Intune Application Protection Policy (APP) formally known as Microsoft Managed Application Management (MAM) – Creating a blank policy
Several months ago we released APP capability into Intune. Previously, the most common model for securing and managing mobile devices (either corporate-owned or personally-owned) was to require the device to enroll into an MDM solution. After enrollment, IT policies are applied to the device and apps, and then end users are allowed to access corporate data from those devices. With the new Intune MAM without enrollment feature, there is now a choice.
With APP we don’t need to enroll the device we can just apply policy to the application for example Outlook. When the user is using Outlook for personal email then we leave them alone when they go into their corporate email though that is when we apply policy rules around what they can do. This could be anything from making them enter a pin to access the data, checking their device isn’t jail broken or stopping them copying that corporate email to their personal email.
Take a look at this article around some of the cool features we can do with APP: https://blogs.technet.microsoft.com/enterprisemobility/2015/11/17/enhancing-managed-mobile-productivity/
And see
https://docs.microsoft.com/en-us/intune-azure/manage-apps/what-is-app-protection-policy
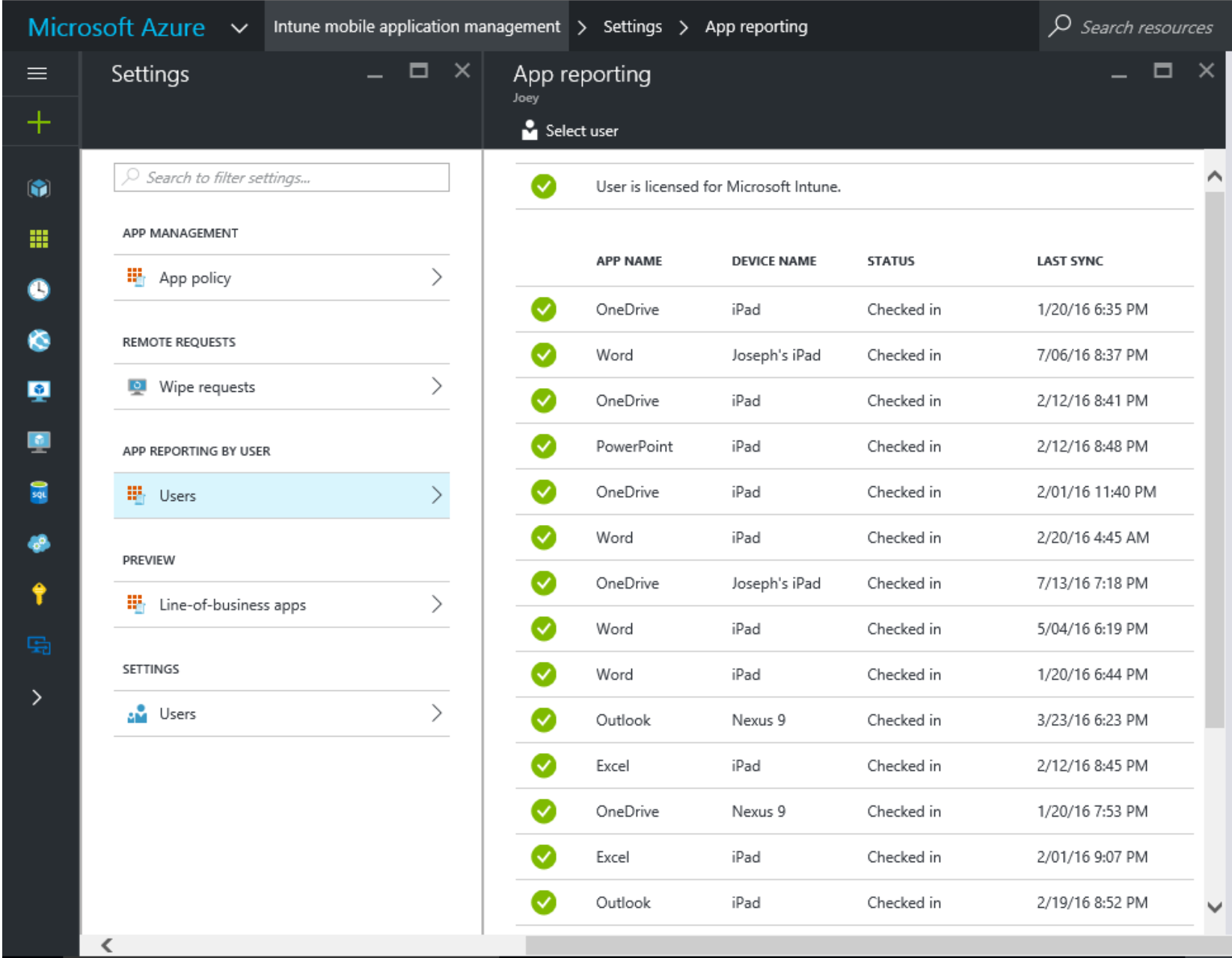
Now one of the abilities with this is we can create a policy that doesn’t have any restrictions, we basically create a blank one with no payload. Why would we want to do this? Well when the user goes into the corporate email they will get a message saying that they are corporately managed, but otherwise will notice no difference but in your azure portal you will get back information on who is accessing your email.
