View and remediate vulnerabilities for images running on your Kubernetes clusters (Secure Score)
Note
This page describes the classic secure score approach to vulnerability management in Defender for Cloud. Customers using Defender CSPM should use the new risk-based approach: View and remediate vulnerabilities for images running on your Kubernetes clusters (Risk based).
Defender for Cloud gives its customers the ability to prioritize the remediation of vulnerabilities in images that are currently being used within their environment using the Running container images should have vulnerability findings resolved recommendation.
To provide findings for the recommendation, Defender for Cloud uses agentless discovery for Kubernetes or the Defender sensor to create a full inventory of your Kubernetes clusters and their workloads and correlates that inventory with the vulnerability reports created for your registry images. The recommendation shows your running containers with the vulnerabilities associated with the images that are used by each container and remediation steps.
Defender for Cloud presents the findings and related information as recommendations, including related information such as remediation steps and relevant CVEs. You can view the identified vulnerabilities for one or more subscriptions, or for a specific resource.
Within each recommendation, resources are grouped into tabs:
- Healthy resources – relevant resources, which either aren't impacted or on which you've already remediated the issue.
- Unhealthy resources – resources that are still impacted by the identified issue.
- Not applicable resources – resources for which the recommendation can't give a definitive answer. The not applicable tab also includes reasons for each resource.
View vulnerabilities on a specific cluster
To view vulnerabilities for a specific cluster, do the following:
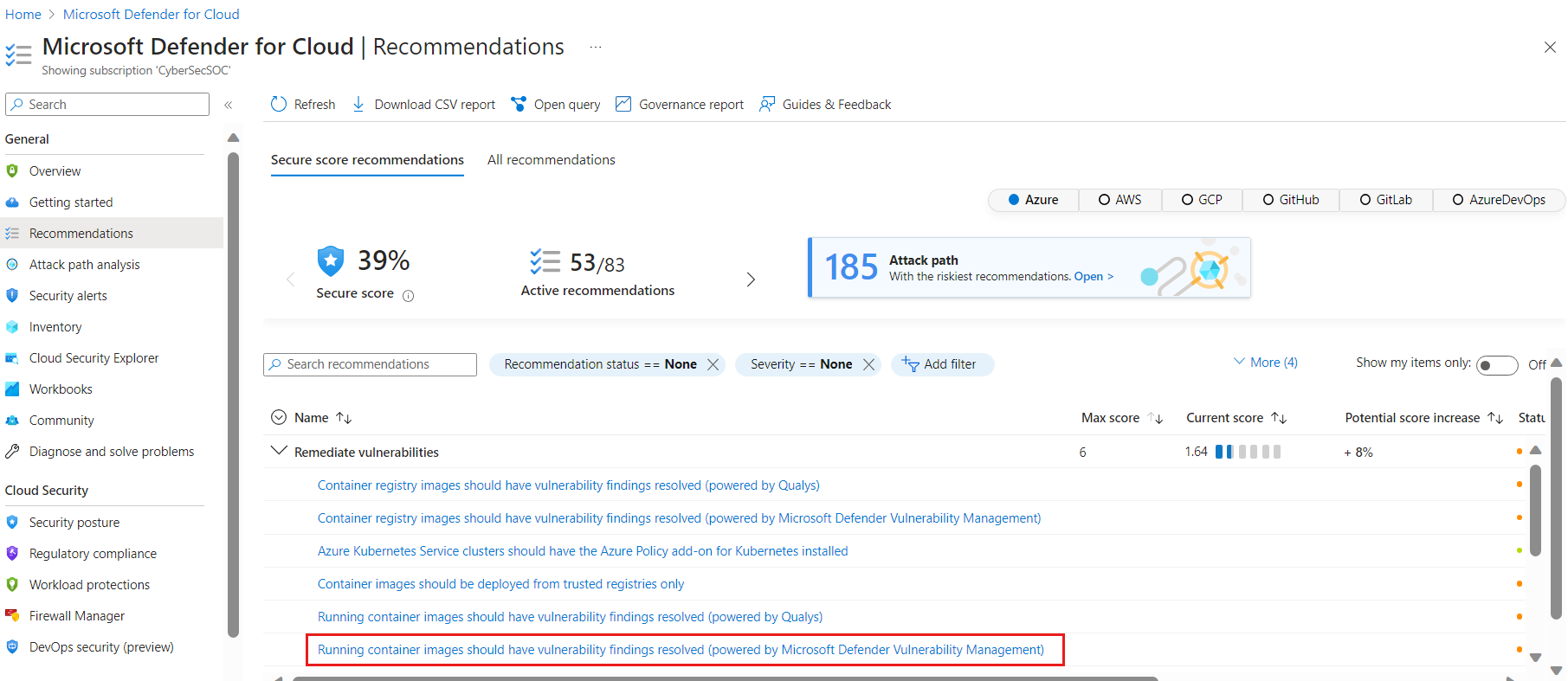
Open the Recommendations page. If you are on the new risk-based page, select Switch to classic view in the menu item on the top of the page. Use the > arrow to open the sub-levels. If issues were found, you'll see the recommendation Running container images should have vulnerability findings resolved (powered by Microsoft Defender Vulnerability Management). Select the recommendation.
