Secured-core to zbiór funkcji, które oferują wbudowane funkcje zabezpieczeń sprzętu, oprogramowania układowego, sterownika i systemu operacyjnego. W tym artykule przedstawiono sposób konfigurowania serwera z zabezpieczeniami rdzenia przy użyciu Centrum administracyjnego systemu Windows, środowiska pulpitu systemu Windows Server i zasad grupy.
Bezpieczny serwer podstawowy został zaprojektowany w celu zapewnienia bezpiecznej platformy dla krytycznych danych i aplikacji. Aby uzyskać więcej informacji, zobacz Co to jest serwer zabezpieczony-podstawowy?
Prerequisites
Przed skonfigurowaniem serwera typu secured-core należy mieć zainstalowane i włączone w BIOS następujące komponenty zabezpieczeń:
- Bezpieczny rozruch.
- Moduł TPM (Trusted Platform Module) 2.0.
- Oprogramowanie układowe systemu musi spełniać wymagania dotyczące ochrony DMA przed uruchomieniem i ustawiać odpowiednie flagi w tabelach ACPI, aby włączyć ochronę DMA jądra. Aby dowiedzieć się więcej na temat ochrony DMA jądra, zapoznaj się z ochrona DMA jądra (ochrona dostępu do pamięci) dla OEM-ów.
- Procesor z obsługą włączoną w ustawieniach BIOS:
- Rozszerzenia wirtualizacji.
- Jednostka zarządzania pamięcią wejściową/wyjściową (IOMMU).
- Dynamiczny korzeń zaufania dla pomiarów (DRTM).
- Funkcja Transparent Secure Memory Encryption jest również wymagana dla systemów opartych na technologii AMD.
Important
Włączenie każdej funkcji zabezpieczeń w systemie BIOS może się różnić w zależności od dostawcy sprzętu. Upewnij się, aby sprawdzić przewodnik producenta sprzętu dotyczący włączania serwera z zabezpieczonym rdzeniem.
Sprzęt certyfikowany dla serwera zabezpieczonego rdzenia można znaleźć w katalogu Windows Server, a serwery lokalne platformy Azure w katalogu lokalnym platformy Azure.
Włączanie funkcji zabezpieczeń
Aby skonfigurować serwer Zabezpieczony-core, należy włączyć określone funkcje zabezpieczeń systemu Windows Server, wybierz odpowiednią metodę i wykonaj kroki.
Poniżej przedstawiono sposób włączania serwera z zabezpieczonym rdzeniem przy użyciu interfejsu użytkownika.
- Na pulpicie systemu Windows otwórz menu Start , wybierz pozycję Narzędzia administracyjne systemu Windows, otwórz pozycję Zarządzanie komputerem.
- W obszarze Zarządzanie komputerem wybierz pozycję Menedżer urządzeń, w razie potrzeby rozwiąż wszelkie błędy urządzenia.
- W przypadku systemów opartych na amd przed kontynuowaniem upewnij się, że urządzenie sterownika rozruchu DRTM jest obecne
- Na pulpicie systemu Windows otwórz menu Start , wybierz pozycję Zabezpieczenia systemu Windows.
- Wybierz pozycję Zabezpieczenia urządzeń > Podstawowe szczegóły izolacji, a następnie włącz integralność pamięci i Firmware Protection. Nie można włączyć integralności pamięci do momentu włączenia ochrony oprogramowania układowego i ponownego uruchomienia serwera.
- Po wyświetleniu monitu uruchom ponownie serwer.
Po ponownym uruchomieniu Twój serwer został włączony jako serwer z zabezpieczonym rdzeniem.
Poniżej przedstawiono sposób włączania serwera zabezpieczonego rdzenia przy użyciu centrum administracyjnego systemu Windows.
- Zaloguj się do portalu Centrum administracyjnego systemu Windows.
- Wybierz serwer, z którym chcesz nawiązać połączenie.