As you can see from the above we get all sorts of useful information around the user name, their device type and even when we last saw them.
So let’s create a blank policy, when you do this I would really recommend that you only assign the policy to a test group of users (more on how to do this later) to double check that you haven’t done anything to impact your users. Once you are confident everything is ok then we can assign it out to all users.
iOS Blank Policy
We are going to create an iOS policy but the same features are available for Android.
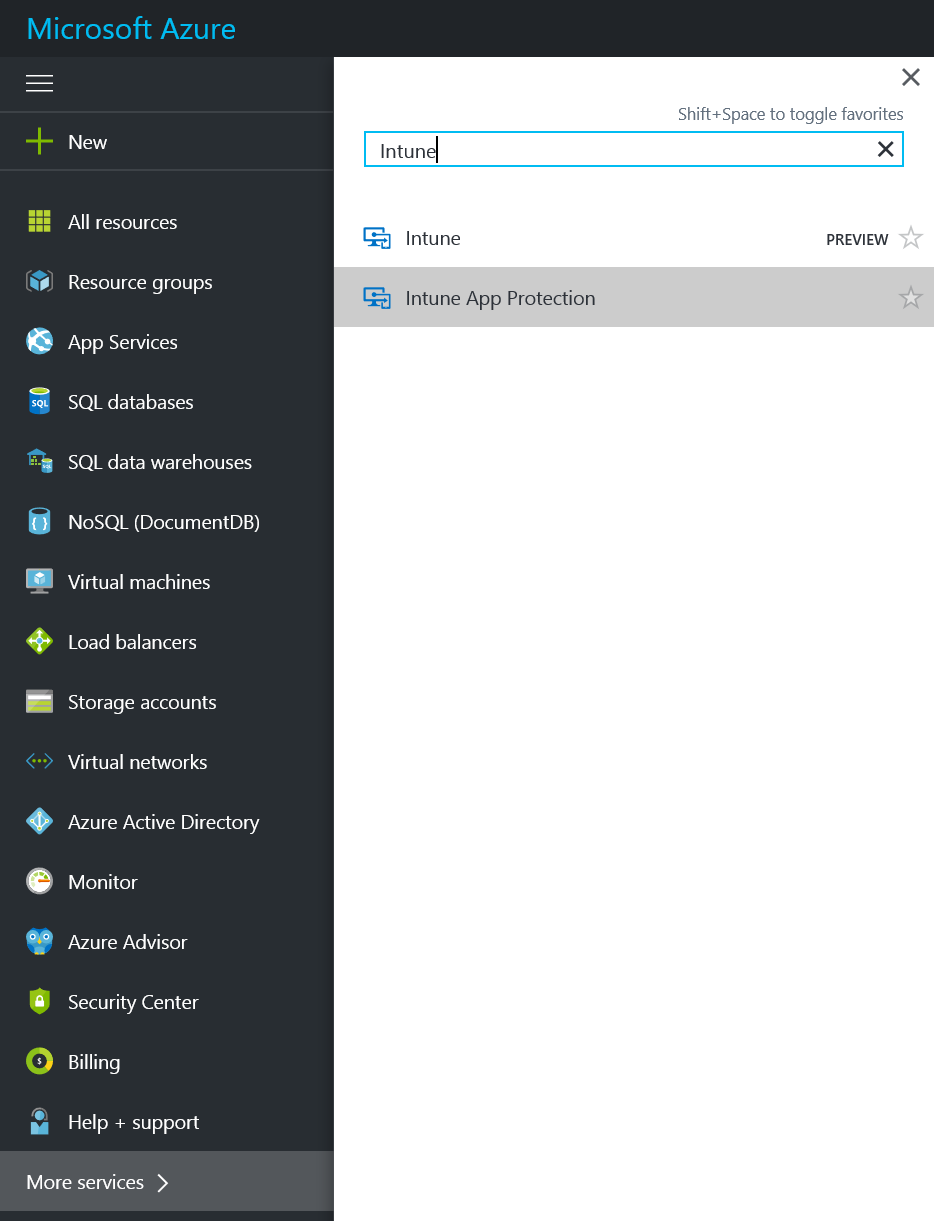
Log into the Azure portal https://portal.azure.com
Click on More Services and type in Intune and select Intune App Protection
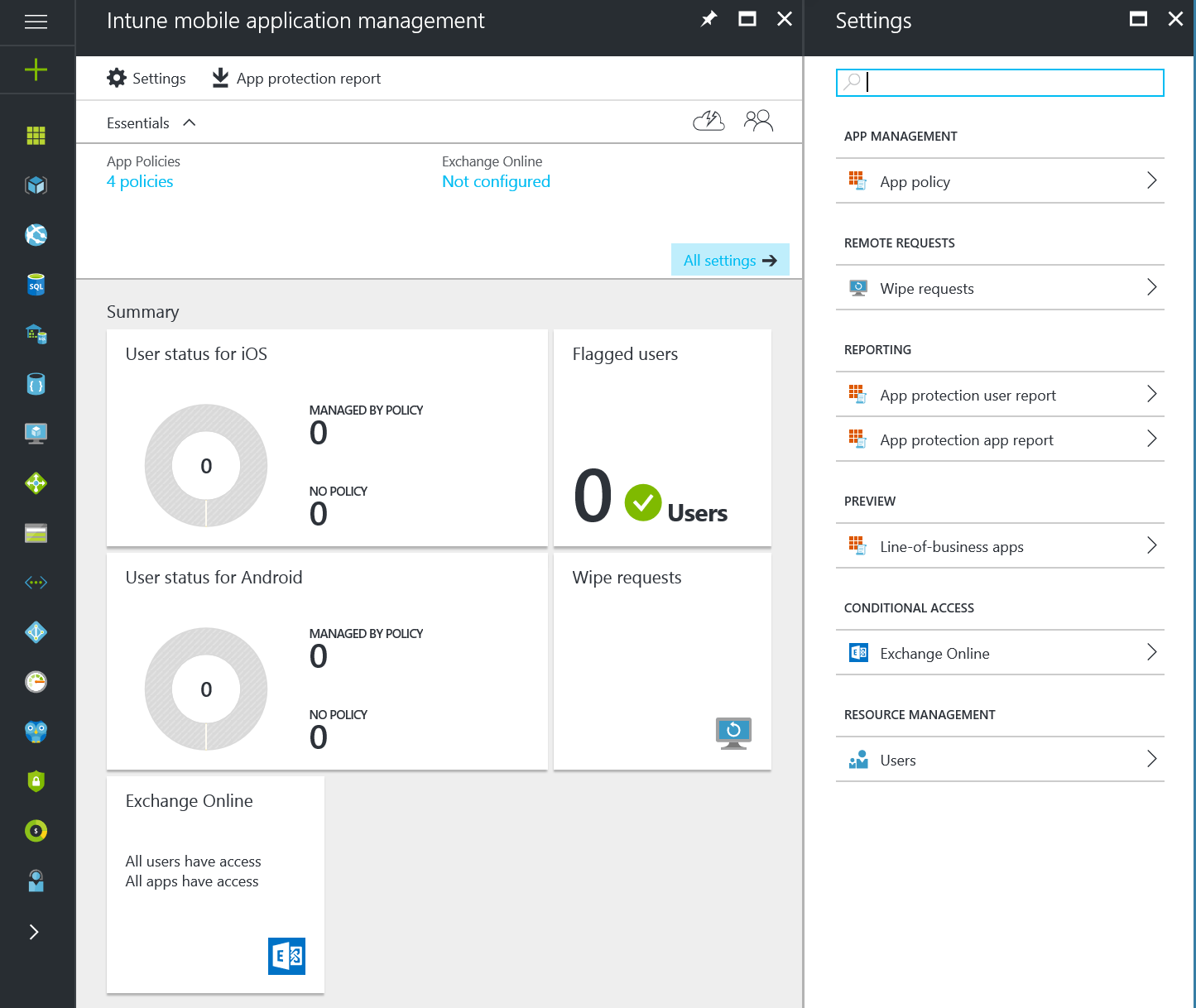
You will then see the Intune Mobile Application Management blade appear. As you can see I currently don’t have any devices enrolled. In the Settings blade click on App policy under the App Management section:
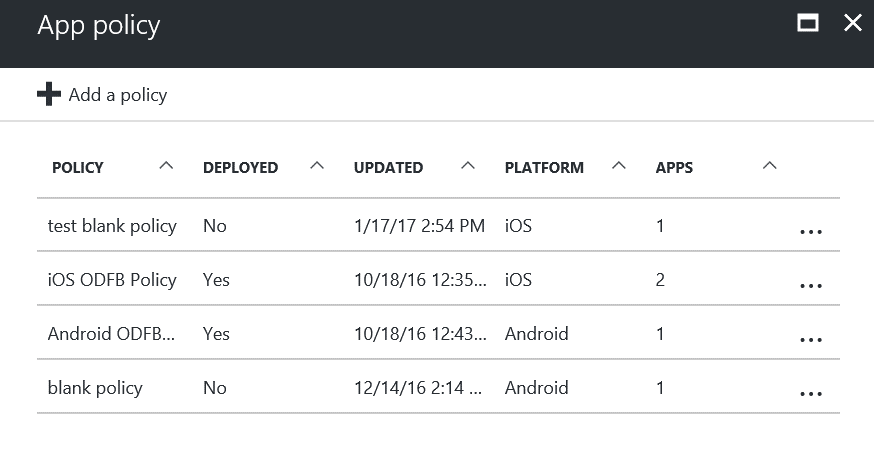
