SQL Injection
While discussing with a newbie web developer friend today, topic of SQL Injection came up and I was trying to give him an example & explain seriousness of SQL Injection. So, thought of sharing the same example for folks trying to look for simple SQL injection examples. This is recycled bit from my old post on a different blogging site few years back.
Let’s get started:-
Connect to SQL server instance and create a simple table in any of your test or playground database as.
CREATE TABLE UserDetails
(
Id INT IDENTITY(1,1),
UserName VARCHAR(6),
Pwd VARCHAR(32),
SSNNumber SMALLINT,
Addres NVARCHAR(100),
ZipCode smallint
)
Let’s insert some data into this table.
INSERT INTO UserDetails
VALUES
('Shubh'
,'5f4dcc3b5aa765d61d8327deb882cf98'
,123
,'House Number1, Street Number1, Apt Number1, ZipCode1, State1'
,12345),
('Khushi'
,'6f4dcc3b5aa765d61d8327deb882cf97'
,456
,'House Number2, Street Number2, Apt Number2, ZipCode2, State2'
,17891),
('Ashi'
,'7f4dcc3b5aa765d61d8327deb882cf96'
,789
,'House Number3, Street Number3, Apt Number3, ZipCode3, State3'
,23456)
Now, assume this table is used to store information about registered users of a website.
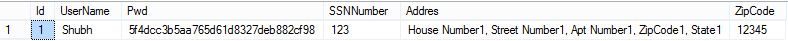
Next a business users comes in to website and searches for customer name using username as Shubh and in the background below SQL query is run to get the results for that specific username. (Assume that business user is authorized from website security perspective to search a username).
SELECT * FROM UserDetails WHERE UserName = 'Shubh';
Output displays below data, which is expected, all is well:
Now, if a user enter input as 'OR 1=1--
This makes the query look like this, which means SQL injected by manipulating way you enter value in search box:
SELECT * FROM UserDetails WHERE UserName = ''OR 1=1--';
And the result is a disaster (S1/P1 bug), as it shows all users and their information.
Try out the above example and hope this helps! Important thing is to always test for SQL injection from a tester perspective, and push for input validations in code.
Comments
- Anonymous
October 23, 2013
Great and Crisp example. I have been reading your blogs and admire them. Keep up the good work.