- Wybierz pozycję Zabezpieczenia przy użyciu panelu po lewej stronie, a następnie wybierz kartę Zabezpieczone rdzenie .
- Sprawdź pozycję Funkcje zabezpieczeń ze stanem Nieskonfigurowane, a następnie wybierz pozycję Włącz.
- Po powiadomieniu wybierz pozycję Zaplanuj ponowne uruchomienie systemu, aby utrwalić zmiany.
- Wybierz pozycję Uruchom natychmiast lub Zaplanuj ponowne uruchomienie w odpowiednim czasie dla obciążenia.
Po ponownym uruchomieniu Twój serwer został włączony jako serwer z zabezpieczonym rdzeniem.
Poniżej przedstawiono sposób włączania zabezpieczonego serwera podstawowego dla członków domeny przy użyciu zasad grupy.
Otwórz konsolę zarządzania zasadami grupy , utwórz lub edytuj zasady zastosowane do serwera.
W drzewie konsoli wybierz pozycję Konfiguracja komputera > Szablony administracyjne > System > Device Guard.
Dla ustawienia kliknij prawym przyciskiem myszy Włącz zabezpieczenia oparte na wirtualizacji i wybierz pozycję Edytuj.
Wybierz pozycję Włączone, z menu rozwijanych wybierz następujące opcje:
- Wybierz Bezpieczny Rozruch i Ochrona DMA dla poziomu zabezpieczeń platformy.
- Wybierz opcję Włączone bez blokady lub Włączone z blokadą UEFI dla funkcji wirtualizacji opartej na ochronie integralności kodu.
- Wybierz pozycję Włączone dla konfiguracji bezpiecznego uruchamiania.
Caution
Jeśli używasz włączonej z blokadą UEFI dla ochrony integralności kodu opartej na wirtualizacji, takiej konfiguracji nie można wyłączyć zdalnie. Aby wyłączyć tę funkcję, należy ustawić zasady grupy na wyłączone , a także usunąć funkcje zabezpieczeń z każdego komputera z fizycznym użytkownikiem, aby wyczyścić konfigurację utrwalone w interfejsie UEFI.
Wybierz przycisk OK , aby ukończyć konfigurację.
Uruchom ponownie serwer, aby zastosować zasady grupy.
Po ponownym uruchomieniu Twój serwer został włączony jako serwer z zabezpieczonym rdzeniem.
Weryfikacja konfiguracji serwera z zabezpieczonym rdzeniem
Po skonfigurowaniu serwera z zabezpieczonym rdzeniem, wybierz odpowiednią metodę, aby zweryfikować jego konfigurację.
Poniżej przedstawiono sposób sprawdzenia, czy serwer z zabezpieczonym rdzeniem został skonfigurowany przy użyciu interfejsu użytkownika.
