Windows 8: Trusted Boot: Secure Boot – Measured Boot
My Top-3 Trusted Boot: Secure Boot – Measured Boot
One of the benefits of a UEFI configuration is that it supports signing and verification for UEFI executable files, up to and including the boot manager, which implements the boot menu in Windows 8.
Secure Boot
This, combined with further verification checking done by Windows, is what constitutes Secure Boot. This feature helps protect Windows against malware or other tampering.
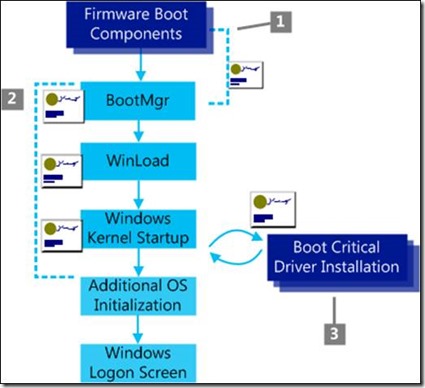
Figure 1: Secure Boot
The three main actions related to Secure Boot are shown in the diagram above. These are:
- The firmware verifies all UEFI executable files and the OS loader to be sure they are trusted.
- Windows Boot Components verify the signature on each component to be loaded. Any non-trusted components will not be loaded and will trigger remediation.
- The signatures on all Boot Critical Drivers are checked as part of Secure Boot verification in WinLoad and by the Early Launch Anti-Malware driver
Secure Boot Remediation
In the event that the UEFI firmware that Boot Manager does not match its signing information, it replaces Boot Manager with a backup copy. In the event that this also fails, the UEFI firmware will display some kind of remediation information, giving you a way to return to a trusted state. This remediation experience is implemented by each OEM, so the specifics differ.
Early Launch Anti-Malware
Secure Boot enables a related feature: Early-Launch Anti-Malware (ELAM). This provides the ability for an anti-malware driver to register as a trusted Boot Critical Driver. This makes it the first non-Microsoft, non-platform specific code that will run on the computer. The anti-malware driver can then verify other drivers in turn before they are initialized.
Secure Boot helps prevent malware from running before the OS, Early Launch AV helps ensure that trusted anti-malware software is the first third-party component run on each startup.
Figure 2: Secure Boot with ELAM
ELAM adds a fourth step to the Secure Boot process, labeled “4” in the diagram above.
- Early Launch Anti-Malware driver is checked for a special signature issued by Microsoft verifying that it is trusted and will early launch, meaning it is always started before all other drivers.
Measured Boot
Measured Boot is another boot feature in Windows 8 that is also related to anti-malware software. Measured boot gives the anti-malware software a detailed, reliable log of components that loaded prior to the anti-malware driver during startup. This log can be used by anti-malware software or an administrator in a business environment to validate whether there may be malware on the computer, or evidence of tampering with boot components.
Trusted Boot
Windows 8 systems ship with a certificate in the UEFI that analyzes the boot loader to ensure it is both the right one and is signed by Microsoft. If you were to encounter a rootkit , the UEFI wouldn't allow it to boot. In other words, UEFI protects the pre-OS environment. Additionally, as the system boots, Windows 8 detects if any of the OS elements have been tampered with and automatically restores the unmodified versions. As you know from that earlier post, Secure Boot is just one of the three pillars of what is called the Trusted Boot process.
There are a lot more specific details here, if anyone wants to go deeper:
https://msdn.microsoft.com/en-us/library/windows/hardware/br259097.aspx
ONiehus, Microsoft
Comments
Anonymous
February 01, 2013
Merci ! Impossible de redémarrer Windows 8 à cause de ce type de procédure ! J'ai lancé Acronis (logiciel de sauvegarde payant) et il le prend pour un Malware ... C'est une belle escroquerie ! Je suis obligé de tout réinstaller. A moins d'une autre solution ...Anonymous
December 01, 2014
This blog is very confusing with the definition of secure boot, trusted boot, etc. the "Securing the Windows 8 Boot Process" article at MSDN technet describes clearly the boundary/range of secure boot, trusted boot. This blog should be deleted to avoid the confusion, or if it is correct by Microsoft. the article in MSDN technet should be removed. thanks