article provides detailed instructions for each task, or links out to more information for each step in the process.
Complete the following prerequisites using Azure PowerShell. (v4.4.0 or higher is recommended):
Important
The setup process differs depending on whether you're using Azure Key Vault or Managed HSM. The shared prerequisites appear first, followed by configuration-specific instructions.
Prerequisites for all configurations
Configuration-specific setup
Final steps
- Onboard using the Customer Key Onboarding Service
- Onboard to Customer Key using the legacy method
- Onboard to Customer Key for SharePoint and OneDrive
- Onboard to Customer Key for special cloud environments
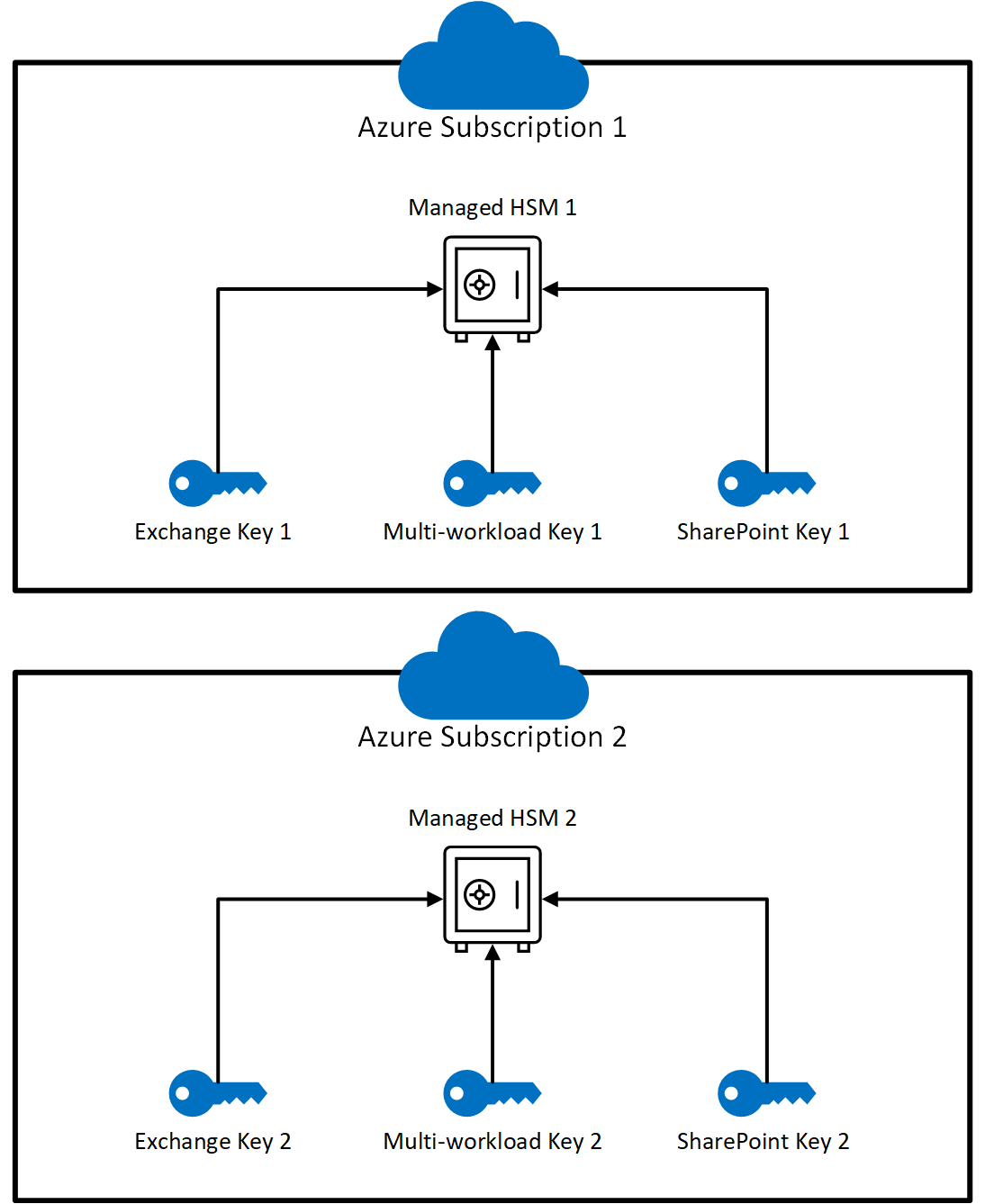
Create two new Azure subscriptions
Customer Key requires two Azure subscriptions. As a best practice, Microsoft recommends creating new Azure subscriptions specifically for use with Customer Key.