- Na pulpicie systemu Windows otwórz menu Start , wpisz
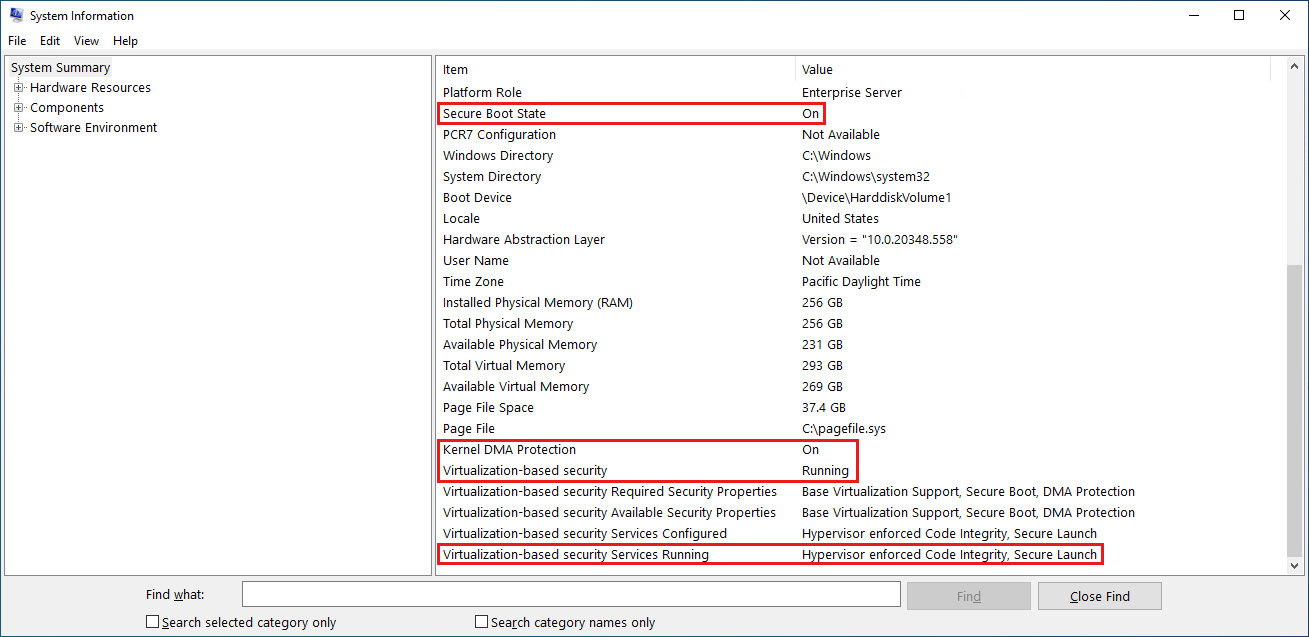
msinfo32.exe polecenie , aby otworzyć pozycję Informacje o systemie. Na stronie Podsumowanie systemu potwierdź:
bezpieczny stan rozruchu i ochrona DMA jądra jest włączona.
Zabezpieczenia oparte na wirtualizacji są uruchomione.
Usługi zabezpieczeń opartych na wirtualizacji Uruchomione usługi pokazują Integralność kodu wymuszaną przez Hypervisora i Bezpieczne Uruchamianie.
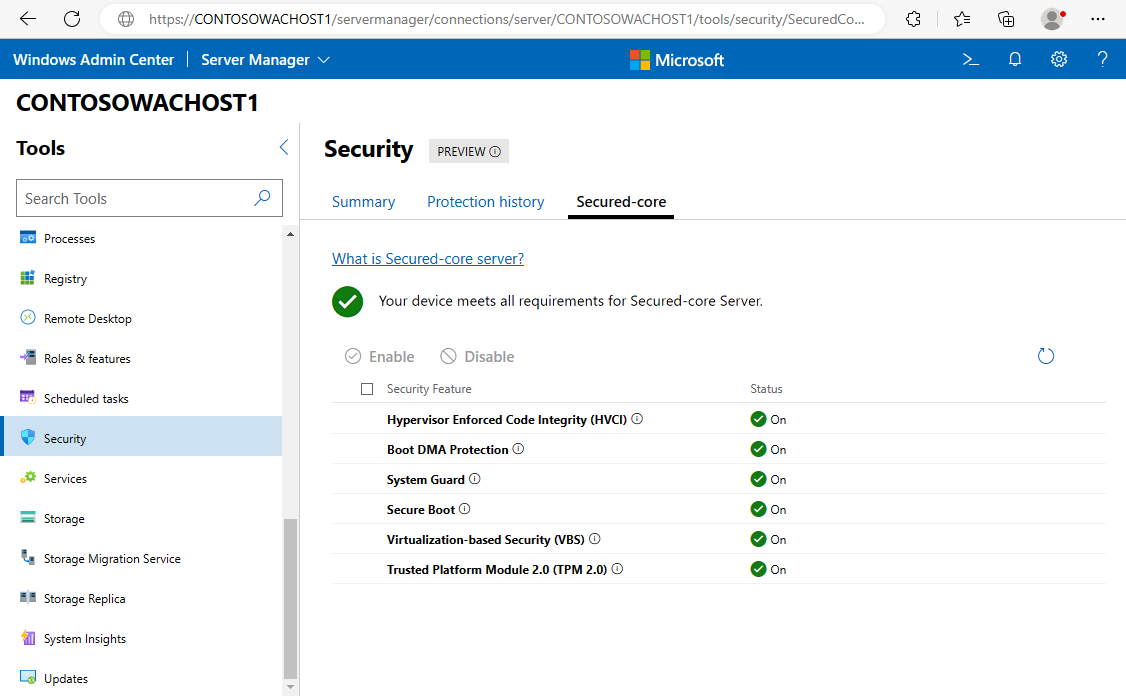
Oto, jak sprawdzić, czy serwer z funkcją Secured-core jest skonfigurowany przy użyciu Windows Admin Center.
