Diagnose MDM enrollment
This article provides suggestions for troubleshooting device enrollment issues for MDM.
Verify autoenrollment requirements and settings
To ensure that the autoenrollment feature is working as expected, you must verify that various requirements and settings are configured correctly. The following steps demonstrate required settings using the Intune service:
Verify that the user who is going to enroll the device has a valid Intune license.
Verify that autoenrollment is activated for those users who are going to enroll the devices into Mobile Device Management (MDM) with Intune. For more information, see Microsoft Entra ID and Microsoft Intune: Automatic MDM enrollment in the new Portal.

Important
For bring-your-own devices (BYOD devices), the Mobile Application Management (MAM) user scope takes precedence if both MAM user scope and MDM user scope (automatic MDM enrollment) are enabled for all users (or the same groups of users). The device will use Windows Information Protection (WIP) Policies (if you configured them) rather than being MDM enrolled.
For corporate-owned devices, the MDM user scope takes precedence if both scopes are enabled. The devices get MDM enrolled.
Verify that the device is running a supported version of Windows.
Autoenrollment into Intune via Group Policy is valid only for devices that are Microsoft Entra hybrid joined. This condition means that the device must be joined into both local Active Directory and Microsoft Entra ID. To verify that the device is Microsoft Entra hybrid joined, run
dsregcmd /statusfrom the command line.You can confirm that the device is properly hybrid-joined if both AzureAdJoined and DomainJoined are set to YES.

Additionally, verify that the SSO State section displays AzureAdPrt as YES.
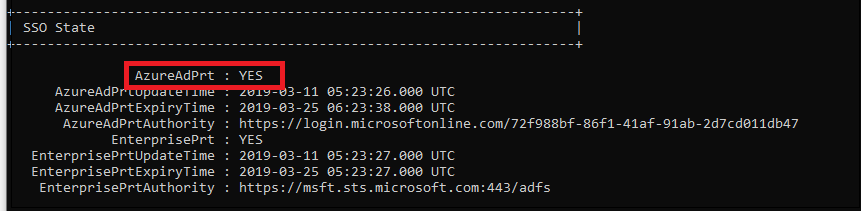
This information can also be found on the Microsoft Entra device list.
Verify that the MDM discovery URL during autoenrollment is
https://enrollment.manage.microsoft.com/enrollmentserver/discovery.svc.
Some tenants might have both Microsoft Intune and Microsoft Intune Enrollment under Mobility. Make sure that your autoenrollment settings are configured under Microsoft Intune instead of Microsoft Intune Enrollment.
When using group policy for enrollment, verify that the Enable Automatic MDM enrollment using default Microsoft Entra credentials group policy (Local Group Policy Editor > Computer Configuration > Policies > Administrative Templates > Windows Components > MDM) is properly deployed to all devices that should be enrolled into Intune. You may contact your domain administrators to verify if the group policy has been deployed successfully.
Verify that Microsoft Intune allows enrollment of Windows devices.
Troubleshoot group policy enrollment
Investigate the logs if you have issues even after performing all the verification steps. The first log file to investigate is the event log, on the target Windows device. To collect Event Viewer logs:
Open Event Viewer.
Navigate to Applications and Services Logs > Microsoft > Windows > DeviceManagement-Enterprise-Diagnostic-Provider > Admin.
Tip
For guidance on how to collect event logs for Intune, see Collect MDM Event Viewer Log YouTube video.
Search for event ID 75, which represents a successful autoenrollment. Here's an example screenshot that shows the autoenrollment completed successfully:
If you can't find event ID 75 in the logs, it indicates that the autoenrollment failed. This failure can happen because of the following reasons:
The enrollment failed with error. In this case, search for event ID 76, which represents failed autoenrollment. Here's an example screenshot that shows that the autoenrollment failed:
To troubleshoot, check the error code that appears in the event. For more information, see Troubleshooting Windows device enrollment problems in Microsoft Intune.
The autoenrollment didn't trigger at all. In this case, you won't find either event ID 75 or event ID 76. To know the reason, you must understand the internal mechanisms happening on the device as described here:
The autoenrollment process is triggered by a task (Microsoft > Windows > EnterpriseMgmt) within the task-scheduler. This task appears if the Enable automatic MDM enrollment using default Microsoft Entra credentials group policy (Computer Configuration > Policies > Administrative Templates > Windows Components > MDM) is successfully deployed to the target machine as shown in the following screenshot:
Note
This task isn't visible to standard users, run Scheduled Tasks with administrative credentials to find the task.
