Get started with the data loss prevention Alerts dashboard
Microsoft Purview Data Loss Prevention (DLP) policies can take protective actions to prevent unintentional sharing of sensitive items. You can be notified when an action is taken on a sensitive item by configuring alerts for DLP. This article shows you how to configure alerts in your data loss prevention (DLP) policies. You'll see how to use the DLP alert management dashboard in the Microsoft Purview compliance portal to view alerts, events, and associated metadata for DLP policy violations.
If you're new to DLP alerts, you should review Get started with the data loss prevention alerts.
Tip
If you're not an E5 customer, use the 90-day Microsoft Purview solutions trial to explore how additional Purview capabilities can help your organization manage data security and compliance needs. Start now at the Microsoft Purview compliance portal trials hub. Learn details about signing up and trial terms.
Microsoft Purview compliance portal shows alerts for DLP policies that are enforced on the following workloads:
- Exchange email
- SharePoint sites
- OneDrive accounts
- Teams chat and channel messages
- Devices
- Instances
- On-premises repositories
- Fabric and Power BI
Before you begin
Before you begin, make sure you have the necessary prerequisites:
- Licensing for the DLP alerts management dashboard
- Licensing for alert configuration options
- Required roles
Licensing for the DLP alert management dashboard
Before you start using DLP policies, confirm your Microsoft 365 subscription and any add-ons.
For information on licensing, see Microsoft 365, Office 365, Enterprise Mobility + Security, and Windows 11 Subscriptions for Enterprises.
Customers who use Endpoint DLP who are eligible for Teams DLP see their endpoint DLP policy alerts and Teams DLP policy alerts in the DLP alert management dashboard.
Licensing for alert configuration options
Before you start using DLP policies, confirm your Microsoft 365 subscription and any add-ons.
For information on licensing, see Microsoft 365, Office 365, Enterprise Mobility + Security, and Windows 11 Subscriptions for Enterprises.
Roles and Role Groups
If you want to view the DLP alert management dashboard or to edit the alert configuration options in a DLP policy, you must be a member of one of these role groups:
- Compliance Administrator
- Compliance Data Administrator
- Security Administrator
- Security Operator
- Security Reader
- Information Protection Admin
- Information Protection Analyst
- Information Protection Investigator
- Information Protection Reader
