PowerShell: Malware detection and tracking of new autoruns
Old Project realized
A month ago I reinstalled one of my PC's and thought of a project I started but never finished many years ago. It was when I found out about autorunsc.exe , one of the many awesome tools from the Sysinternals suite and the creator Mark Russinovich, when I thought of an idea to keep track of all additions to my Windows installation. Any additions to it that had any effect on my boot process or that started any processes at startup. With this information I would be able to determine when I had additions I didn’t approved nor expected. Then I could simple remove these binaries or uninstall the guilty application.
Now, I have a slightly different approach. Besides catching all additions to the auto-runs in my Windows installation I also would like to know what executables are signed or not and if these could be a threat to me. I'm thinking of malware and vicious code. I think autorunsc.exe can do a fantastic job here with all its features, especially with some of the new features and the combination with another awesome tool, also from Sysinternals, Sigcheck.
Some of the things Autorunsc do:
List all drivers, processes, scheduled tasks, boot drivers , logon startups and auto-runs.
Check if the image of the executable is signed or not.
Check the hash of the image.
Link to Autoruns : https://technet.microsoft.com/en-us/sysinternals/bb963902
Some of the things SigCheck do:
Verify signatures.
Check the image against Virus Total, a free online virus, malware and URL Scanner.
Link to SigCheck: https://technet.microsoft.com/en-us/sysinternals/bb897441
With a combination of both:
Scan my entire system auto-runs against Virus Total, i.e. the things Autorunsc.exe collects:
Boot execute.
Codecs.
Appinit DLLs.
Explorer addons.
Sidebar gadgets (Vista and higher)
Image hijacks.
Internet Explorer addons.
Known DLLs.
Logon startups (this is the default).
WMI entries.
Winsock protocol and network providers.
Office addins.
Printer monitor DLLs.
LSA security providers.
Autostart services and non-disabled drivers.
Scheduled tasks.
Winlogon entries.
Powershell - There's nothing PowerShell can't do!
Powershell comes to help once again. By using PowerShell I built a wrapper around these two Sysinternals tools (Autrunsc.exe and SigCheck.exe) plus some GUI to provide you with notifications when you got new binaries on your system.
The processs:
- Use Scheduled Tasks to run the script at:
- Boot(Analyze autoruns) .
- User Logon (Notifications).
One Powershell script that does all the job.
The script scan the machine with Autorunsc.exe.
Generates CSV output.
Compares CSV inbetween boots.
The script finds any differences.
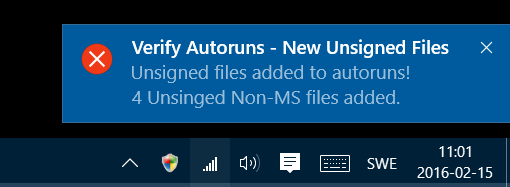
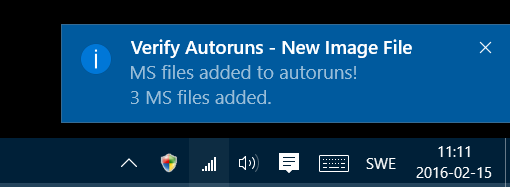
The script sends the user notifications when:
New Unsigned Non-Microsoft Binaries added.
New Unsigned Microsoft Binaries added.
Files with New Hash and Unsigned Binaries added.
New Non-Microsoft Binaries added.
New Microsoft Binaries added.
Provide a UI to see the added files and a summary.
With the list of additions you can run a check against Virus Total.
The value this script provides
Scan the entire system auto-runs with Virus Total.
Creates an offline file for scanning entire system auto-runs with Virus Total, when no internet is available.
Notifications when additions to the system are added.
A Summary of additions over every boot.
Summary of current additions with information about what kind of modifications done.
Requirements
These are the requirements.
PowerShell
Sysinternals Autorunsc v13.51 (or newer) - Autostart program viewer.
Sysinternals Sigcheck v2.50 (or newer) - File version and signature viewer.
Internet connection if you will run a check against Virus Total.
Important! Once run Sigcheck -v <any file> and accept the agreement with Virus Total, if you do agree of cause :).
Important! Agree to Autorunsc.exe EULA.
Important! Agree to SigCheck.exe EULA.
Run the PowerShell script once and it will prompt you with the option to agree to the EULA and to use Virus Total.
Tip! : I would recommend the nice script Update-sysinternals.ps1 to keep your Sysinternals tools updated.
Modify the following command in the script to something like this.
Update-Sysinternalshttp -ToolsLocalDir "c:\Sysinternals"
https://gallery.technet.microsoft.com/scriptcenter/Another-Sysinternals-Tools-aa288439
Config
To run this you have to put these two files, Autorunsc.exe and SigCheck.exe, in a folder on your drive, the expected path is C:\Sysinternals but it's configurable.