This task runs every 5 minutes for the duration of one day. To confirm if the task succeeded, check the task scheduler event logs: Applications and Services Logs > Microsoft > Windows > Task Scheduler > Operational. Look for an entry where the task scheduler created by enrollment client for automatically enrolling in MDM from Microsoft Entra ID is triggered by event ID 107.
When the task is completed, a new event ID 102 is logged.
The task scheduler log displays event ID 102 (task completed) regardless of the autoenrollment success or failure. This status-display means that the task scheduler log is only useful to confirm if the autoenrollment task is triggered or not. It doesn't indicate the success or failure of autoenrollment.
If you can't see from the log that task Schedule created by enrollment client for automatically enrolling in MDM from Microsoft Entra ID is initiated, there's possibly an issue with the group policy. Immediately run the command
gpupdate /forcein a command prompt to get the group policy object applied. If this step still doesn't help, further troubleshooting on Active Directory is required. One frequently seen error is related to some outdated enrollment entries in the registry on the target client device (HKLM > Software > Microsoft > Enrollments). If a device has been enrolled (can be any MDM solution and not only Intune), some enrollment information added into the registry is seen:By default, these entries are removed when the device is unenrolled, but occasionally the registry key remains even after unenrollment. In this case,
gpupdate /forcefails to initiate the autoenrollment task and error code 2149056522 is displayed in the Applications and Services Logs > Microsoft > Windows > Task Scheduler > Operational event log file under event ID 7016.A resolution to this issue is to remove the registry key manually. If you don't know which registry key to remove, go for the key that displays most entries as the previous screenshot shows. All other keys display fewer entries as shown in the following screenshot:
Error codes
| Code | ID | Error message |
|---|---|---|
| 0x80180001 | "idErrorServerConnectivity", // MENROLL_E_DEVICE_MESSAGE_FORMAT_ERROR | There was an error communicating with the server. You can try to do this again or contact your system administrator with the error code {0} |
| 0x80180002 | "idErrorAuthenticationFailure", // MENROLL_E_DEVICE_AUTHENTICATION_ERROR | There was a problem authenticating your account or device. You can try to do this again or contact your system administrator with the error code {0}. |
| 0x80180003 | "idErrorAuthorizationFailure", // MENROLL_E_DEVICE_AUTHORIZATION_ERROR | This user isn't authorized to enroll. You can try to do this again or contact your system administrator with the error code {0}. |
| 0x80180004 | "idErrorMDMCertificateError", // MENROLL_E_DEVICE_CERTIFCATEREQUEST_ERROR | There was a certificate error. You can try to do this again or contact your system administrator with the error code {0}. |
| 0x80180005 | "idErrorServerConnectivity", // MENROLL_E_DEVICE_CONFIGMGRSERVER_ERROR | There was an error communicating with the server. You can try to do this again or contact your system administrator with the error code {0} |
| 0x80180006 | "idErrorServerConnectivity", // MENROLL_E_DEVICE_CONFIGMGRSERVER_ERROR | There was an error communicating with the server. You can try to do this again or contact your system administrator with the error code {0} |
| 0x80180007 | "idErrorAuthenticationFailure", // MENROLL_E_DEVICE_INVALIDSECURITY_ERROR | There was a problem authenticating your account or device. You can try to do this again or contact your system administrator with the error code {0}. |
| 0x80180008 | "idErrorServerConnectivity", // MENROLL_E_DEVICE_UNKNOWN_ERROR | There was an error communicating with the server. You can try to do this again or contact your system administrator with the error code {0} |
| 0x80180009 | "idErrorAlreadyInProgress", // MENROLL_E_ENROLLMENT_IN_PROGRESS | Another enrollment is in progress. You can try to do this again or contact your system administrator with the error code {0}. |
| 0x8018000A | "idErrorMDMAlreadyEnrolled", // MENROLL_E_DEVICE_ALREADY_ENROLLED | This device is already enrolled. You can contact your system administrator with the error code {0}. |
| 0x8018000D | "idErrorMDMCertificateError", // MENROLL_E_DISCOVERY_SEC_CERT_DATE_INVALID | There was a certificate error. You can try to do this again or contact your system administrator with the error code {0}. |
| 0x8018000E | "idErrorAuthenticationFailure", // MENROLL_E_PASSWORD_NEEDED | There was a problem authenticating your account or device. You can try to do this again or contact your system administrator with the error code {0}. |
