Notitie
Voor toegang tot deze pagina is autorisatie vereist. U kunt proberen u aan te melden of de directory te wijzigen.
Voor toegang tot deze pagina is autorisatie vereist. U kunt proberen de mappen te wijzigen.
Cloaking is een COM-beveiligingsmogelijkheid die bepaalt welke identiteit de client tijdens imitatie naar de server projecteert. Wanneer cloaking is ingesteld, maskeert de tussenliggende server zijn eigen identiteit en presenteert hij de identiteit van de cliënt aan de server die hij namens de cliënt aanroept. Essentieel; de clientidentiteit die door de server wordt gezien, is de identiteit die is gekoppeld aan de proxy. De identiteit van de proxy wordt bepaald door verschillende factoren, waarvan één het type cloaking is dat is ingesteld (indien van toepassing). Cloaking wordt niet ondersteund door de Schannel-beveiligingsprovider.
De volgende onderwerpen bevatten meer informatie over het klonen:
- typen cloaking-
- hoe cloaking van invloed is op clientidentiteit
- Verhulling van instellen
- Verhullings- en identiteitswaardes
- Cloaking Scenarios
- Verwante onderwerpen
Soorten cloaking
Er zijn twee soorten cloaking: statische verhulling en dynamische verhulling.
- Met statische cloaking (EOAC_STATIC_CLOAKING) ziet de server het threadtoken van de eerste aanroep van een client naar de server. Als voor de eerste aanroep de proxy-identiteit eerder is ingesteld tijdens een aanroep naar CoSetProxyBlanket, wordt die proxy-identiteit gebruikt. Als de proxy-identiteit echter niet eerder is ingesteld, wordt het threadtoken gebruikt. Als er geen threadtoken aanwezig is, wordt het procestoken gebruikt. Voor alle toekomstige aanroepen wordt de identiteit die is ingesteld voor de eerste aanroep gebruikt.
- Bij dynamische cloaking (EOAC_DYNAMIC_CLOAKING) wordt bij elke aanroep het huidige threadtoken (als er een threadtoken is) gebruikt om de identiteit van de client te bepalen. Als er geen threadtoken is, wordt het procestoken gebruikt. Dit betekent dat servers die namens de client worden aangeroepen tijdens imitatie de identiteit zien van de COM-client die afkomstig is van de aanroep, wat over het algemeen het gewenste gedrag is. (Voor een geslaagde imitatie moet de client de serverautoriteit hebben gegeven om zich te imiteren door een geschikt imitatieniveau in te stellen. Zie imitatieniveausvoor meer informatie.) Dit soort cloaking is duur.
Hoe cloaking van invloed is op clientidentiteit
Wanneer een versleutelde aanroep wordt gedaan en de server de client vraagt om de identiteit, wordt meestal de identiteit gekoppeld aan de proxy. (Soms voert de verificatieservice een vertaling uit van de echte identiteit, maar over het algemeen is de proxy-identiteit de identiteit die de server ziet.) De proxy geeft een identiteit weer voor de server die afhankelijk is van het type cloaking dat is ingesteld en andere factoren.
Samenvattend is de identiteit van de cliënt een functie van de verbergvlag ingesteld, het proces-token, de aanwezigheid of afwezigheid van een draad-token, en of de proxy-identiteit eerder is ingesteld. In de volgende tabel ziet u de resulterende proxy-identiteit (clientidentiteit) wanneer deze factoren variëren.
| Verborgen Vlaggen | Aanwezigheid van thread-token | Proxy-identiteit eerder ingesteld | Proxy-identiteit (clientidentiteit) |
|---|---|---|---|
| Cloaking niet ingesteld |
Het maakt me niets uit |
Het maakt me niets uit |
Token ofwel authenticatie-identiteit verwerken |
| EOAC_STATIC_CLOAKING |
Aanwezig |
Nee |
Threadtoken |
| EOAC_STATIC_CLOAKING |
Aanwezig |
Ja |
Huidige proxy-identiteit |
| EOAC_STATIC_CLOAKING |
Niet aanwezig |
Nee |
Procestoken |
| EOAC_STATIC_CLOAKING |
Niet aanwezig |
Ja |
Huidige proxy-identiteit |
| EOAC_DYNAMIC_CLOAKING |
Aanwezig |
Het maakt me niets uit |
Threadtoken |
| EOAC_DYNAMIC_CLOAKING |
Niet aanwezig |
Het maakt me niets uit |
Procestoken |
In het volgende stroomdiagram ziet u hoe de proxy-identiteit in verschillende situaties wordt bepaald.