To learn more about them, see Permissions in the Microsoft Purview compliance portal
Here's a list of applicable role groups. To learn more about them, see Permissions in the Microsoft Purview compliance portal.
- Information Protection
- Information Protection Admins
- Information Protection Analysts
- Information Protection Investigators
- Information Protection Readers
To access the DLP alert management dashboard, you need the Manage alerts role and either of these two roles:
- DLP Compliance Management
- View-Only DLP Compliance Management
To access the Content preview feature and the Matched sensitive content and context features, you must be a member of the Content Explorer Content Viewer role group, which has the Data classification content viewer role preassigned.
DLP alert configuration
To learn how to configure an alert in your DLP policy, see Create and Deploy data loss prevention policies.
Important
Your organization's audit log retention policy configuration controls how long an alert remains visible in the console. See, Manage audit log retention policies for more information.
Aggregate event alert configuration
If your organization is licensed for aggregated alert configuration options, then you see these options when you create or edit a DLP policy.
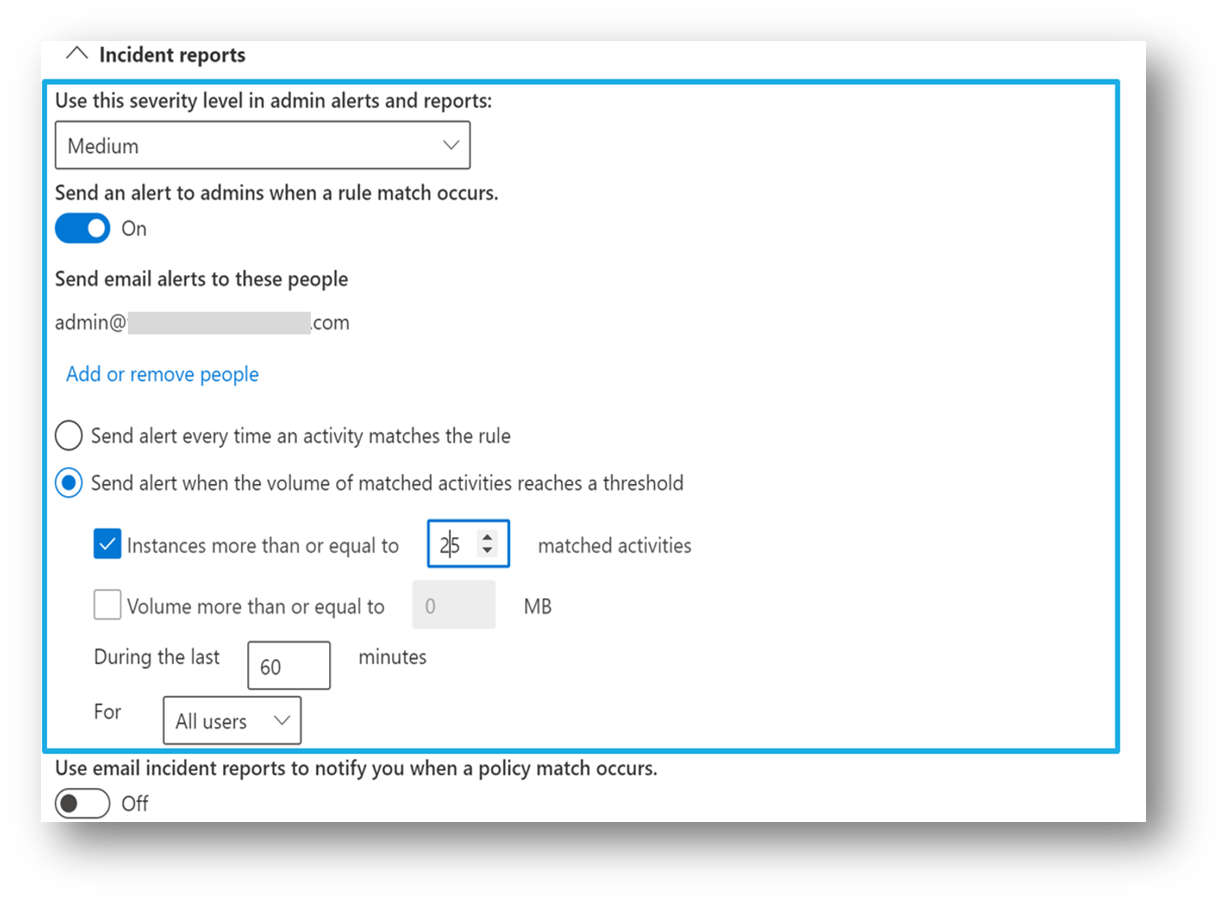
This configuration allows you to set up a policy to generate an alert every time an activity matches the policy conditions or when a certain threshold is exceeded, based on the number of activities or based on the volume of exfiltrated data.
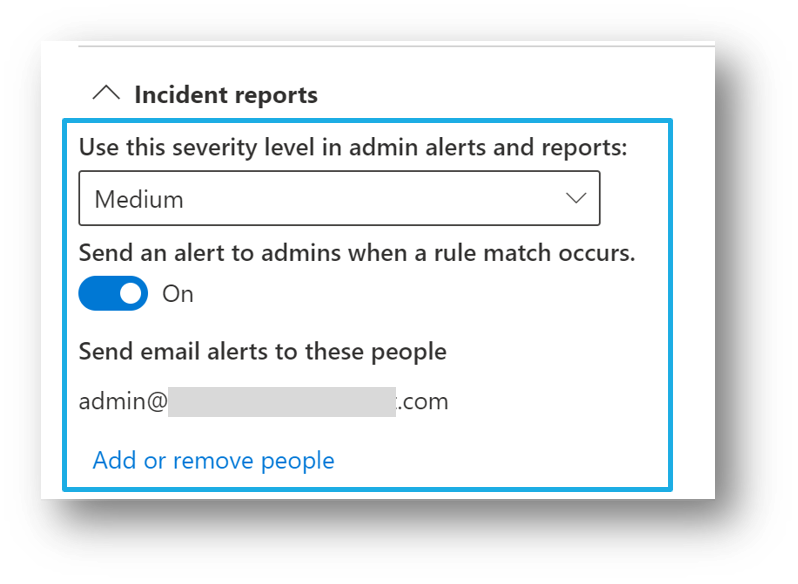
Single event alert configuration
If your organization is licensed for single-event alert configuration options, then you see these options when you create or edit a DLP policy. Use this option to create an alert that's raised every time a DLP rule match happens.
Investigate a DLP alert
Select the appropriate tab for the portal you're using. To learn more about the Microsoft Purview portal, see Microsoft Purview portal. To learn more about the Compliance portal, see Microsoft Purview compliance portal.
To work with the DLP alert management dashboard:
- Sign in to the Microsoft Purview portal > Data loss prevention.
- Select Alerts to view the DLP Alerts dashboard.
- Use the Filter fields to refine the list of alerts.
- Choose Customize columns to list the properties you want to see.
- To sort the results in ascending or descending order, double-click the column header.
- Double-click an alert for more information about it.
- The Details tab opens by default and provides high-level information about the alert.