| 0x8018000F | "idErrorAuthenticationFailure", // MENROLL_E_WAB_ERROR | There was a problem authenticating your account or device. You can try to do this again or contact your system administrator with the error code {0}. |
| 0x80180010 | "idErrorServerConnectivity", // MENROLL_E_CONNECTIVITY | There was an error communicating with the server. You can try to do this again or contact your system administrator with the error code {0} |
| 0x80180012 | "idErrorMDMCertificateError", // MENROLL_E_INVALIDSSLCERT | There was a certificate error. You can try to do this again or contact your system administrator with the error code {0}. |
| 0x80180013 | "idErrorDeviceLimit", // MENROLL_E_DEVICECAPREACHED | Looks like there are too many devices or users for this account. Contact your system administrator with the error code {0}. |
| 0x80180014 | "idErrorMDMNotSupported", // MENROLL_E_DEVICENOTSUPPORTED | This feature isn't supported. Contact your system administrator with the error code {0}. |
| 0x80180015 | "idErrorMDMNotSupported", // MENROLL_E_NOTSUPPORTED | This feature isn't supported. Contact your system administrator with the error code {0}. |
| 0x80180016 | "idErrorMDMRenewalRejected", // MENROLL_E_NOTELIGIBLETORENEW | The server did not accept the request. You can try to do this again or contact your system administrator with the error code {0}. |
| 0x80180017 | "idErrorMDMAccountMaintenance", // MENROLL_E_INMAINTENANCE | The service is in maintenance. You can try to do this again later or contact your system administrator with the error code {0}. |
| 0x80180018 | "idErrorMDMLicenseError", // MENROLL_E_USERLICENSE | There was an error with your license. You can try to do this again or contact your system administrator with the error code {0}. |
| 0x80180019 | "idErrorInvalidServerConfig", // MENROLL_E_ENROLLMENTDATAINVALID | Looks like the server isn't correctly configured. You can try to do this again or contact your system administrator with the error code {0}. |
| "rejectedTermsOfUse" | "idErrorRejectedTermsOfUse" | Your organization requires that you agree to the Terms of Use. Please try again or ask your support person for more information. |
| 0x801c0001 | "idErrorServerConnectivity", // DSREG_E_DEVICE_MESSAGE_FORMAT_ERROR | There was an error communicating with the server. You can try to do this again or contact your system administrator with the error code {0} |
| 0x801c0002 | "idErrorAuthenticationFailure", // DSREG_E_DEVICE_AUTHENTICATION_ERROR | There was a problem authenticating your account or device. You can try to do this again or contact your system administrator with the error code {0}. |
| 0x801c0003 | "idErrorAuthorizationFailure", // DSREG_E_DEVICE_AUTHORIZATION_ERROR | This user isn't authorized to enroll. You can try to do this again or contact your system administrator with the error code {0}. |
| 0x801c0006 | "idErrorServerConnectivity", // DSREG_E_DEVICE_INTERNALSERVICE_ERROR | There was an error communicating with the server. You can try to do this again or contact your system administrator with the error code {0} |
| 0x801c000B | "idErrorUntrustedServer", // DSREG_E_DISCOVERY_REDIRECTION_NOT_TRUSTED | The server being contacted isn't trusted. Contact your system administrator with the error code {0}. |
| 0x801c000C | "idErrorServerConnectivity", // DSREG_E_DISCOVERY_FAILED | There was an error communicating with the server. You can try to do this again or contact your system administrator with the error code {0} |
| 0x801c000E | "idErrorDeviceLimit", // DSREG_E_DEVICE_REGISTRATION_QUOTA_EXCCEEDED | Looks like there are too many devices or users for this account. Contact your system administrator with the error code {0}. |
| 0x801c000F | "idErrorDeviceRequiresReboot", // DSREG_E_DEVICE_REQUIRES_REBOOT | A reboot is required to complete device registration. |
| 0x801c0010 | "idErrorInvalidCertificate", // DSREG_E_DEVICE_AIK_VALIDATION_ERROR | Looks like you have an invalid certificate. Contact your system administrator with the error code {0}. |
| 0x801c0011 | "idErrorAuthenticationFailure", // DSREG_E_DEVICE_ATTESTATION_ERROR | There was a problem authenticating your account or device. You can try to do this again or contact your system administrator with the error code {0}. |
| 0x801c0012 | "idErrorServerConnectivity", // DSREG_E_DISCOVERY_BAD_MESSAGE_ERROR | There was an error communicating with the server. You can try to do this again or contact your system administrator with the error code {0} |
| 0x801c0013 | "idErrorAuthenticationFailure", // DSREG_E_TENANTID_NOT_FOUND | There was a problem authenticating your account or device. You can try to do this again or contact your system administrator with the error code {0}. |
| 0x801c0014 | "idErrorAuthenticationFailure", // DSREG_E_USERSID_NOT_FOUND | There was a problem authenticating your account or device. You can try to do this again or contact your system administrator with the error code {0}. |