Now under App policy I can see we already have some policies but we are going to create a new one. Click on + Add a policy:
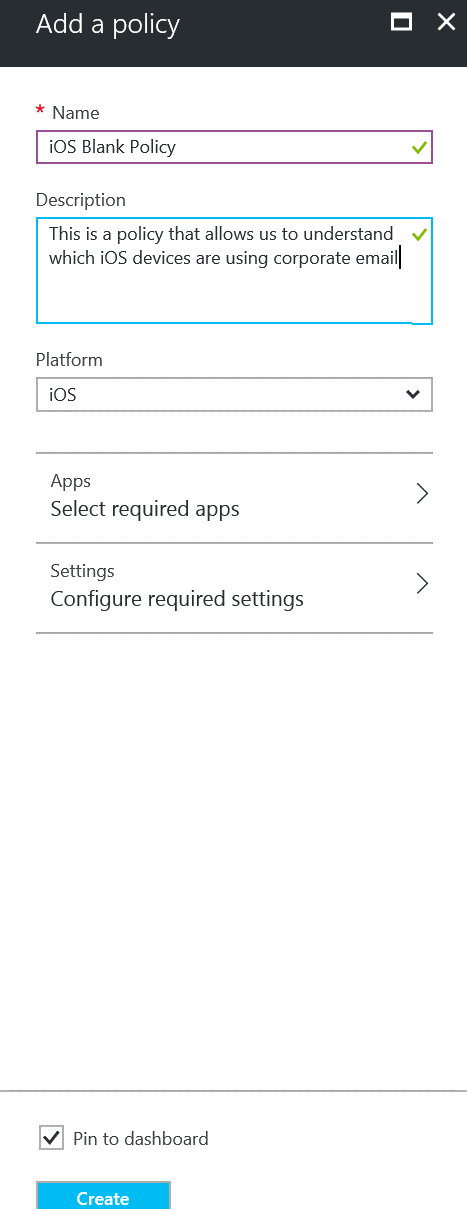
Lets create the new policy:
Give it a name iOS Blank Policy and a description This is a policy that allows us to understand which iOS devices are using corporate email
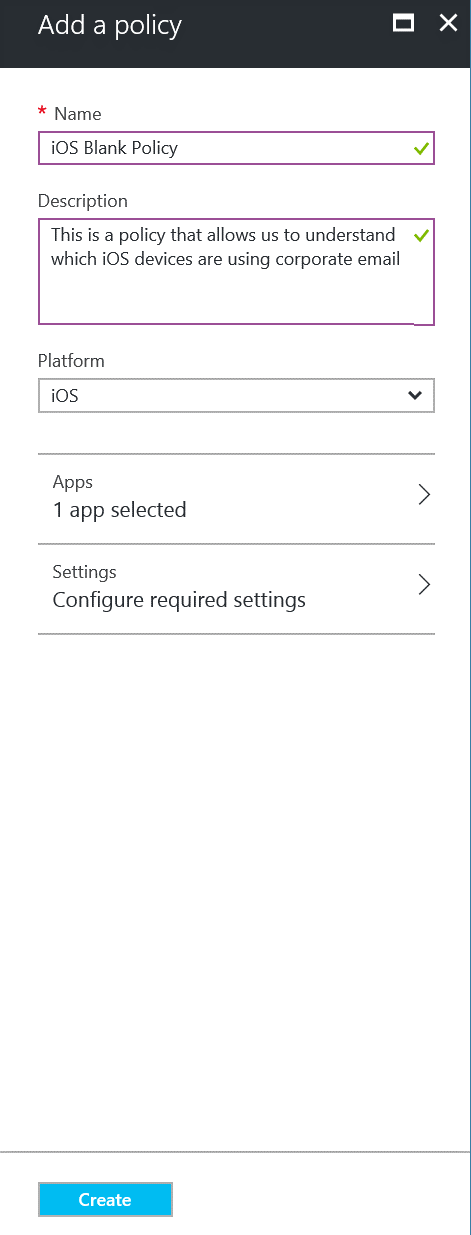
Select under Platform iOS and click the Apps section:
We could select multi apps to detect but let’s stick with Outlook.