1. First run must include the "-Analyze" switch . This is needed after each boot since it will collect all auto-runs.
Verify-Autoruns.ps1 -Analyze
Or
Verify-Autoruns.ps1 -Analyze -Dir <folder path to Autorunsc.exe and SigCheck.exe>
2. Once we have collected data we can run the script without scanning if we just want to get notifications and summary
Verify-Autoruns.ps1
Or if we want notifications even if nothing has happend:
Verify-Autoruns.ps1 -Icon
I also suggest you put the script in the same directory, but it is not a requirement ,though it must be configured in the scheduled task.
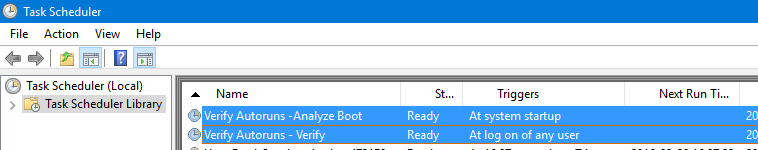
You can schedule a task in that runs at every boot.
This is the action for the task:
Program: C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe
Arguments: -ExecutionPolicy Unrestricted -File "C:\Sysinternals\Verify-Autoruns.ps1" "-Analyze"
If you want you can just import the exported Scheduled Task provided : Verify Autoruns - Analyze Boot.xml included in the attached file VerifyAutoruns_ScheduledTaskExports.zip
You can also schedule a task in that runs at every logon to provide the user that logons with notifications.
Program: C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe
Arguments: -Nologo -WindowStyle Hidden -ExecutionPolicy Unrestricted -File "C:\Sysinternals\Verify-Autoruns.ps1" "-Icon"
If you want you can just import the exported Scheduled Task provided : Verify Autoruns - Verify.xml included in the attached file VerifyAutoruns_ScheduledTaskExports.zip
Output from Verify-Autoruns
What will this powershell script generate:
- A CSV file with all the autoruns on the system in a folder called C:\AutorunsLogs (Can be customized). Example: AutorunsC_20160210-0925.csv
Verify-Autoruns.ps1 -LogDir <folder path to all logs>
A CSV file with any new files added . This will require that you have at least two boot scans created, there's only going to be one file for each boot. Example file: AutorunsC_New_20160210-0950.csv
A CSV file with the collected summary of all added files, i.e. the contents of all AutorunsC_New.. files.
SigCheck input CSV file for offline systems that can not access to internet. This file can be moved and run on internet connected systems for checking with Virus Total.
Notifications Icon.
Ballon Notifications.
Report Window.
Summary Window.
Notifications Icon
This Shield icon in the task bar let you access three things:
The Report Window.
The Summary of the last run.
Windows Reliability Monitor (This tool can provide you with events on your system that might have caused one of the additions to the auto-runs)
Balloon Notifications
The following notifications are fired at detection. This will require that you have at least two boot scans created, there's only going to be one file for each boot.
- New Non-Microsoft Files that are not signed
- Files with new Hash that are not signed
- New Microsoft files that are not signed
- New Non-Microsoft files added
- New Microsoft files added
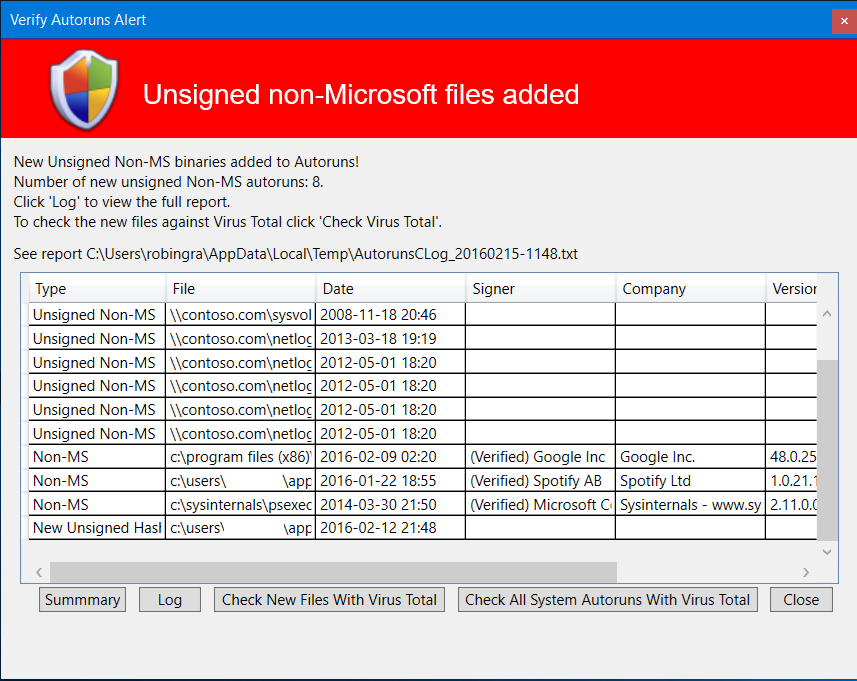
Report Window
Here can you view the files added to autoruns. You can also:
View a summary of the last boot.
View the logfile.