Azure Key Vault keys can only be authorized for applications in the same Microsoft Entra tenant. To assign data encryption policies (DEPs), make sure to create both subscriptions under the same Microsoft Entra tenant used by your organization. For example, use your work or school account that has proper administrator privileges in your organization. For step-by-step guidance, see Sign up for Azure as an organization.
Important
Customer Key requires two keys for each DEP. To support this requirement, you must create two separate Azure subscriptions. As a best practice, have different members of your organization manage one key in each subscription. These subscriptions should be used only to administer encryption keys for Microsoft 365. This configuration helps protect your organization in case someone accidentally, intentionally, or maliciously deletes or mismanages a key they control.
There's no practical limit to how many Azure subscriptions your organization can create. Following these best practices helps reduce the risk of human error and makes it easier to manage Customer Key resources.
Register the required Service Principals
To use the Customer Key, your tenant must have the required service principals registered. The following sections show you how to check whether the service principals are already registered in your tenant. If they aren't, run the 'New-AzADServicePrincipal' cmdlet.
Register the Service Principal for the Customer Key Onboarding Application
To check if the Customer Key Onboarding application is already registered with the correct permissions, run the following command:
Get-AzADServicePrincipal -ServicePrincipalName 19f7f505-34aa-44a4-9dcc-6a768854d2ea
If it isn't registered, run:
New-AzADServicePrincipal -ApplicationId 19f7f505-34aa-44a4-9dcc-6a768854d2ea
Register the Service Principal for the M365DataAtRestEncryption Application
To check if the M365DataAtRestEncryption application is already registered with the correct permissions, run the following command:
Get-AzADServicePrincipal -ServicePrincipalName c066d759-24ae-40e7-a56f-027002b5d3e4
If it isn't registered, run:
New-AzADServicePrincipal -ApplicationId c066d759-24ae-40e7-a56f-027002b5d3e4
Register the Service Principal for the Office 365 Exchange Online Application
To check if the Office 365 Exchange Online application is already registered with the correct permissions, run the following command:
Get-AzADServicePrincipal -ServicePrincipalName 00000002-0000-0ff1-ce00-000000000000
If it isn't registered, run:
New-AzADServicePrincipal -ApplicationId 00000002-0000-0ff1-ce00-000000000000
Configuration-specific setup steps
Important
The following steps differ depending on whether you're using Azure Key Vault or Managed HSM. Use the tabs below to select your configuration.
Create a premium Azure Key Vault in each subscription
Prior to creating a key vault, perform the steps in Getting Started with Azure Key Vault. These steps guide you through installing and launching Azure PowerShell, and connecting to your subscription. Next, create a resource group and a key vault.
Important
When creating your key vaults, you must enable both soft delete and purge protection during the initial vault creation process. Customer Key requires all vaults to have both features enabled with a retention period of 90 days. These settings can't be disabled once enabled, so it's critical to configure them correctly from the start.
When you create a key vault, you must choose an SKU: either Standard or Premium. The Standard SKU uses software-protected keys without a Hardware Security Module (HSM), while the premium SKU allows the use of HSMs to protect keys. Customer Key supports key vaults with either of the two SKUs, but Microsoft strongly recommends using the Premium SKU. The cost of operations is the same for both; so, the only price difference comes from the monthly cost of each HSM-protected key. For pricing details, see Key Vault pricing.
Important
Use the Premium SKU key vaults and HSM-protected keys for production data. Use Standard SKU key vaults and keys only for testing and validation.
Enabling soft delete and purge protection
When you can quickly recover your keys, you're less likely to experience extended service outages from accidental or malicious deletion. This recovery feature is called soft delete. It allows you to recover deleted keys or vaults within 90 days without needing to restore from a backup. Customer Key requires all vaults to have soft delete enabled and have a retention period of 90 days. Soft delete is automatically enabled for new Azure Key Vaults. If you use existing vaults where it's not turned on, you can enable it manually.