- Select Summarize with Copilot. This causes the Security Copilot to generate a summary of the alert. The alert summary will contain the:
- alert severity
- alert title
- the name of the policy that was matched
- the name file involved and a link to the file
- alert status
- the email address of the user who performed the action that matched the policy
- Select the ellipsis in the Security Copilot summary to:
- copy the summary to the clipboard
- regenerate the summary
- open the alert in the Security Copilot standalone experience.
- Select View details to open the Overview tab. The Overview tab provides a summary of the following information:
- What happened
- Who performed the actions that caused the policy match
- Additional information about the policy match
- The Events tab lists all of the events associated with the alert. Select any event in the list to get detailed information about the event. For each event, choose the Actions drop down for a list of actions you can take on the alert, such as verifying whether or not the alert has identified a true match or a false positive.
- The User activity summary tab requires that sharing be turned On in the insider risk management settings Once enabled, the User activity summary tab provides all the exfiltration activities the user has engaged in (up to the past 120 days). Users must be in scope of an insider risk management policy to see the User activity summary tab.
- After you investigate the alert, return to the Overview tab where you can View details to triage and manage the disposition of the alert, add comments and assign ownership of the alert. (To see the history of workflow management.)
- After you take the required action for the alert, set the Status of the alert to Resolved.
Other matched conditions
Microsoft Purview supports showing matched conditions in a DLP event to reveal the exact cause for a flagged DLP policy. This information shows up in:
- DLP Alerts console
- Activity explorer
- Microsoft Defender for Business portal
In the Events tab, open Details to see Other matched conditions.
Prerequisites
- Must be running Windows 10 x64 (build 1809 or later) or Windows 11.
- See March 21, 2023—KB5023773 (OS Builds 19042.2788, 19044.2788, and 19045.2788) Preview for required minimum Windows Operating System builds.
- Matched conditions data is available for valid E3 and E5 license holders.
- Enable Auditing.
- Enable Advanced classification scanning and protection.
Matched events information is supported for these conditions
| Condition | Exchange | Sharepoint | Teams | Endpoint |
|---|---|---|---|---|
| Sender is | Yes | No | Yes | No |
| Sender domain is | Yes | No | Yes | No |
| Sender address contains words | Yes | No | No | No |
| Sender address matches patterns | Yes | No | No | No |
| Sender is a member of | Yes | No | No | No |
| Sender IP address is | Yes | No | No | No |
| Has sender overridden the policy tip | Yes | No | No | No |
| SenderAdAttribute Contains words | Yes | No | No | No |
| SenderAdAttribute Matches patterns | Yes | No | No | No |
| Recipient is | Yes | No | Yes | No |
| Recipient domain is | Yes | No | Yes | No |
| Recipient address contains words | Yes | No | No | No |
| Recipient address matches patterns | Yes | No | No | No |
| Recipient is a member of | Yes | No | No | No |
| RecipientAdAttribute Contains words | Yes | No | No | No |
| RecipientAdAttribute Matches patterns | Yes | No | No | No |
| Document is password protected | Yes | No | No | No |
| Document could not be scanned | Yes | No | No | No |
| Document did not complete scanning | Yes | No | No | No |
| Document name contains words | Yes | Yes | No | No |
| Document name matches patterns | Yes | No | No | No |
| Document property is | Yes | Yes | No | No |
| Document size over | Yes | Yes | No | No |
| Document content contains words | Yes | No | No | No |
| Document content matches patterns | Yes | No | No | No |
| Document type is | No | No | No | Yes |
| Document extension is | Yes | Yes | No | Yes |
| Content is shared from M365 | Yes | Yes | Yes | No |
| Content is received from | Yes | No | No | No |
| Content character set contains words | Yes | No | No | No |
| Subject contains words | Yes | No | No | No |
| Subject matches patterns | Yes | No | No | No |
| Subject or body contains words | Yes | No | No | No |
| Subject or body matches patterns | Yes | No | No | No |
| Header contains words | Yes | No | No | No |
| Header matches patterns | Yes | No | No | No |
| Message size over | Yes | No | No | No |
| Message type is | Yes | No | No | No |
| Message importance is | Yes | No | No | No |
Limitation when downloading emails from within a DLP alert
In general, when using the DLP alert management dashboard, you can download specific emails from within an alert. However, emails that have been deleted in any of the following scenarios can't be downloaded.
| Sender | Recipient | Email Status |
|---|---|---|
| Internal | External | Deleted by sender |
| External | Internal | Deleted by recipient |
| Internal | Internal | Deleted by both parties |
Additional Alert investigation tools
Feedback
Binnenkort beschikbaar: In de loop van 2024 zullen we GitHub-problemen geleidelijk uitfaseren als het feedbackmechanisme voor inhoud en deze vervangen door een nieuw feedbacksysteem. Zie voor meer informatie: https://aka.ms/ContentUserFeedback.
Feedback verzenden en weergeven voor