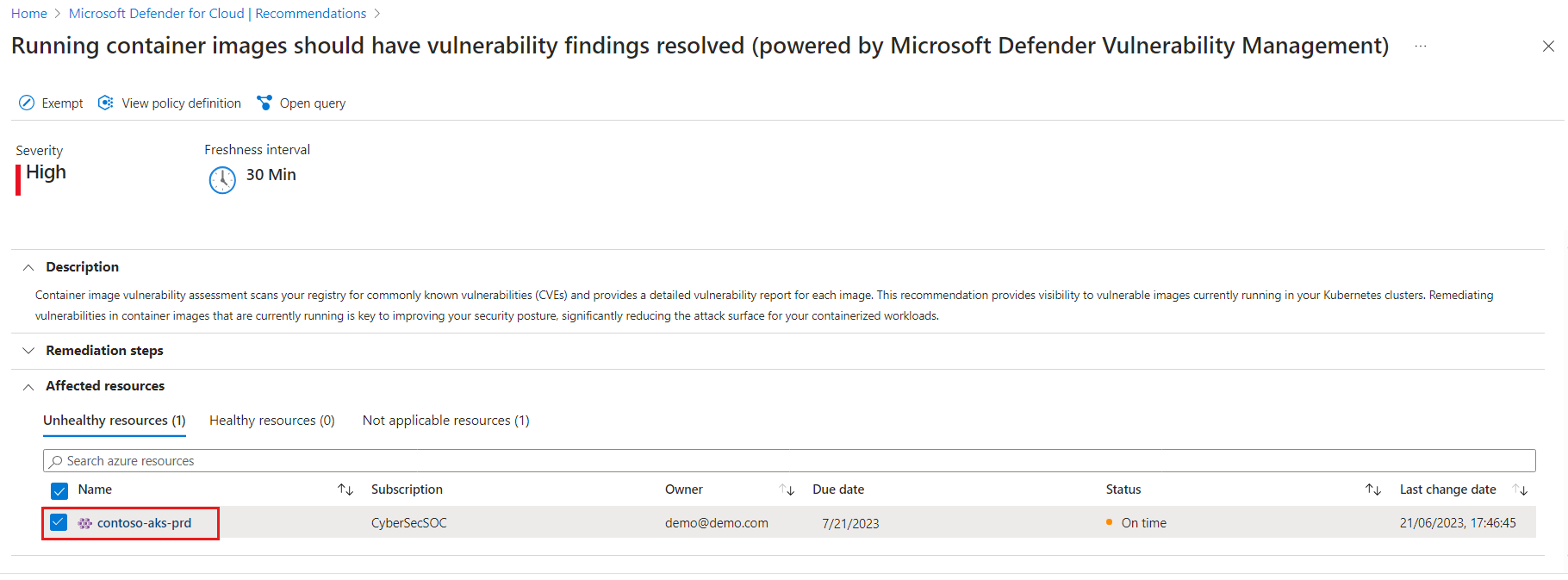
The recommendation details page opens showing the list of Kubernetes clusters ("affected resources") and categorizes them as healthy, unhealthy and not applicable, based on the images used by your workloads. Select the relevant cluster for which you want to remediate vulnerabilities.