Cloaking instellen
Cloaking wordt ingesteld als een capabiliteitsvlag in een aanroep naar CoInitializeSecurity, waardoor cloaking voor het hele proces wordt geactiveerd. De cloaking-mogelijkheid wordt vervolgens ingesteld totdat de client deze wijzigt via een aanroep naar IClientSecurity::SetBlanket (of CoSetProxyBlanket), waarmee cloaking voor de proxy wordt ingesteld.
Cloaking is standaard niet ingesteld. Als u dit wilt instellen, geeft u EOAC_STATIC_CLOAKING of EOAC_DYNAMIC_CLOAKING door aan de parameter pCapabilities in CoInitializeSecurity of SetBlanket.
Wanneer statische cloaking is ingeschakeld met behulp van CoInitializeSecurity, haalt elke proxy een token (thread of proces) op wanneer u de eerste keer een aanroep uitvoert op de proxy. Wanneer statische cloaking is ingeschakeld met behulp van SetBlanket, haalt de proxy het token op de thread op dat moment op. Als er geen threadtoken beschikbaar is wanneer SetBlanket- wordt aangeroepen, wordt het procestoken gebruikt voor de identiteit van de proxy. In principe bevestigt SetBlanket de identiteit van de proxy.
Met dynamische cloaking wordt de identiteit van de proxy op dezelfde manier bepaald, ongeacht of dynamische cloaking is ingesteld met behulp van CoInitializeSecurity of met SetBlanket. Het huidige threadtoken wordt gebruikt als er een is; anders wordt het procestoken gebruikt.
Als cloaking is ingesteld voor het hele proces via een aanroep naar CoInitializeSecurity en u oproepen wilt doen met het procestoken, moet u niet impersoneren tijdens het maken van oproepen.
Cloaking- en imitatieniveaus
Zoals eerder vermeld, bepaalt de cloaking-mogelijkheid welke identiteit tijdens imitatie aan een server wordt gepresenteerd. Cloaking biedt een manier voor een server om een andere identiteit dan een eigen identiteit te projecteren op een andere server die namens de client wordt aangeroepen. Het impersonatieniveau geeft aan hoeveel bevoegdheid de client aan de server heeft gegeven.
Imitatie zonder cloaking werkt, maar het is mogelijk niet de beste keuze, omdat in sommige gevallen de uiteindelijke server de identiteit van de initiële beller moet kennen. Dit kan niet worden bereikt zonder cloaking te gebruiken, omdat het moeilijk is om ervoor te zorgen dat alleen geautoriseerde clients toegang hebben tot een externe computer. Wanneer imitatie wordt gebruikt zonder verbergen, is de identiteit die aan een downstreamserver wordt gepresenteerd die van het directe aanroepende proces.
Cloaking is echter niet nuttig zonder nabootsing. Cloaking is alleen zinvol wanneer de client een imitatieniveau van nabootsen of delegeren heeft ingesteld. (Met lagere imitatieniveaus kan de server geen cloaked-aanroepen maken.) Of cloaking geslaagd is, is afhankelijk van het aantal overschreden computergrenzen en het imitatieniveau, wat aangeeft hoeveel bevoegdheid de server heeft om namens de client te handelen.
In sommige situaties is het logisch dat de server cloaking instelt wanneer de client het niveau van imitatie instelt op RPC_C_IMP_LEVEL_IMPERSONATE. Bepaalde beperkingen zijn echter van kracht. Als de oorspronkelijke client het imitatieniveau instelt op RPC_C_IMP_LEVEL_IMPERSONATE, kan de tussenliggende server (die fungeert als een client op dezelfde computer) slechts over één computergrens klonen. Dit komt doordat een imitatieniveau-token slechts over één computer kan worden doorgegeven. Nadat de computergrens is overschreden, kunnen alleen lokale resources worden geopend. De identiteit die aan de server wordt gepresenteerd, is afhankelijk van het type cloaking dat is ingesteld. Als er geen cloaking is ingesteld, is de identiteit die aan een server wordt gepresenteerd, dat van het proces dat de directe aanroep doet.
Om meerdere computergrenzen af te schermen, moet u zowel een geschikte afschermingsmogelijkheidenvlag als een gedelegeerdenniveau-immitatie specificeren. Met dit type imitatie worden zowel de lokale als de netwerkreferenties van de client aan de server gegeven, zodat het imitatietoken een willekeurig aantal computergrenzen kan overschrijden. Nogmaals, de identiteit die aan de server wordt gepresenteerd, is afhankelijk van het type cloaking dat is ingesteld. Als er geen cloaking is ingesteld met imitatie op gemachtigde niveau, is de identiteit die aan een server wordt gepresenteerd dat van het proces dat de aanroep doet.
Stel dat Proces A B aanroept en B C aanroept. B heeft cloaking ingesteld en A heeft het impositieniveau ingesteld op imitatieniveau. Als A, B en C zich op dezelfde computer bevinden, werkt het doorgeven van het imitatietoken van A naar B en vervolgens naar C. Maar als A en C zich op dezelfde computer bevinden en B niet, werkt het doorgeven van het token tussen A en B, maar niet van B naar C. De aanroep van B naar C mislukt omdat B geen C kan aanroepen tijdens het klonen. Als A echter het imitatieniveau instelt om te delegeren, kan het token worden doorgegeven van B naar C en kan de aanroep lukken.
Scenario's voor verhulling
In de volgende afbeelding roept Proces A B aan, roept C aan, roept D aan wanneer cloaking niet is ingesteld. Als gevolg hiervan herkent elk tussenliggend proces de identiteit van het proces dat het heeft aangeroepen.
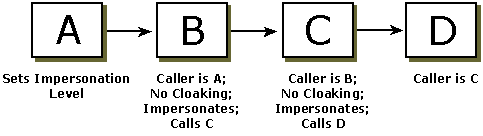
Bij statische cloaking ziet de server de proxy-identiteit die is ingesteld tijdens de eerste aanroep van de client naar de server. In de volgende afbeelding ziet u een voorbeeld van de proxy-identiteit die wordt ingesteld tijdens een aanroep van B naar C. Bij een volgende aanroep ziet Process D de identiteit van B wanneer statische cloaking is ingesteld door B en C.

Bij dynamische verhulling is de identiteit van de beller tijdens nabootsing gebaseerd op het huidige threadtoken, indien aanwezig. In de volgende afbeelding ziet u de situatie waarin B en C dynamische cloaking instellen en D de identiteit van A ziet, ondanks een eerdere oproep van B naar C.

Verwante onderwerpen
-
nl-NL: Delegatie en impersonatie