When purge protection is on, a vault or an object in the deleted state can't be purged until the retention period passes. Soft-deleted vaults and objects can still be recovered, ensuring that the retention policy is followed.
To enable soft delete and purge protection on your Azure Key Vault, see Azure Key Vault recovery management with soft delete and purge protection.
For each Microsoft 365 workload for which you use Customer Key, create a key vault in each of the two Azure subscriptions you set up earlier.
Key Vault configuration
For example, if you're using Customer Key for Multiple Workloads, Exchange and SharePoint scenarios, you need three pairs of key vaults, for a total of six. Use a clear naming convention that reflects the intended use of the DEP with which you associate the vaults. The following table shows how to map each Azure Key Vault to each workload.
| Key Vault Name | Permissions for Multiple Microsoft 365 Workloads (M365DataAtRestEncryption) | Permissions for Exchange | Permissions for SharePoint and OneDrive |
|---|---|---|---|
| ContosoM365AKV01 | Yes | No | No |
| ContosoM365AKV02 | Yes | No | No |
| ContosoEXOAKV01 | No | Yes | No |
| ContosoEXOAKV02 | No | Yes | No |
| ContosoSPOAKV01 | No | No | Yes |
| ContosoSPOAKV02 | No | No | Yes |
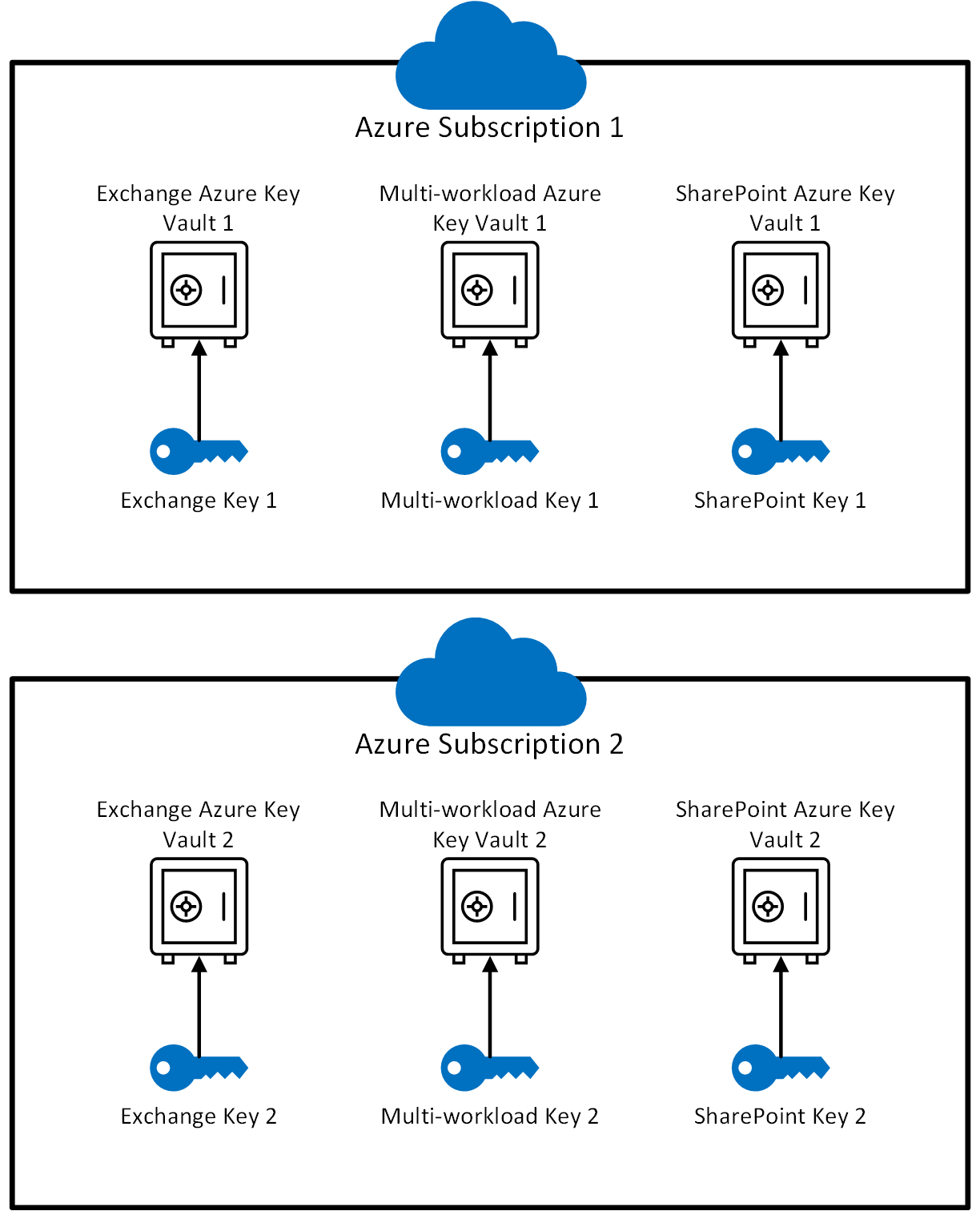
Creating key vaults also requires setting up Azure resource groups. Key vaults require a small amount of storage, and logging (if enabled) also stores data. As a best practice, Microsoft recommends assigning different administrators to manage each resource group. These roles should align with the admins responsible for managing the associated Customer Key resources.
For Exchange, a DEP is scoped at the mailbox level. Each mailbox can have only one policy assigned, and you can create up to 50 policies. A SharePoint policy covers all data in an organization's geographic location (or geo), while a multi-workload policy covers supported workloads across all users in the organization.
Important
If you're using Customer Key for Multiple Workloads, Exchange, and SharePoint and OneDrive, make sure to create two Azure Key Vaults for each workload. This means you need a total of six key vaults.
Assign permissions to each Azure Key Vault
Assign the required permissions to each key vault using Azure role-based access control (Azure RBAC) in the Azure portal. This section explains how to apply the correct permissions using RBAC.
Assigning permissions using RBAC method
