SignTool Error: The signer's certificate is not valid for signing
You may find the below error message while publishing a ClickOnce application in the Visual Studio IDE: “SignTool Error: The signer's certificate is not valid for signing”
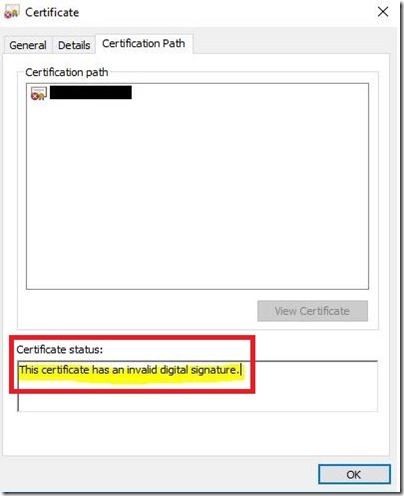
Since, the above error message indicates that it's an issue with the certificate. I tried signing a sample EXE file using the same certificate and it failed with the below error message:
C:\>signtool.exe sign /f My_Certificate.pfx MyApp.exe
SignTool Error: The signer's certificate is not valid for signing.
SignTool Error: An error occurred while attempting to sign: MyApp.exe
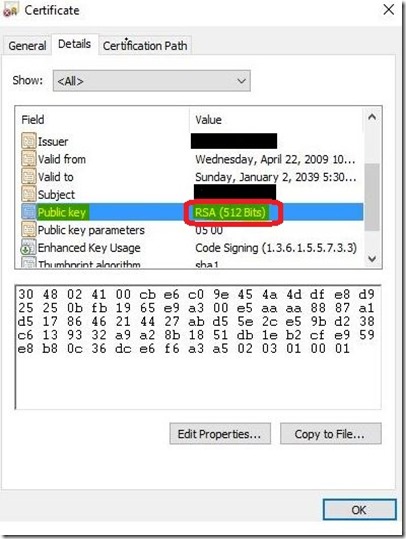
Then I verified the certificate property and found the below information:
The above issue is due to the certificate having an RSA key less than 1024 bits (512 bits) long. As per this MSDN doc: https://msdn.microsoft.com/en-us/library/aa374191(v=vs.85).aspx
publicKeyToken- A 16-character hexadecimal string representing the last 8 bytes of the SHA-1 hash of the public key under which the application or assembly is signed. The public key used to sign the catalog must be 2048 bits or greater.
Hence, the recommended resolution would be to implement certificates that have a key length of at least 2048 bits. Then sign the ClickOnce application using the certificate.
An alternative workaround:
The following command (admin prompt) would allow you to bypass the blocking keys that have a length of less than1024 bits: certutil -setreg chain\minRSAPubKeyBitLength 512
You can revert to blocking keys that have a length of less than1024 bits by removing the value. To do this, run the following certutil command: certutil -delreg chain\MinRsaPubKeyBitLength
Microsoft does not recommend customers use certificates less than 1024 bits long. Customers may however need the above temporary workaround while a longer term solution is developed to replace RSA certificates with a key length of less than 1024 bits length. Customers configuring these settings are accepting the risk that an attacker may be able to break their certificates and use them to spoof content, perform phishing attacks, or perform Man-in-the-Middle attacks.