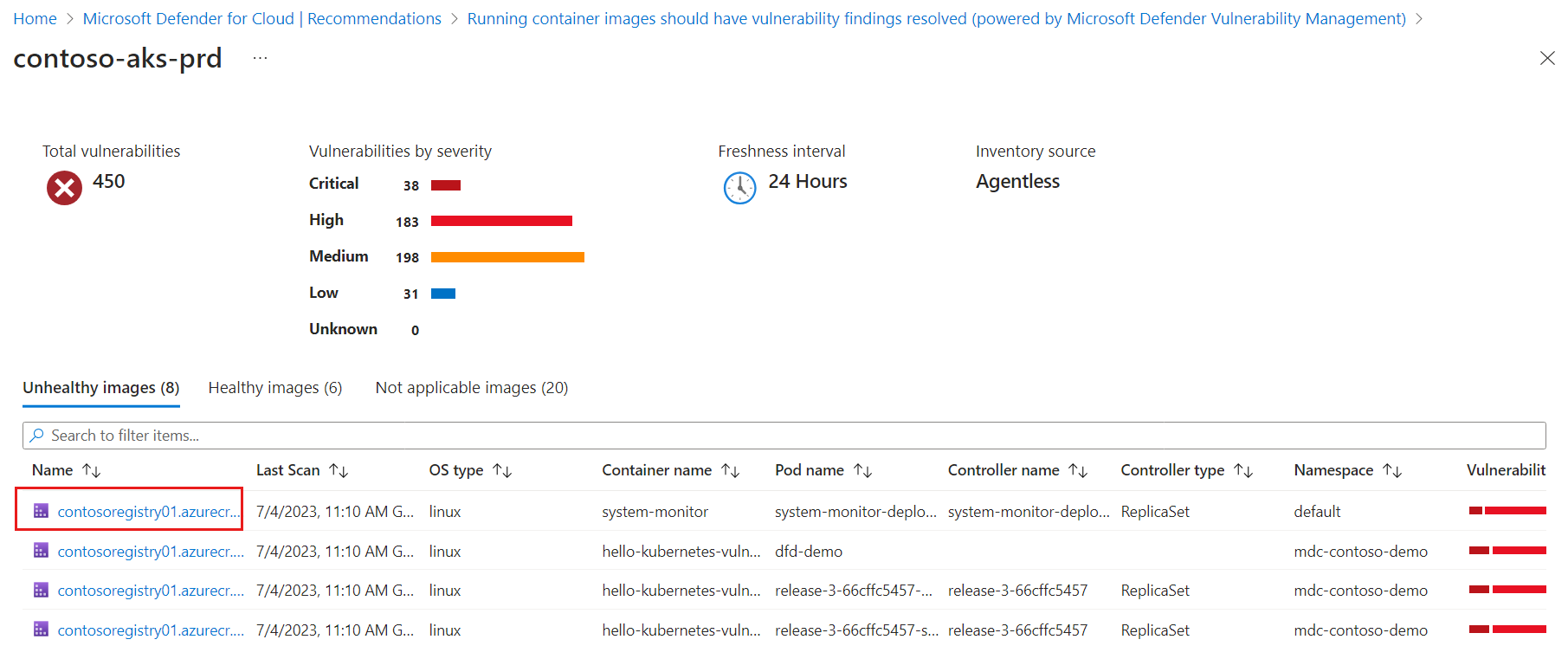
The cluster details page opens. It lists all currently running containers categorized into three tabs based on the vulnerability assessments of the images used by those containers. Select the specific container you want to explore.