To assign (wrapKey, unwrapKey, and get) on your Azure Key Vault, assign the Key Vault Crypto Service Encryption User role to the appropriate Microsoft 365 app. See Grant permission to applications to access an Azure Key Vault using Azure RBAC.
When assigning the role, search for the following app names in your tenant:
Multiple Workloads:
M365DataAtRestEncryptionExchange:
Office 365 Exchange OnlineSharePoint and OneDrive:
Office 365 SharePoint Online
If you don't see the app you're looking for, make sure you register the app in the tenant.
For more information about assigning roles and permissions, see Use role-based access control to manage access to your Azure subscription resources.
Assigning user roles
Customer Key requires both Key Vault Administrators and Key Vault Contributors to manage and safeguard access to encryption keys.
Key Vault Administrators handle daily management tasks such as backup, create, get, import, list, and restore. By design, they don’t have permission to delete keys. This design helps prevent permanent data loss. Only grant delete permissions temporarily and with caution using the Contributor role.
Key Vault Contributors can manage permissions and assign roles in the Key Vault. Use this role to control access when team members join or leave.
For detailed steps on assigning these roles using Azure RBAC, see Azure built-in roles for Key Vault data plane operations.
Add a key to each Key Vault either by creating or importing a key
There are two ways to add keys to an Azure Key Vault: you can create a key directly in the vault or import an existing key. Creating a key in Azure is simpler, but importing a key gives you full control over how the key is generated. Use RSA keys. Customer Key supports RSA key lengths up to 4,096 bits. Azure Key Vault doesn't support wrapping and unwrapping with elliptical curve (EC) keys.
To add a key to each vault, see Add-AzKeyVaultKey.
If you prefer to generate a key on-premises and then import it into Azure, perform the steps in How to generate and transfer HSM-protected keys for Azure Key Vault. Use the Azure instructions to add a key to each Key Vault.
Verify expiration date of your keys
To check that your keys don't have an expiration date, run the Get-AzKeyVaultKey cmdlet.
For Azure Key Vault:
Get-AzKeyVaultKey -VaultName <vault name>
Customer Key can't use expired keys. If a key is expired, any operation using it fails, which can lead to a service outage. We strongly recommend that keys used with Customer Key don't have an expiration date.