Check the new files against Virus Total. Requires Internet. (Requires SigCheck.exe ver 2.50 in the same folder as Autorunsc.exe).
Check all current autoruns against Virus Total .Requires Internet. (This might take a while).
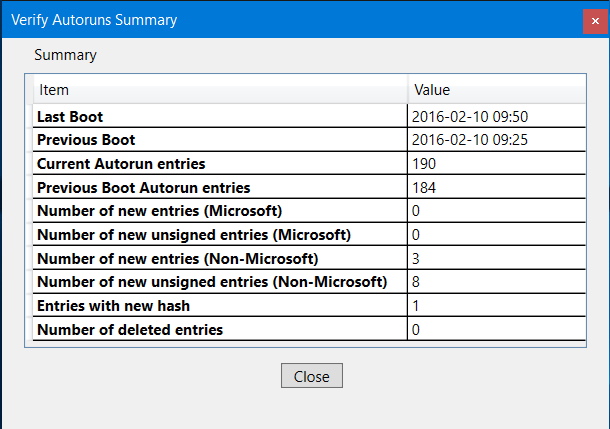
Summary Window
This list shows the results from the latest analysis.
Virus Total Check Window
This is a table with the results from Virus Total. The column VT Detection will let you know the detection ratio. How many indications of the binary to be "unsecure" in ratio with the number of sources of information.
This picture shows the Virus Total outcome of the new addtions to Windows from the latest boot.
Scan the entire systems auto-runs against Virus Total
If you like to scan all binaries that the system runs at boot and startup you can do it from the Report Window, just click "Check All System Autoruns with Virus Total", or you can do it directly from the Powerhshell command line.
Command:
PS C:\Sysinternals> .\Verify-Autoruns.ps1 -SystemCheck
This action might take a while since there are many files to be checked over internet.
Or if no internet connection is possible:
PS C:\Sysinternals> .\Verify-Autoruns.ps1 -SystemCheck -Offline
The output from this command can be used with SigChekc on a internet connected system like this:
SigCheck.exe -o -v VTInput.csv > VTResult.csv
This output will file contain the VT Detection ratio for each file. It's a CSV file that's best suitable for opening in Excel or similar.
Summary
With this script running on my PC's I can easily determine all the auto-runs added, even over time. But the coolest feature according to me is that you can scan the entire systems auto-runs against Virus Total online or offline.
This script does of course not replace any antivirus or malware software. I use it on all my PC's as an additional control and nice to have.
The script is available at TechNet Script Center here.
VerifyAutoruns_ScheduledTaskExports.zip
Comments
- Anonymous
February 21, 2016
Really nice article, thank you very much - Anonymous
February 22, 2016
When running this I get the following:
Could not import last autoruns file: C:AutorunsLogsAutorunsC_20160215-0805.csv. Try re-run with -Analyze parameter to create a new file.
so I run: .Verify-Autoruns.ps1 -Analyze
I get the same issue. It's not creating the CSV file. I tried as Administrator and running under normal conditions. Thanks for the great post! - Anonymous
February 22, 2016
https://www.reddit.com/r/sysadmin/comments/46zl30/powershell_malware_detection_and_tracking_of_new/
You may want to clean up some of the errors - Anonymous
February 22, 2016
@OsageNDN
Have you put Autorunsc.exe and Sigcheck.exe in C:Sysinternals folder? If you store these two in another folder you have to use “-Dir” to point to the point to that folder. - Anonymous
February 22, 2016
@HeyITsMe!
Yep, there are some spelling errors. I will fix that. - Anonymous
February 22, 2016
Muy buena información, gracias por compartir. - Anonymous
February 22, 2016
Almost there. Getting two errors when running .verify-autoruns.ps1 -systemcheck
Cannot index into a null array.
At C:sysinternalsVerify-Autoruns.ps1:2763 char:29
+ ... $file[0] = $file[0].Replace("$([char]34)","")
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : InvalidOperation: (:) [], RuntimeException
+ FullyQualifiedErrorId : NullArray
You cannot call a method on a null-valued expression.
At C:sysinternalsVerify-Autoruns.ps1:2853 char:29
+ $VerifyVTGui.Window.Activate()
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : InvalidOperation: (:) [], RuntimeException
+ FullyQualifiedErrorId : InvokeMethodOnNull
Any guesses? - Anonymous
February 22, 2016
The comment has been removed - Anonymous
February 22, 2016
Windows 10 and PS version 5.0.10586.63 - Anonymous
February 22, 2016
@NickS
Do you got a C:AutorunsLogsAutorunsC_[your boot time].csv and does it got any content?
What regional settings are you using? - Anonymous
February 22, 2016
I did get a .csv in that directory when I ran the .ps1 using the -analyze parameter. It was filled with all log information regarding my autorun and signed certs.
I got returning information from the VTInput.csv when I ran the -systemcheck -offline parameters. - Anonymous
February 22, 2016
The comment has been removed - Anonymous
February 22, 2016
The comment has been removed - Anonymous
February 23, 2016
Malware detection using Powershell and SysInternals