Advanced Customization of ADFS for Cloud Usage (Part 2 of 4)
Advanced Customization of ADFS for Cloud Usage
Written by Kevin Saye
This is part 2 of a 4 part blog about customizing Microsoft’s ADFS for advanced user scenarios. I will break down this series into the following parts:
| Part 1 – Customizing the Login Page | Customizing the Login Page for advanced features. We will add icons and have automated presentation logic. |
Part 2 – Using Cloud or on Premises MFA |
What changes happen in the claims and how to control where MFA takes place. |
Part 3 – User Certificates |
Enabling enrollment and usage of user certificates for ADFS. |
Part 4 – Expired Passwords |
How to detect and address users with expired passwords. |
Part 2 – Using Cloud or on Premises MFA:
As documented here: https://msdn.microsoft.com/en-us/library/azure/dn394284.aspx, you can use either Azure Multi-Factor Server (on Premises) or Azure Multi-Factor Authentication (cloud based) to perform Multi-Factor for Federated (ADFS) users. Azure will honor both, as long as the “multi-factor” claim is passed from ADFS to Azure when using Azure Multi-Factor Server.
While it is not the purpose of this blog to discuss installation, it is the purpose to discuss logic and claims needed.
Two items we need to discuss before we understand the logic:
PowerShell: Set-MsolDomainFederationSettings with the –SupportsMFA parameter
Claim: Authentication Method References (https://schemas.microsoft.com/claims/authnmethodsreferences)
Domain Federation Setting:
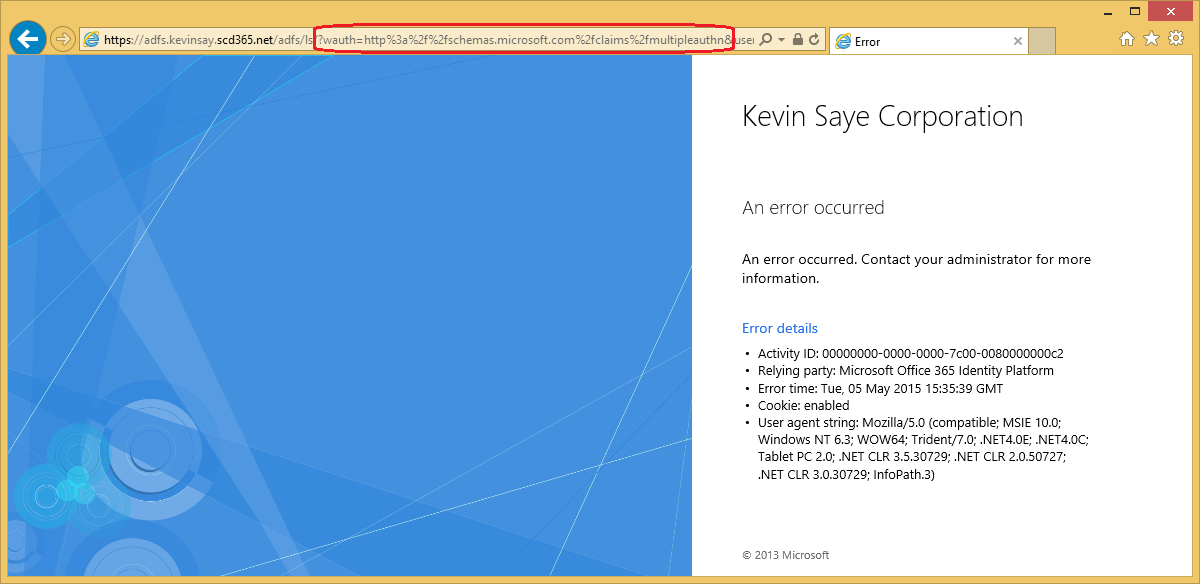
Each Federated Domain can be configured to support MFA at the Claims Provider (ADFS Server). To change this setting, simply run the Set-MsolDomainFederationSettings to toggle the setting between true and false. More information here: https://msdn.microsoft.com/en-us/library/azure/dn194088.aspx. If the setting is True, and Azure (through configuration) required Multi-Factor, Azure will redirect to the Claims Provider (ADFS) setting the query string: wauth=http%3a%2f%2fschemas.microsoft.com%2fclaims%2fmultipleauthn and expecting the return claim https://schemas.microsoft.com/claims/authnmethodsreferences set to the value of https://schemas.microsoft.com/claims/multipleauthn.
Authentication Method Claim:
As discussed above, if leveraging Azure Multi-Factor Server integrated with your ADFS server, the claim https://schemas.microsoft.com/claims/authnmethodsreferences should be set to the value of https://schemas.microsoft.com/claims/multipleauthn to indicate that MFA has been performed. This claim is not enabled by default on your ADFS server to be sent to Azure, called “Microsoft Office 365 Identity Platform”.
