Customer security best practices
Appropriate roles: Global Admin | Admin Agent | Helpdesk Agent
All customers of Cloud Solution Provider (CSP) partners should follow the security guidance in this article.
For security best practices for CSPs, see CSP security best practices.
Ensure multifactor authentication (MFA) is enabled and registered on every account. Use either Microsoft Entra ID security defaults or Conditional Access to enforce MFA. MFA is the best baseline security hygiene method to protect against threats.
- Consider using passwordless sign-in with the Microsoft Authenticator app.
Frequently review subscriptions and resources or services that might have been provisioned unexpectedly.
- Review the Azure Monitor activity log for Azure subscription-related activity.
Utilize cost anomaly alerts to detect unexpected high consumption in your Azure subscription.
Users who have Microsoft Entra administrative roles such as Global Administrator or Security Administrator should not be regularly used for email and collaboration. Create a separate user account with no Microsoft Entra administrative roles for collaboration tasks.
Regularly review and verify password recovery email addresses and phone numbers within Microsoft Entra ID for all users with the Global Admin roles and update if necessary.
Review, audit, and minimize access privileges and delegated permissions. It's important to consider and implement a least-privilege approach. Microsoft recommends prioritizing a thorough review and audit of partner relationships to minimize any unnecessary permissions between your organization and upstream providers. Microsoft recommends immediately removing access for any partner relationships that look unfamiliar or haven't yet been audited.
Review, harden, and monitor all tenant administrator accounts: All organizations should thoroughly review all tenant admin users, including users associated with Administer On Behalf Of (AOBO) in Azure subscriptions, and verify the authenticity of the users and activity. We strongly encourage the use of phishing-resistant MFA for all tenant administrators, review of devices registered for use with MFA, and minimizing the use of standing high-privilege access. Continue to reinspect all active tenant admin users accounts, and check audit logs regularly to verify that high-privilege user access isn't granted or delegated to admin users who don't require those privileges to do their jobs.
Review service provider permissions access from B2B and local accounts: In addition to using delegated administrative privilege capabilities, some cloud service providers use business-to-business (B2B) accounts or local administrator accounts in customer tenants. We recommend that you identify whether your cloud service providers use these accounts, and if so, ensure that those accounts are well governed and have least-privilege access in your tenant. Microsoft recommends against the use of "shared" administrator accounts. Review the detailed guidance on how to review permissions for B2B accounts.
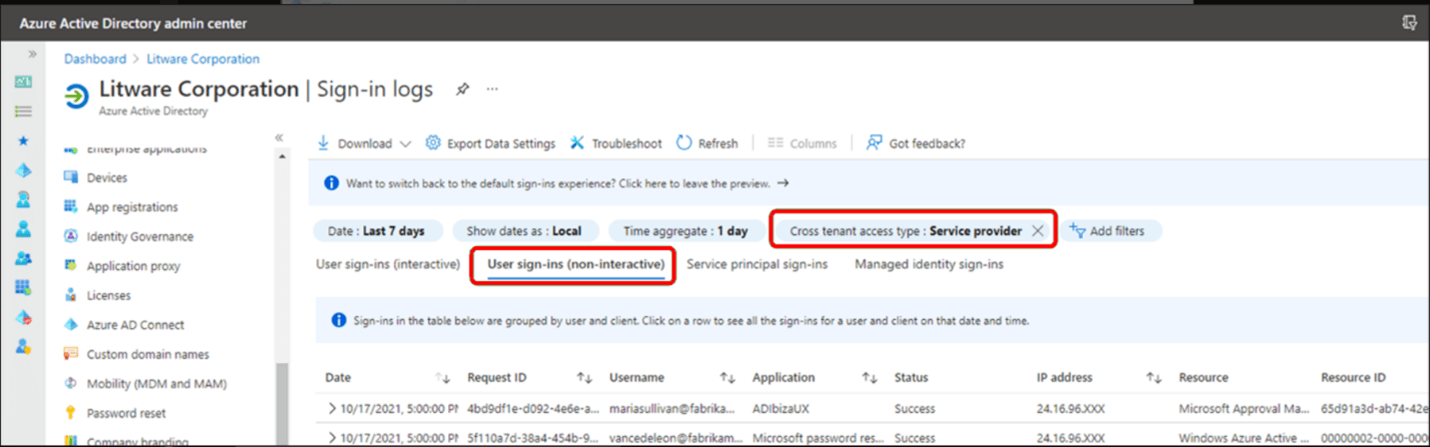
Review and audit Microsoft Entra sign-ins and configuration changes: Authentications of this nature are audited and available to customers through the Microsoft Entra sign-in logs, Microsoft Entra audit logs, and the Microsoft Purview compliance portal (formerly in the Exchange Admin Center). We recently added the capability to see sign-ins by partners who have delegated admin permissions. You can see a filtered view of those sign-ins by going to the sign-in logs in the Microsoft Entra admin center and adding the filter Cross-tenant access type: Service provider on the User-sign ins (non-interactive) tab.
Review existing log availability and retention strategies: Investigating activities conducted by malicious actors places a large emphasis on having adequate log-retention procedures for cloud-based resources, including Microsoft 365. Various subscription levels have individualized log availability and retention policies, which are important to understand before forming an incident response procedure.
We encourage all organizations to become familiar with the logs made available within your subscription and to evaluate them routinely for adequacy and anomalies. For organizations relying on a third-party organization, work with them to understand their logging strategy for all administrative actions and establish a process should logs need to be made available during an incident.
See also
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for