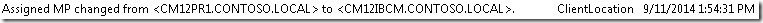Management Point Affinity Added in ConfigMgr 2012 R2 CU3
Overview:
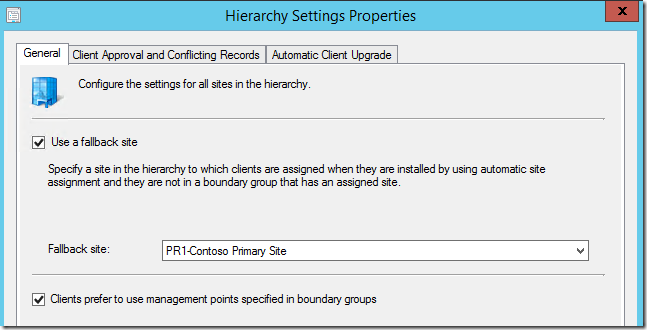
Update: In Configuration Manager 2012 SP2/SP1 R2 this feature can now be implemented using boundary groups and doesn’t require this registry method. You can enable this feature in the Hierarchy Settings on the site:
A common request the product group has received is to provide a way to define management point affinity for a specific set of ConfigMgr Clients in a primary site.
Starting with ConfigMgr 2012 R2 cumulative update 3 (https://support.microsoft.com/kb/2994331) there is a new way to define management point affinity for clients.
Caveats of Management Point Affinity in CU3:
There are some caveats in the way management point affinity works in cumulative update 3. You can set a client to use a specific management point(s) by setting a registry value. When this registry value exist, It will cause LocationServices to bypass switching to any management point(s) during a Location Services Rotation unless it’s defined in the registry value.
The downside to this approach is if the management point(s) the client is forced to use goes down you will have an unmanaged client until the management point(s) is back online or the registry value is deleted or changed.
This method should only be used for management point(s) in a primary site. Clients in a boundary group of a secondary site will still use the secondary sites management point as a proxy management point. This can be used to set the initial management point communication for clients to register with a management point at a primary site before it starts to use a secondary site’s management point as a proxy management point.
This method is only for management point selection. This does not apply to distribution points, software update points, Fallback Status Points, or any other site system roles.
This method only works for intranet clients and intranet management points.
This method can’t be used to defeat the HTTPS preference over HTTP management point(s).
Only management point(s) in the same primary site as the client can be used.
Potential Scenarios:
- Computers in restricted network such as a DMZ where the client can only communicate with specific set management point(s) in the primary site.
How to Set the Management Point Affinity:
Below are snippets from my lab that I used to test out this new feature.
Site Servers / Systems:
CM12PR1 - (Site Server also Hosting a Management Point Intranet)
CM12IBCM - (Site System Hosting a Management Point Intranet)
Clients:
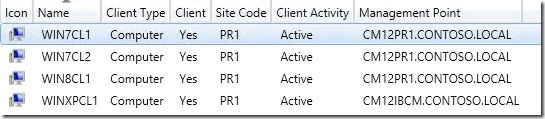
WIN7CL1 – (Client currently using CM12PR1 as MP)
WIN7CL2 – (Client currently using CM12PR1 as MP)
WIN8CL1 – (Client currently using CM12PR1 as MP)
WINCPCL1 – (Client currently using CM12IBCM as MP)
How to Set Management Point Affinity:
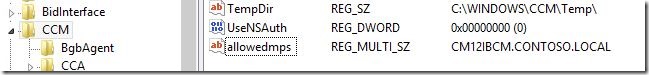
Management point affinity is set by defining the following registry value.
Key: HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\CCM:AllowedMPs
Type: Reg_Multi_SZ
Value Data: CM12IBCM.CONTOSO.LOCAL
Value Data: Is the FQDN of the Management Point(s) you want to allow the client to communicate with. You can set multiple management points in the REG_MULTI_SZ value one per line.
I manually set these values on four machines in my lab, but you could use Group Policy, Compliance Scripts, etc.
I set each of my four clients to use the opposite management point as they were currently communicating with as mentioned above.
After these values where set, I installed the cumulative update 3 on my 4 clients machines. The order shouldn’t matter here though you could set the registry values before or after installing the cumulative update 3 client update.