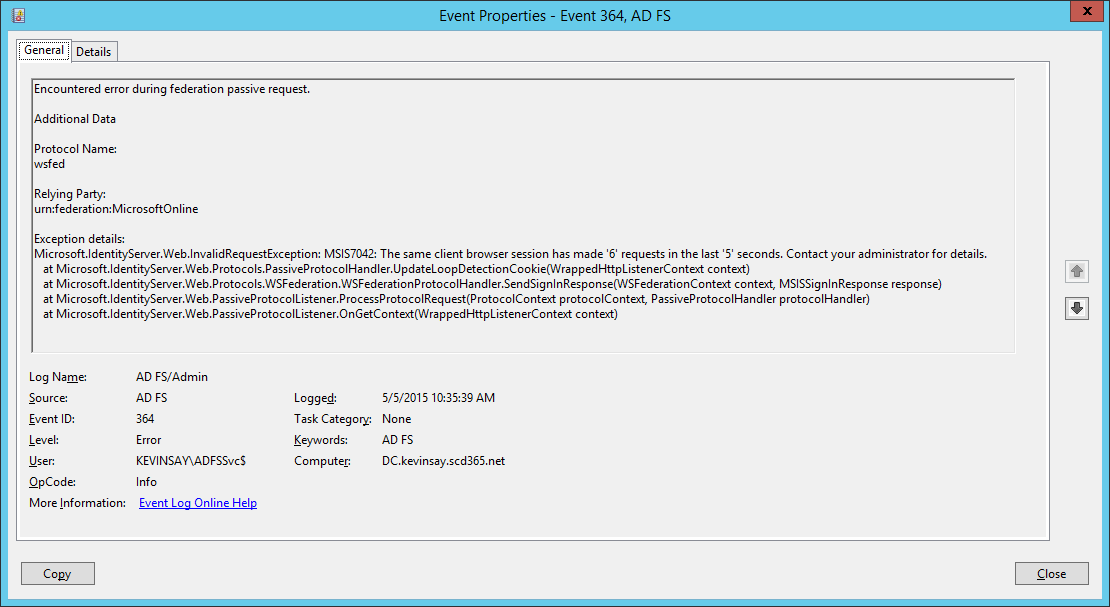
If the claim is not “issued” on the ADFS server, Azure and ADFS will just loop until ADFS throws a loop detection error (Microsoft.IdentityServer.Web.Protocols.PassiveProtocolHandler.UpdateLoopDetectionCookie) as shown below. Notice the “wauth=http%3a%2f%2fschemas.microsoft.com%2fclaims%2fmultipleauthn” meaning Azure asked ADFS to perform MFA. This error can also occur if there are no MFA providers configured in ADFS.
You will get event log error: 365 with the description: Microsoft.IdentityServer.Web.InvalidRequestException: MSIS7042: The same client browser session has made ….
To resolve this, enable the claim https://schemas.microsoft.com/claims/authnmethodsreferences on your Azure Relying Party (discussed next).
Enabling the Authentication Method References in ADFS:
To enable the claim to be sent from ADFS to Azure, follow these steps:
Open the AD FS Management console on your ADFS Server.
Select AD FS à Trust Relationships à Relying Party Trust
Right click on “Microsoft Office 365 Identity Platform” or whatever you have named the Azure Relying Party and select Edit Claim Rules
Click Add Rule on the Issuance Transform Rules tab
Select the rule template Pass Through or Filter an Incoming Claim and click next
In the incoming claim type, select Authentication Methods References and leave Pass through all claim values selected and click Finish
Click OK to save the Claims Rules
Now any Azure service that requires Multi-Factor will honor the https://schemas.microsoft.com/claims/authnmethodsreferences claim.
How to use both Azure Multi-Factor Server and Azure Multi-Factor Authentication
In some cases, you may want to use Multi-Factor Server for some users and Multi-Factor Authentication for others.
If you want to support both Multi-Factor Server and Multi-Factor Authentication for a single Federated domain, follow these steps:
Use the “Set-MsolDomainFederationSettings” command and set the –SupportMFA to $false
Enable a MFA provider in ADFS
Enforce the MFA requirement on the desired users in ADFS
4. Enable the Authentication Methods References claim in ADFS
Following this method, any user who authenticates through ADFS will be MFA challenged at ADFS initial login time. Azure will honor the Authentication Methods References claim set by ADFS for these users. If a user does not have the claim Authentication Methods References set to https://schemas.microsoft.com/claims/multipleauthn via ADFS, Multi-Factor Authentication will perform a cloud based Multi-Factor authentication.