Once set, an expiration date can't be removed, but you can change it. If you must use a key with an expiration date, update it to 12/31/9999 and use the legacy onboarding method. Any other expiration value fails Customer Key onboarding validation.
Note
The Customer Key Onboarding Service only accepts keys without an expiration date.
To change the expiration date to 12/31/9999, use the Update-AzKeyVaultKey cmdlet.
Update-AzKeyVaultKey -VaultName <vault name> -Name <key name> -Expires (Get-Date -Date "12/31/9999")
Caution
Don't set expiration dates on encryption keys used with Customer Key.
Back up Azure Key Vault Key
After you create or modify a key, make sure to immediately back it up. Store backup copies in both online and offline locations to help prevent data loss.
To back up a key in Azure Key Vault, use the Backup-AzKeyVaultKey cmdlet.
Important
If a key is deleted without a backup, it can't be recovered. Always create a backup after any key change or creation.
Obtain the URI for each Azure Key Vault key
After you set up your Key Vaults and add your keys, run the following command to get the URI for each key. You need these URIs when creating and assigning DEPs; so, be sure to save them somewhere secure.
Run the following command in Azure PowerShell—once for each Key Vault:
(Get-AzKeyVaultKey -VaultName <vault name>).Id
Onboard using the Customer Key Onboarding Service
The Microsoft 365 Customer Key Onboarding Service allows you to enable Customer Key in your tenant. This service automatically validates the required Customer Key resources. If you'd prefer, you can validate your resources separately before proceeding with enablement.
Important
This service isn't currently available for the following scenarios:
- Special clouds tenant: See Onboard to Customer Key for special cloud environments.
- SharePoint and OneDrive: See Onboard to Customer Key for SharePoint and OneDrive.
The account used for onboarding must have the following permissions:
- Service principal registration permissions: To register the required service principals.
- Reader role: On each Azure Key Vault used in the onboarding cmdlet.
Install the M365CustomerKeyOnboarding PowerShell module
Sign in to your Azure subscription with Azure PowerShell. For guidance, see Sign in with Azure PowerShell.
Install the latest version of the
M365CustomerKeyOnboardingmodule from the PowerShell Gallery.
- To confirm you're using the latest version, check the Version History tab at the bottom of the module page.
- Copy and paste the install command into your session and run it.
- If you're prompted, select Yes to All to continue.
Using the two different onboarding modes
There are two different onboarding modes available when using the Customer Key Onboarding Service: Validate, and Enable. Each mode serves a different purpose in the onboarding process.
When running the cmdlet (as guided in Create an Onboarding request), specify the mode using the -OnboardingMode parameter.
Validate
Use the Validate mode to confirm that your Customer Key resource configuration is correct. This mode doesn’t make any changes to your environment.
Important
You can run this mode as many times as needed, especially after making changes to your configuration.
Enable
Use the Enable mode when you're ready to onboard your tenant to Customer Key. This mode enables Customer Key for the workload you specify using the -Scenario parameter.
If you want to enable Customer Key for both Multiple Workloads and Exchange, run the cmdlet twice, once for each workload.
Before running in Enable mode, make sure your validation results show Passed under ValidationResult.
Important
Your resources must pass all checks in Validate mode for the onboarding process to succeed in Enable mode.
Creating an onboarding request
The first step in the onboarding process is to create a new request. In PowerShell, you can store the results of a cmdlet in a variable using the $ symbol followed by the variable name.