Click on Outlook and click Select: 
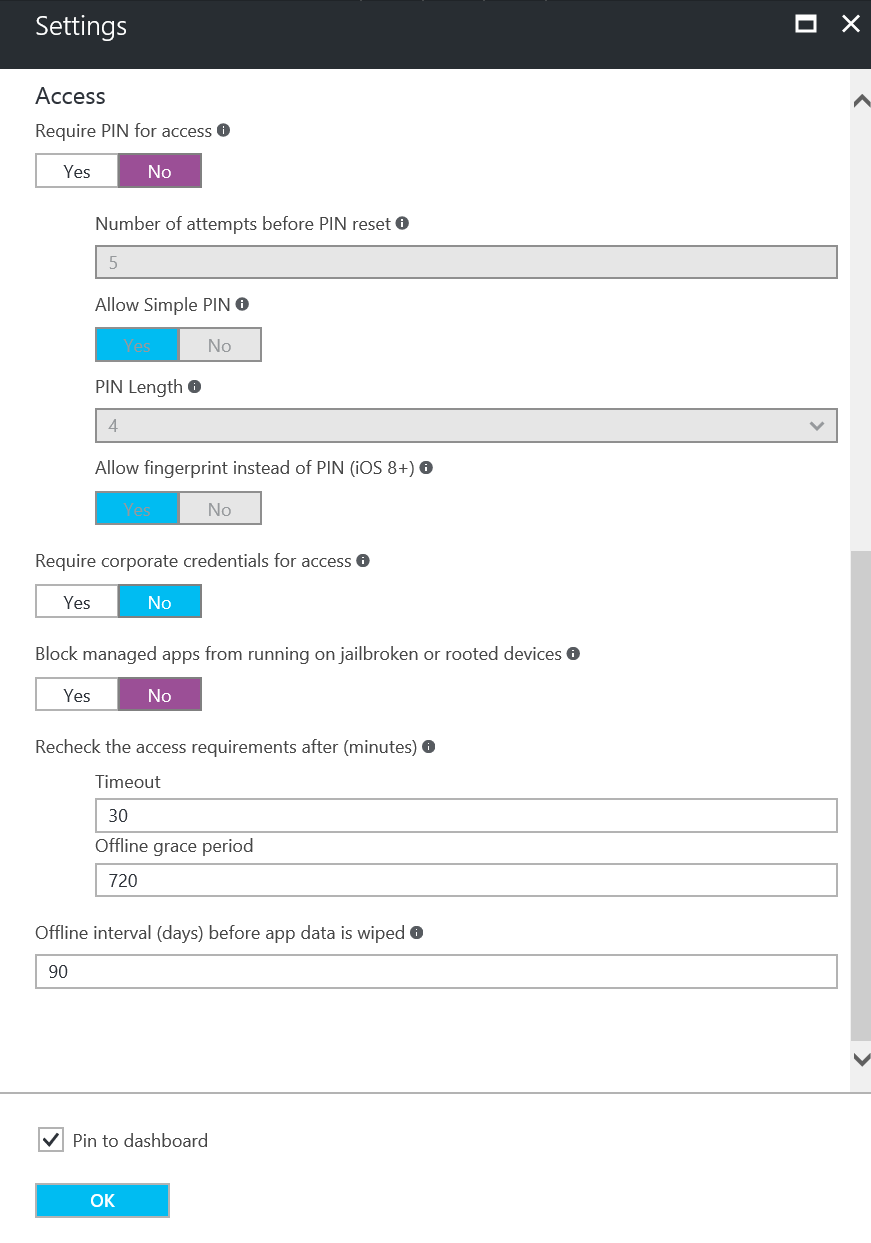
Settings (part1)
Configure the following settings as the image below shows: 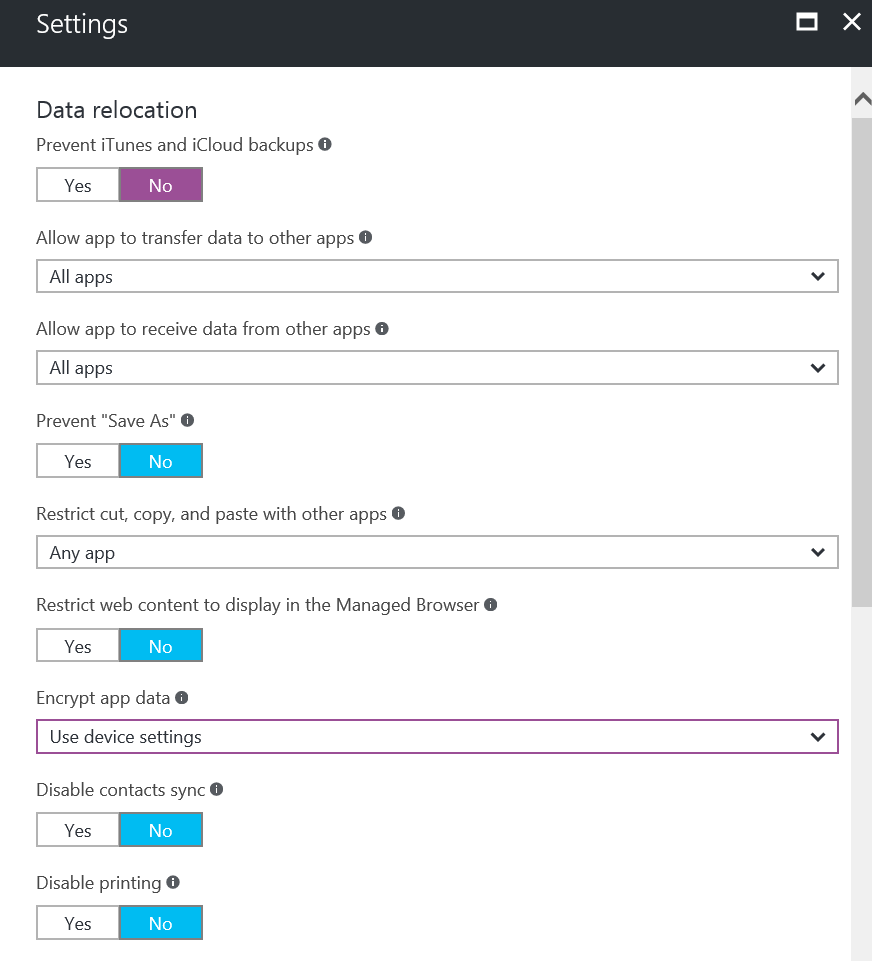
Settings (part2)
Configure the following settings as the image below shows then click OK:
Click Create:
Now we need a Test Group, Click on Active Directory in the application bar as highlighted below: 
Click on Users and Groups:
Click on All Groups:
Click the +Add button:
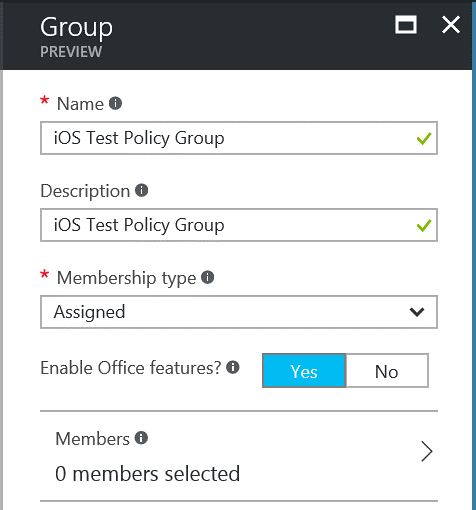
