Office 365 Certificates and the Hybrid Configuration Wizard
It’s been a while since my last blog, but the world of Microsoft Consulting has been keeping me very busy.
In this post I’m going to cover an issue I picked up during an Office 365 Hybrid deployment for a customer.
I’m not going to go into much detail around the actual deployment as there’s great documentation available on the deployment process, but I couldn’t find any reference to the issue I picked up with the certificates on Hybrid Configuration Wizard.
When you start planning your Office 365 hybrid solution you'll need to plan for a trusted third party certificate. It's required for ADFS and Transport Layer Security to work between the on-premise environment and Office 365.
During my deployment my customer requested the certificate and everything was looking good until I wanted to configure mail flow. The Hybrid Configuration Wizard wasn’t picking up the certificates on the transport servers.
After a little (actually...ALOT) of digging I found that my customer was pushing certificates via GPO, even the third party trusted Root CA certificates.
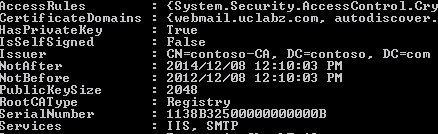
Upon checking the certificate in EMS I noticed that the Exchange Certificate was showing a RootCAType of GroupPolicy which made me uncomfortable.
I then removed the certificates from the GPO, manually imported the Trusted CA and this resulted in the RootCAType showing Registry.
This again didn’t solve my issue, so I removed the Root CA certificate from the machine, opened a secure HTTPS session to the third party certificate site and the machine downloaded the root CA.
When I checked the certificate after this it displayed ThirdParty, which then resulted in the HCW to pick up the certificates on the transport servers...yay!
You might also get an error message when the HCW runs:
Execution of the Get-FederationInformation cmdlet had thrown an exception. This may indicate invalid parameters in your Hybrid Configuration settings.
In my case Autodiscover was working properly and all pre-flight checks were good so I retried it a couple of times and it went through. :-)
I hope the above assists anyone with the same issue….it was a very interesting one to say the least.
Some more posts coming....
Cheers,
Michael
Comments
Anonymous
May 06, 2013
Hello Michael, Thank you for positing, it really helped me. Best Regards.Anonymous
February 05, 2014
Hey Michael, how are you? I just want to told you that I've followed your instruction, during a lab, to download the Root Cert using HTTPS in the Hybrid Server itself and it worked for me! After that, the RootCAType showed ThirdParty. Thanks!Anonymous
March 18, 2014
Thanks Michael, in the same boat... I want to manually change the RootCAType... I'll try and share the resultsAnonymous
March 18, 2014
Got it, the RootCAType has to do with where the Certificate chain ends within your local certificate stores. My RootCA Certificate had been pushed by GPO to the Trusted Root Certification Authorities Store and needed to be added to the Third Party Root Certification Authorities Store.