Decrypting SSTP traffic with Netmon and NMDecrypt
Intro
I have recently received some inquiries about [MS-SSTP].
I must admit that I had to review most of the information about this “fairly” newly introduced VPN protocol (it was first shipped with Windows Vista) since I hadn’t been working with it for a while.
For those that are just learning about the existence of this protocol, a brief description of SSTP would be:
“SSTP (Secure Socket Tunneling Protocol) allows encapsulating PPP (Point to Point Protocol) packets into a secure HTTPS connection.”
There are many articles that help understanding how to set up this environment so I won’t be jumping into details about this task. Instead I’ll be just pointing to the most relevant resources:
- SSTP Remote Access Step-by-Step Guide: Deployment: https://technet.microsoft.com/en-us/library/cc731352(WS.10).aspx
- How an IIS Web server and a Secure Socket Tunneling Protocol (SSTP)-based Routing and Remote Access server can co-exist on a Windows Server 2008-based server: https://support.microsoft.com/kb/947026/en-us
- How to troubleshoot Secure Socket Tunneling Protocol (SSTP)-based connection failures in Windows Server 2008: https://support.microsoft.com/kb/947031
What’s needed?
In order to be able to decrypt SSTP traffic with Network Monitor, the following are needed:
Network Monitor: Its latest version can be downloaded from https://support.microsoft.com/?kbid=933741. That article points to the download site (for both x86 and x64) and to related information.
NMDecrypt (Network Monitor Decryption Expert): This expert can be downloaded from https://nmdecrypt.codeplex.com/. Once downloaded, it needs to be installed. Note that there are x86 and x64 versions as well.
The server certificate / private key in one of the following formats:
- Binary PKCS12 (PFX) IIS certificate (and the password used when exported)
The steps to do this from the Windows MMC can be found on NMDecrypt’s help - PEM (text-based) private certificate
- .key file (contains the private key of the server in text format)
A network capture file (.cap) containing the SSTP traffic : It must include the initial SSL challenge response. In some cases, if the capture was taken with a later version of Netmon than the one where NMDecrypt is installed, the analysis may fail, so it is sometimes a time saver for the capture to be taken with the same version of Netmon that is being used with NMDecrypt.
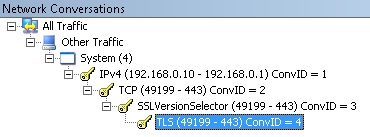
Also, if at all possible, the capture should contain just the TCP conversation related to the SSTP traffic. If the capture contains multiple conversations, it is a time saver to select the appropriate TCP conversation once opened in Netmon and then running the expert.
This is an example of what you should see:
How to make magic happen?
Once Netmon is open, NMDecrypt is run by following these steps:
Click on the Experts menu:
Select the correct expert (NMDecrypt) and then select “Run Expert”:
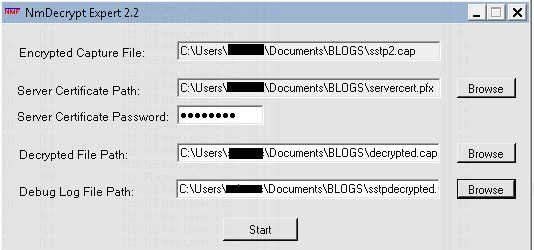
Complete the requested information:
The path to the encrypted capture
The path to the server certificate
The password for the .pfx file (if this is the format for the certificate)
The path to the resultant decrypted file
The path to the log file
Once the fields are completed, press Start.
Magic will happen during a couple minutes (execution time depends on the size of the capture) and a new instance of Netmon will pop up with the decrypted capture. Things could go wrong while decrypting in which case the descriptive errors will be logged in the resultant log file.
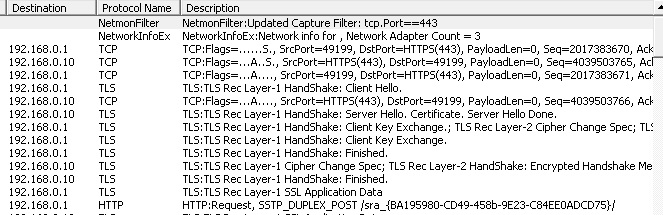
For comparison purposes, here are screenshots of how some frames look like before and after decryption:
Before:
After:
As you may already have noticed, the SSL Application Data is mostly broken down. However, most SSTP messages may not be available at first sight.
If the SSTP packets of interest are not viewable at first sight, some HTTP payload needs to be decoded as SSTP. In order to do that:
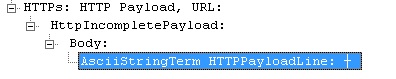
Select an HTTP frame:
On the Frame Details section select the HTTPPayloadLine property:
On the Hex Details section, the raw data corresponding to that property will be highlighted:
Click on the Decode As button (right above the raw data):
The Decode As window will pop up, select SSTP under the Protocols branch:
Click OK and a new Decoded Frame window with the decoded frame will pop up:
I hope that you find this information useful.
If you want to expand on NMDecrypt and Netmon, you can take a look at this blog.
Until next time!