Zaloguj się do portalu Centrum administracyjnego systemu Windows.
Wybierz serwer, z którym chcesz nawiązać połączenie.
Wybierz pozycję Zabezpieczenia przy użyciu panelu po lewej stronie, a następnie wybierz kartę Zabezpieczone rdzenie .
Sprawdź, czy wszystkie funkcje zabezpieczeń mają stan Skonfigurowane.
Aby sprawdzić, czy zasady grupy zostały zastosowane do serwera, uruchom następujące polecenie w wierszu polecenia z podwyższonym poziomem uprawnień.
gpresult /SCOPE COMPUTER /R /V
W danych wyjściowych potwierdź, że ustawienia funkcji Device Guard są stosowane w sekcji Szablony administracyjne. Poniższy przykład przedstawia dane wyjściowe po zastosowaniu ustawień.
Administrative Templates
------------------------
GPO: Local Group Policy
Folder Id: SOFTWARE\Policies\Microsoft\Windows\DeviceGuard\LsaCfgFlags
Value: 3, 0, 0, 0
State: Enabled
GPO: Local Group Policy
Folder Id: SOFTWARE\Policies\Microsoft\Windows\DeviceGuard\RequirePlatformSecurityFeatures
Value: 3, 0, 0, 0
State: Enabled
GPO: Local Group Policy
Folder Id: SOFTWARE\Policies\Microsoft\Windows\DeviceGuard\EnableVirtualizationBasedSecurity
Value: 1, 0, 0, 0
State: Enabled
GPO: Local Group Policy
Folder Id: SOFTWARE\Policies\Microsoft\Windows\DeviceGuard\HypervisorEnforcedCodeIntegrity
Value: 2, 0, 0, 0
State: Enabled
GPO: Local Group Policy
Folder Id: SOFTWARE\Policies\Microsoft\Windows\DeviceGuard\HVCIMATRequired
Value: 0, 0, 0, 0
State: Enabled
GPO: Local Group Policy
Folder Id: SOFTWARE\Policies\Microsoft\Windows\DeviceGuard\ConfigureSystemGuardLaunch
Value: 1, 0, 0, 0
State: Enabled
Sprawdź, czy serwer zabezpieczonego rdzenia został skonfigurowany, wykonując kroki opisane w tych krokach.
- Na pulpicie systemu Windows otwórz menu Start , wpisz
msinfo32.exe polecenie , aby otworzyć pozycję Informacje o systemie. Na stronie Podsumowanie systemu potwierdź:
bezpieczny stan rozruchu i ochrona DMA jądra jest włączona.
Zabezpieczenia oparte na wirtualizacji są uruchomione.
Usługi zabezpieczeń opartych na wirtualizacji Uruchomione usługi pokazują Integralność kodu wymuszaną przez Hypervisora i Bezpieczne Uruchamianie.

Dalsze kroki
Teraz, po skonfigurowaniu serwera Zabezpieczone-core, oto kilka zasobów, aby dowiedzieć się więcej na temat:

