Advanced Threat Analytics(ATA) Deployment and Capabilities Part-II
Once again bringing an interesting part of Advanced Threat Analytics(ATA). In the previous blog we looked into complete setup process. If you have not already got a chance, please take a look at part-1 here Part-1 talks about how to configure and install ATA
In this blog, we will look into few capabilities of ATA. That means, we will try to generate or perform few suspicious activities and see how effective ATA would be to trap that and report. Lab machines setup continues as mentioned on part-1. So lets get started.
Note:- Please get the environment setup from previous blog. https://blogs.technet.microsoft.com/chandanbharti/2017/04/27/advanced-threat-analyticsata-deployment-steps-part-i/
Entire concept of this post is to simulate some suspicious action in an environment.
Activity 1:- DNS Zone Transfer
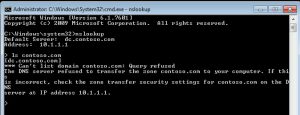
- Login to the client machine with user account and open a cmd prompt window and type nslookup -->ENTER
- Hit exit on cmd prompt to close the window.
- Log in to ATACenter VM and browse to https://10.1.1.6
- check notification
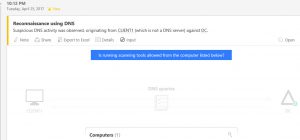
- You should see the activity of DNS activities has been logged.It should be logged with "Reconnaissance Using DNS" suspicious activity. Navigate around to check the severity and more information about this.
- You should be able to get the details view to get more details.
Activity 2:-
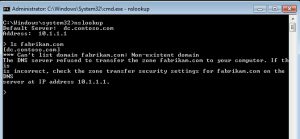
- Login to client machine and on cmd prompt, type nslookup -->ENTER
- Type "ls hallo.com" -->ENTER
- Type fabricam.com -->ENTER
- Move over to ATACenter VM and browse to console https://10.1.1.6
- Notice the suspicious activity recorded,
- Check the details of each activity that you see and also time stamp on it.
Activity 3:-
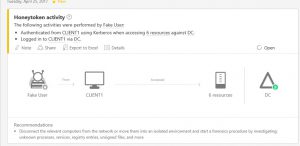
- Login to client machine again with HoneyToken user
Note: HoneyToken user is the account that is inactive and not used, I have created an account with name Fake User (CONTOSO\ADMINUSER). Whole idea is to check what if suddenly an inactive account gets active one fine day and tries to log in to resources.
- Please use password something like WWAATT which is not correct, and i want to make an unsuccessful attempt.
- Now lets go to ATA center and log into console https://10.1.1.6. You should see something like this
- Go to details and severity. Most common resolution is suggested and also you should see some action that you can perform.
Activity 4:- Deletion of user accounts in AD.
- Login to DC with domain admin and run dsa.msc to open users and computers console.
- Navigate to User account OU and select all the user and delete them.
- Once done, close the user and computer console.
- Go to ATAcenter console https://10.1.1.6 and check the notification. It should show something like "Massive object deletion Alert"
Activity 5:-
- Log into the client machine. (Please download sysinternal tools and save it in a folder in client machine.)
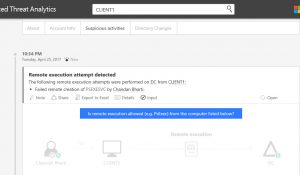
- At command prompt, type "psexec \\dc notepad.exe" (note: note that an account is trying to make a remote connection and execute a command)
- Exit out of command prompt and log into ATACenter console.
- Go through the details of the activities to understand it better.
Activity 6:- Directory service enumeration.
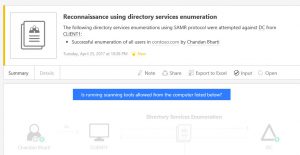
- Log in to client CM and open a command prompt
- Type these 2 commands. "net user /domain" and "Net group /domain"
- connect to ATA center console and check on activities you may have received named "Reconnaissance using directory services enumeration"
- Go through the details to get better understanding.
Note:- We are trying to simulate few scenarios that is usually performed during a cyber attacks. These rules can be modified and created at will.
Eventually all the notification you received can be visible this way in the console.
These are some of the magic activities that you can perform to showcase the capabilities of ATA.
In the next blog, i will bring few administrative actions that you can do in the product so stay tuned and happy learning!!
-Chandan