SSO for On Premise Integrated Windows Auth Apps using KCD with Azure Web Application Proxy
I was working off of this documentation on MSDN to get this setup in my lab and found it a bit confusing. I am working with the PM’s to get the documentation updated…but in the meantime…
…I thought I’d show how I set this up in my lab – it’s pretty straightforward.
OK, so what are we trying to do?
I have a IIS Server sitting behind my firewall that I want to publish to users that are connecting to the Azure MyApps Portal. Furthermore, I want Azure to handle the pre-authentication to the application and I have my IIS Server configured ONLY for Integrated Windows Authentication. The user is already providing their AD credentials to get access to the MyApps Portal (https://myapps.microsoft.com) so we want to SSO them to the on-prem website that’s sitting behind the firewall.
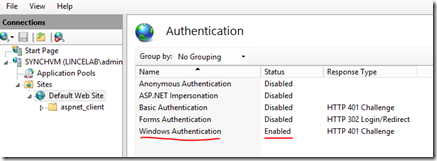
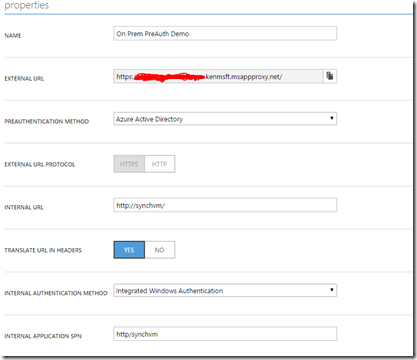
Here’s how we have the IIS Site configured:
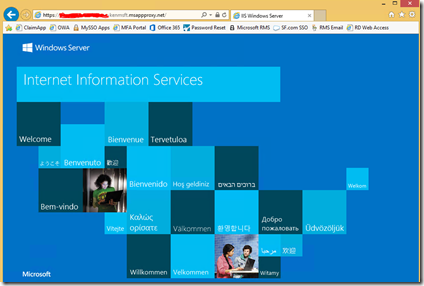
In my case, this is simply the default IIS start page. If I connect to this on premise as a logged in domain user, I get access to the page:
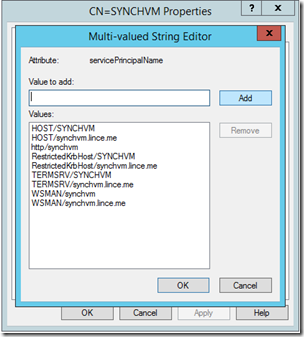
Next, we need to add a SPN on the IIS server. Use ADSI Edit to connect to the IIS Server (in my case the server is named SYNCHVM) and add a http/hostname SPN. In my case it was “http/syncvm”. We’ll use this SPN in the Azure Admin Portal to configure access to the site in a bit…
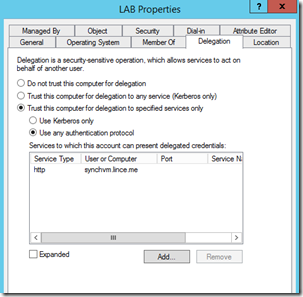
Now on the server that is running the Azure WAP connector/agent you need to configure constrained delegation. To do this, open AD Users and Computers and find the computer running the Azure WAP Connector/agent. Right click –> Properties and select the ‘delegation’ tab. You’ll need to configure yours similar to mine adding the IIS server and the http service type.
On the Azure side you’ll walk through the wizard process to add an application via the Azure WAP. When you click into the application once it’s configured and get advanced properties you will want to set yours up accordingly. The last 2 fields are not exposed during the wizard setup – you’ll have to get into the ‘configure’ tab of the application to turn on integrated auth and add the SPN you configured in a previous step.
So the final step here is doing some testing…
I open a web browser on a non-domain joined computer or internet connected device. I enter the URL that Azure assigned me for the application I published. In my case, I’m using ADFS so I get redirected to my ADFS server on-prem for authentication. Once I’m authenticated as a domain user, I get signed on to my application behind the firewall. If you weren’t setup to use ADFS your user would be authenticated out of Azure Active Directory. Now of course, this assumes that you are using DirSync and those on-prem users have been synchronized out to Azure AD.