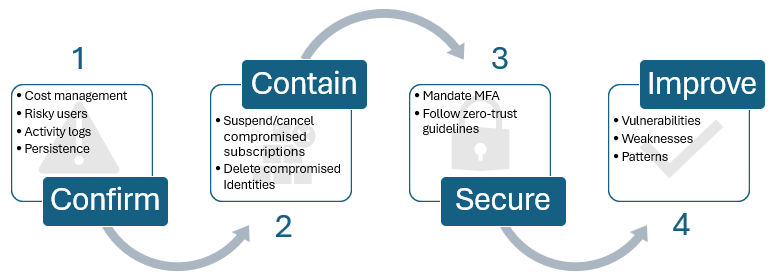
Essential steps to confirm, contain, and secure a compromise
Appropriate roles: Admin agent | Security contact
This article helps you take actions to confirm, contain, and secure a compromise.
- Confirm:
- Review the Azure subscriptions that are compromised and check for the spending anomalies. For more information, see Microsoft cost management.
- Conduct thorough investigations examining the risky users and Azure Monitor activity logs to confirm the compromise and contain the exposure immediately. It's important to note that any persistence methods missed during the investigation could result in continued access by the attacker, which could lead to a potential recompromise. Therefore, it's essential to be meticulous in your investigation to prevent any future attacks.
- Contain:
- If you determine that a customer is compromised and there's fraud-in-flight, you can try to work with the customer or take unilateral action to cancel the subscription. You can start by immediately canceling the Azure subscriptions that are confirmed to contain the compromise. Then, take the required steps to identify and evict the threat actor quickly. For more information, see how to quickly remediate the compromised identities.
- Secure:
- When the abuse is contained, you should do the work to secure the tenant. Follow the best practice guidelines for Cloud Solution Providers and customer tenants. For more information, see the instructions on how to address security alerts.
- Improve:
- Take some time to investigate and understand how the compromise occurred. Doing so might uncover weaknesses in your overall security posture that can be remediated.
For more info, see support.
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for