On WIN7CL1, I could see the following information in the logs after cumulative update 3 was installed:
ClientLocation.log
LocationServices.log
We can see that Location Services can detect the new registry value and will filter out any management points that are not in the list.
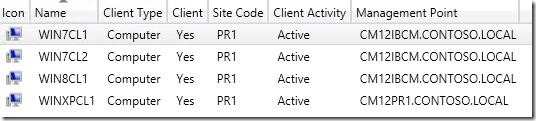
Here’s a screenshot of my 4 clients after cumulative update 3 was installed. We can see each client switched management points.
Wrapping Up:
This is not intended as a MP enforcement for “Mobile” devices such as Laptops and Tablets. This is intended for scenarios where it is really required like DMZ networks where communication may not be open to all management points in the site.
Disclaimer: The information on this site is provided "AS IS" with no warranties, confers no rights, and is not supported by the authors or Microsoft Corporation. Use of any included script samples are subject to the terms specified in the Terms of Use
Comments
- Anonymous
January 01, 2003
The comment has been removed - Anonymous
January 01, 2003
MP affinity only applies if you set the registry keys no issue deploying. - Anonymous
January 01, 2003
Thanks for implementing this. - Anonymous
January 01, 2003
Yes, i would like to know how does the client handles multiple MP's when listed? And how is this setting modfied, Can we do this in the console, or is this a GPO that applies the setting? - Anonymous
January 01, 2003
@ Christian, I'm not aware of any issues with HTTPS MP's. This can't be used for Internet Facing clients though. - Anonymous
January 01, 2003
You could try creating site based media, but this solution is not designed for WinPE. - Anonymous
January 01, 2003
@Ithomas this only applies to windows. - Anonymous
September 22, 2014
Thanks - Anonymous
September 23, 2014
The comment has been removed - Anonymous
September 23, 2014
If we set multiple entries in the registry key how does the client process the list/will it attempt to use the first MP/use the second if the first isn't available? - Anonymous
September 24, 2014
Yes, i would like to know how does the client handles multiple MP's when listed? And how is this setting modfied, Can we do this in the console, or is this a GPO that applies the setting? - Anonymous
September 26, 2014
Finally we will be able to fully use Config Manager in our environment. This update/fix wasn't a day too soon. Thanks for testing and confirming it! - Anonymous
October 06, 2014
The latest cumulative update for SCCM 2012 R2 has been released by Microsofthttp://support.microsoft - Anonymous
October 08, 2014
Mon collègue américain Justin Chalfant a publié sur son blog un article expliquant l’utilisation d’une - Anonymous
October 20, 2014
The comment has been removed - Anonymous
November 21, 2014
Hi Justin,
is there any known issue when the MP in allowed MPs is https only? Or does it have to behttps://Mp.domain.com in the allowedmps-Setting then?
Thanks
Christian - Anonymous
November 24, 2014
@Justin ok. thanks. - Anonymous
January 13, 2015
What about a scenario where the company uses two management points for failover purposes, e.g., one MP connects to site DB, and the other MP connects to a replica of the site DB? If I'm reading this post correctly, we would need to deploy the registry values for BOTH MP's to each client, so if a MP fails, the client fails over to the other MP. Is this a correct assumption? If we don't wish to add the extra complexity and trouble associated with implementing MP affinity--and keep our location services rotation the way it currently is, which works great--is there a way to deploy the rest of CU3 without deploying MP affinity? - Anonymous
February 16, 2015
The comment has been removed - Anonymous
April 14, 2015
Yes, we also wonder about Task Sequence and unknown computers. How can we force MP communication in WINPE ? - Anonymous
May 19, 2015
What about Linux/Unix and other clients? - Anonymous
October 09, 2015
FYI
If you have a stand-alone primary site in ConfigMgr 2012 R2 SP1, the setting "Clients prefer to use management points specified in boundary groups" is ignored (tested in my environment). You have to apply CU1 for ConfigMgr 2012 R2 SP1, seehttps://support.microsoft.com/en-us/kb/3074857 - Anonymous
September 21, 2016
Does this still apply in current branch (1606)? I have the registry key entered manually and the management is still not forced. - Anonymous
November 20, 2017
The comment has been removed