In this example, the onboarding request is stored in a variable named $request:
$request = New-CustomerKeyOnboardingRequest -Organization <tenantID> -Scenario <Scenario> -Subscription1 <subscriptionID1> -KeyIdentifier1 <KeyURI1> -Subscription2 <subscriptionID2> -KeyIdentifier2 <KeyURI2> -OnboardingMode <OnboardingMode>
| Parameter | Description | Example |
|---|---|---|
-Organization |
Your tenant ID in the format xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx. |
abcd1234-abcd-efgh-hijk-abcdef123456 |
-Scenario |
The workload you're onboarding to. Options: MDEP – Customer Key for Multiple Workloads, EXO – Customer Key for Exchange |
MDEP or EXO |
-Subscription1 |
Azure subscription ID of the first subscription. | p12ld534-1234-5678-9876-g3def67j9k12 |
-KeyIdentifier1 |
The Key URI of the first AKV or HSM Key configured for Customer Key. | https://exampleVault1.vault.azure.net/keys/customerKey1 |
-Subscription2 |
Azure subscription ID of the second subscription. | 21k9j76f-ed3g-6789-8765-43215dl21pbd |
-KeyIdentifier2 |
The Key URI of the second AKV or HSM Key configured for Customer Key. | https://exampleVault2.vault.azure.net/keys/customerKey2 |
-OnboardingMode |
The onboarding action to perform. Options: Validate – Validates your configuration without making changes. Useful for verifying before onboarding. Enable – Validates and enables Customer Key in your tenant if validation passes. |
Validate, or Enable |
Sign in with your tenant admin credentials
When prompted, a browser window opens. Sign in using your tenant admin account with the necessary privileges to complete onboarding.
View validation and enablement details
After successfully signing in, return to your PowerShell window. Run the variable you used when creating the onboarding request to view its output:
$request
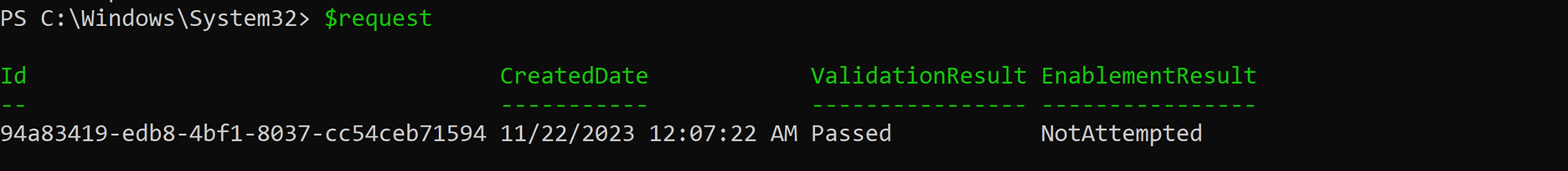
You receive an output that includes ID, CreatedDate, ValidationResult, and EnablementResult.
| Output | Description |
|---|---|
ID |
ID associated with the created onboarding request. |
CreatedDate |
Date on which the request was created. |
ValidationResult |
Indicator of successful/unsuccessful validation. |
EnablementResult |
Indicator of successful/unsuccessful enablement. |
A tenant that's ready to use Customer Key shows Success for both ValidationResult and EnablementResult as shown in the following screenshot:
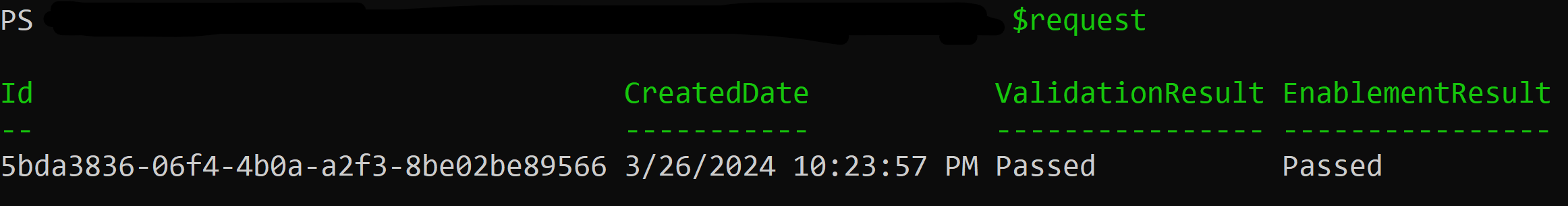
If both values show Success, proceed to Next Steps.
Troubleshooting failed validations details
If validation fails during onboarding, perform the following steps to investigate the cause. This process helps identify which Customer Key resources are misconfigured.