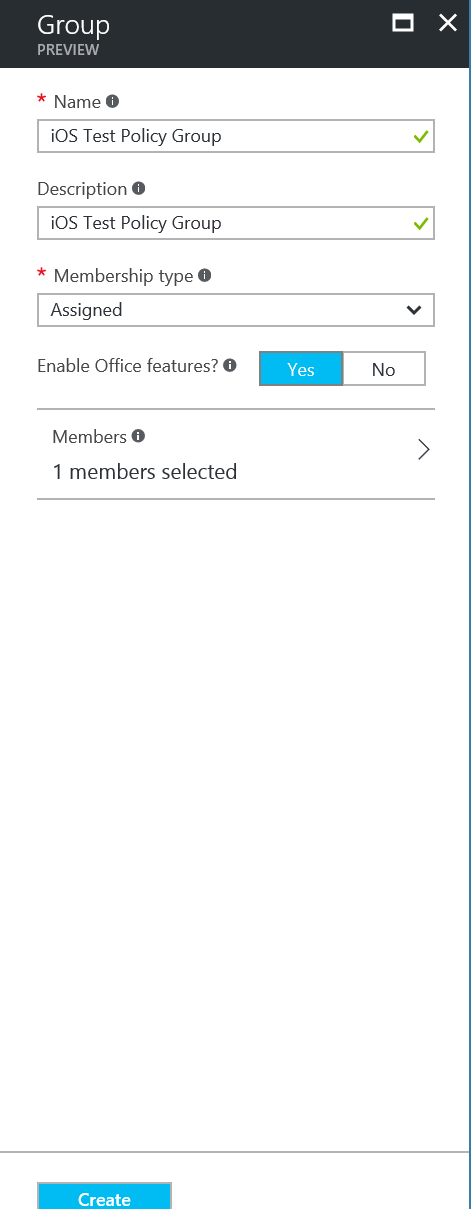
Enter a name for the Group iOS Test Policy Group, Description of iOS Test Policy Group and set Membership type to Assigned. Ensure Enable Office features are Yes. Click on Members:
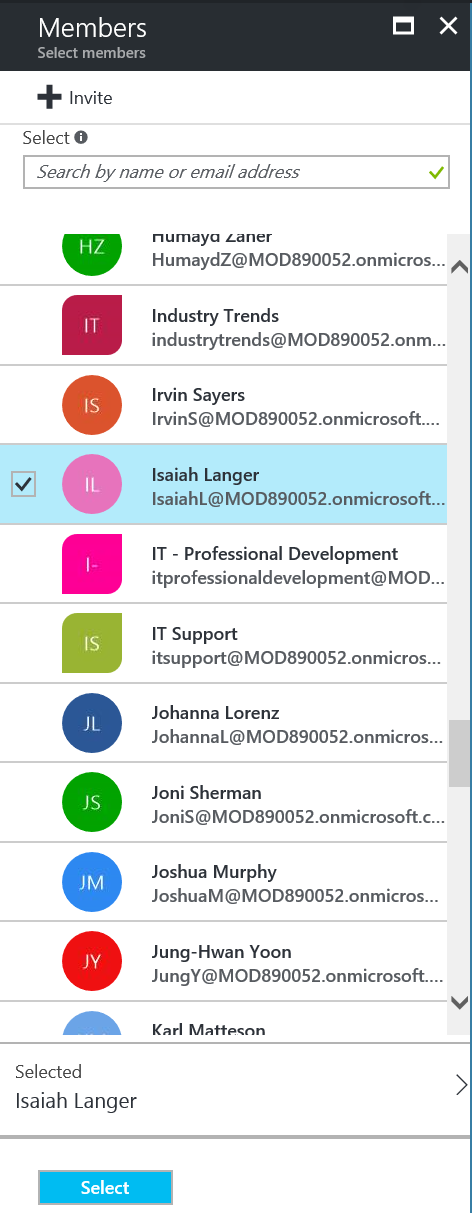
Click on a user or users you want to add. Click Select:
Click on Create:
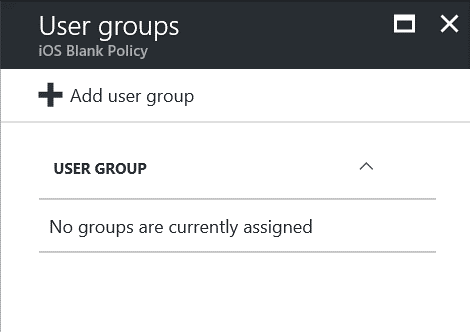
Back in the Intune Mobile application management blade under settings and App policy:
Click on … for our iOS Blank Policy and click Target User Groups: 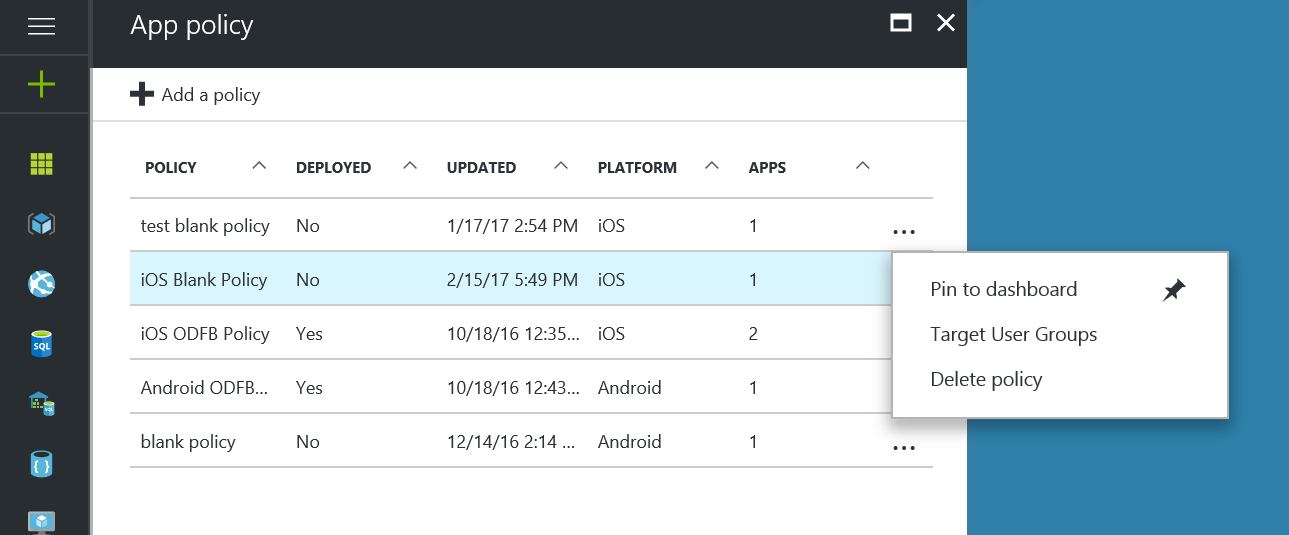
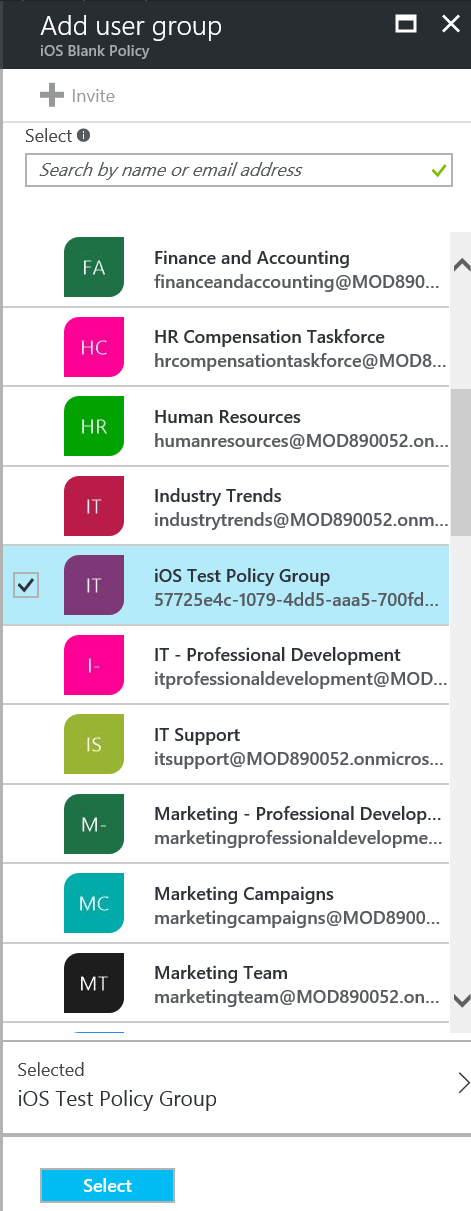
Find and select our new iOS Test Policy Group and click Select:
We should now have an active group: 
If the user(s) you selected are already using Outlook on their iOS device then in a short time we should get data. If not you need to go to your iOS device install Outlook from the Apple Store and add your company corporate credentials in to receive email on that device.