- List all onboarding requests for your tenant to find the
RequestIDof the one you want to investigate:
Get-CustomerKeyOnboardingRequest -OrganizationID <OrganizationID>
- Store the specific onboarding request into a variable:
$request = Get-CustomerKeyOnboardingRequest -OrganizationID <OrganizationID> -RequestID <RequestID>
- View the failed validation details:
$request.FailedValidations
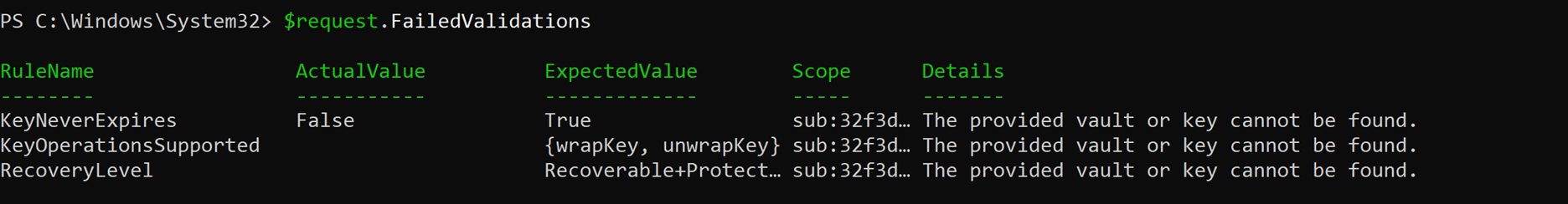
Each validation rule includes the following fields:
- ExpectedValue: What the resource configuration should be.
- ActualValue: What was detected in your environment.
- Scope: The first five characters of the subscription ID that helps you identify which subscription (and its associated Key Vault) has the issue.
- Details: Describes the root cause and offers guidance to resolve the problem.
The following table summarizes common validation rules and how to resolve failures:
| RuleName | Description | Solution |
|---|---|---|
OrganizationHasRequiredServicePlan |
Verifies whether your organization has the required licenses. | See Ensure your tenant has the required licenses. |
KeyNeverExpires |
Ensures that the key has no expiration date. | See the key expiration verification steps in Configuration-specific setup |
KeyOperationsSupported |
Verifies whether the key supports required operations for the workload. | See the permissions assignment steps in Configuration-specific setup |
RecoveryLevel |
Checks if the key recovery level is Recoverable. |
Ensure both soft delete and purge protection are enabled. See Enabling Soft Delete and Purge Protection for Azure Key Vault or Create a resource group provision, and activate a Managed HSM for Managed HSM. |
SubscriptionInRequestOrganization |
Confirms that your Azure subscription belongs to your organization. | Make sure the subscription was created within the specified tenant. |
SubscriptionsCountPerScenario |
Confirms that two subscriptions were provided. | Make sure your onboarding request includes two subscriptions. |
SubscriptionUniquePerScenario |
Ensures you're using two unique subscriptions per scenario. | Double-check that both subscription IDs are different. |
VaultExistsinSubscription |
Confirms that the AKV/Managed HSM is part of the given subscription. | Verify whether the Key Vault/HSM was created in the correct subscription. |
Checking passed validations
To view which validations were successful during the onboarding process, perform the following steps:
- Store the specific onboarding request into the variable '$request'
$request = Get-CustomerKeyOnboardingRequest -OrganizationID <OrganizationID> -RequestID <RequestID>
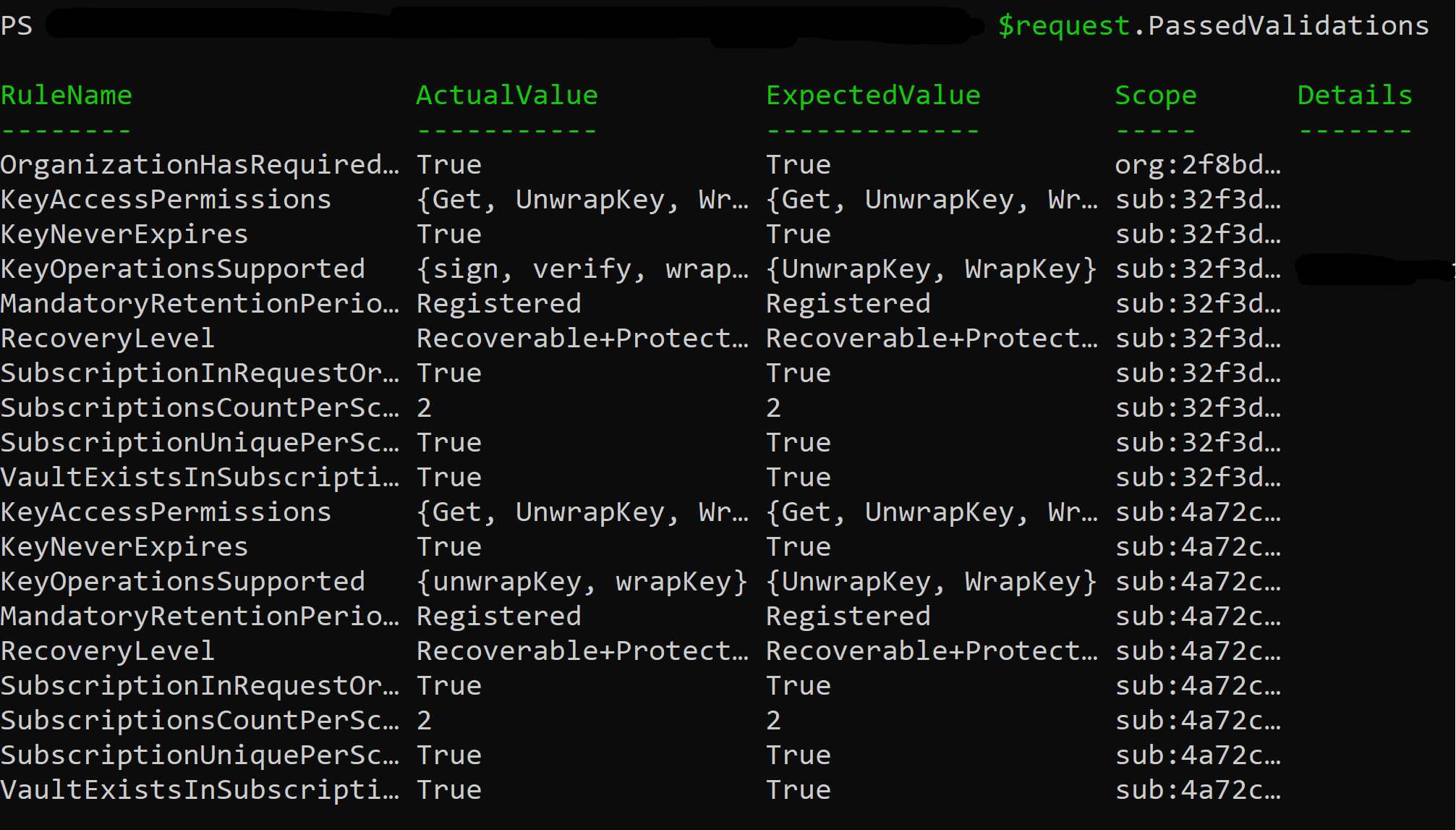
- Run the following command to display all passed validations:
$request.PassedValidations
This command returns a list of all the validations that passed successfully for the selected onboarding request.
Onboard to Customer Key using the legacy method
Use this method only if the Customer Key Onboarding Service doesn't support your tenant's scenario.
After completing all required steps to set up your Azure Key Vaults and subscriptions, contact Microsoft Support and request assistance with Customer Key onboarding.
Onboard to Customer Key for special cloud environments
If your tenant is located in GCC-H, DoD, or M365 operated by 21Vianet, complete all required Customer Key setup steps first.
For GCC-H and DoD tenants, contact Microsoft Support and request onboarding for government tenants.
For customers in Microsoft 365 operated by 21Vianet (China), configure your Customer Key resources using Azure operated by 21Vianet portal. Then, contact Microsoft Support and request onboarding for your tenant.
Onboard to Customer Key for SharePoint and OneDrive
To onboard to Customer Key for SharePoint and OneDrive, your Azure Key Vaults must meet the following prerequisites:
Enable both soft delete and purge protection during the initial vault creation process. See Enabling Soft Delete and Purge Protection for Azure Key Vault.
Maintain a retention period of 90 days.
If all prerequisites are satisfied, perform the steps in Create a DEP for use with SharePoint and OneDrive.
Next steps
After completing the setup steps in this article, you're ready to create and assign DEPs. For detailed instructions, see Manage Customer Key.