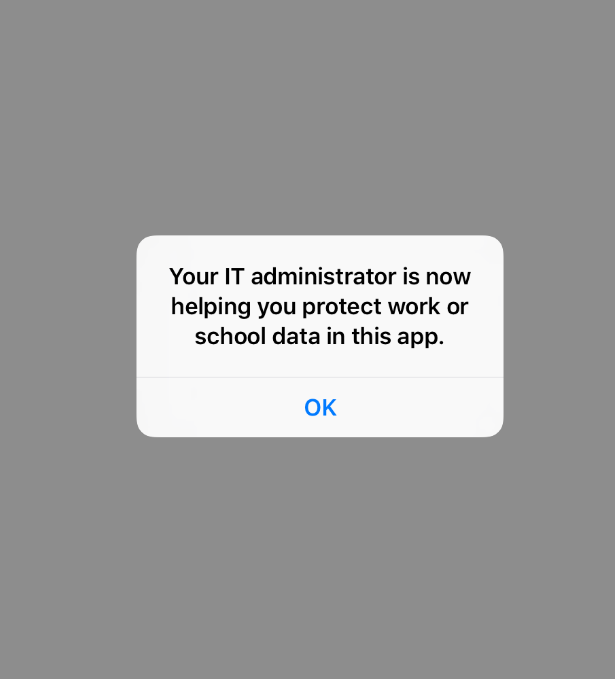
The user will see this message when they login:
You should now have some clients showing policy: 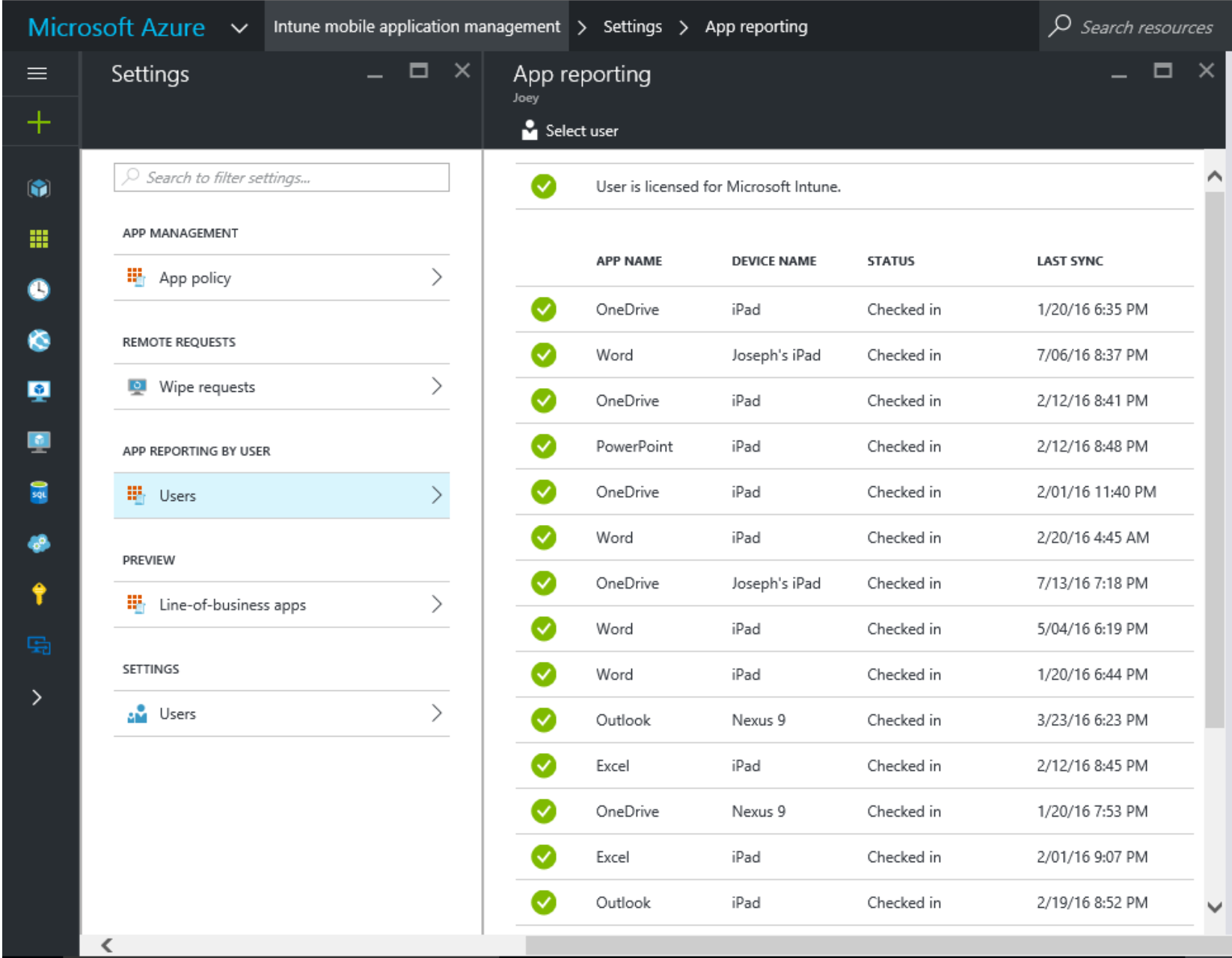
Also if you want to keep up to date on the latest and greatest with Intune:
/en-us/intune/whats-new/whats-new-in-microsoft-intune
Andy Taylor
Enterprise Mobility Technical Specialist Microsoft UK.