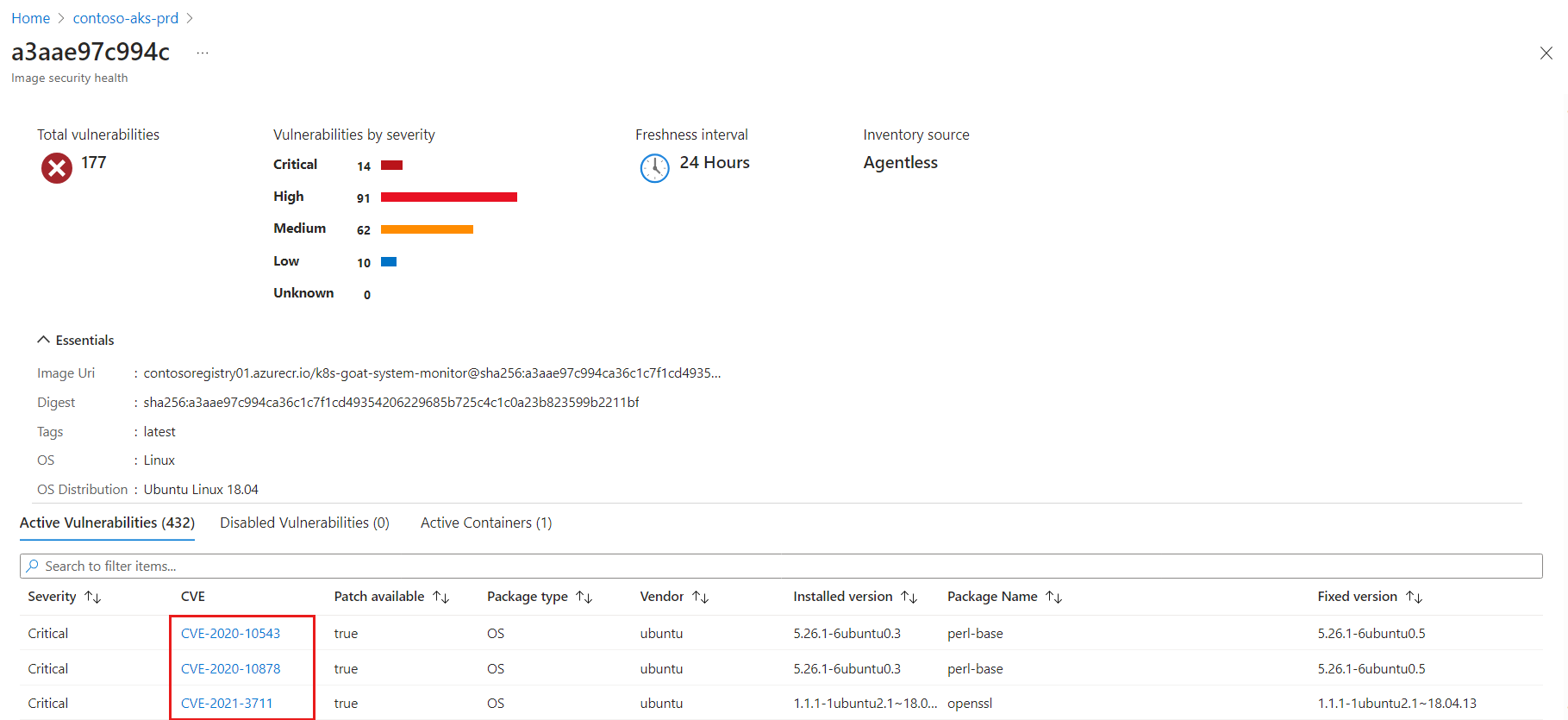
This pane includes a list of the container vulnerabilities. Select each vulnerability to resolve the vulnerability.
View container images affected by a specific vulnerability
To view findings for a specific vulnerability, do the following:
Open the Recommendations page, using the > arrow to open the sub-levels. If issues were found, you'll see the recommendation Running container images should have vulnerability findings resolved (powered by Microsoft Defender Vulnerability Management). Select the recommendation.
The recommendation details page opens with additional information. This information includes the list of vulnerabilities impacting the clusters. Select the specific vulnerability.
The vulnerability details pane opens. This pane includes a detailed description of the vulnerability, images affected by that vulnerability, and links to external resources to help mitigate the threats, affected resources, and information on the software version that contributes to resolving the vulnerability.
Remediate vulnerabilities
Use these steps to remediate each of the affected images found either in a specific cluster or for a specific vulnerability:
- Follow the steps in the remediation section of the recommendation pane.
- When you've completed the steps required to remediate the security issue, replace each affected image in your cluster, or replace each affected image for a specific vulnerability:
- Build a new image (including updates for each of the packages) that resolves the vulnerability according to the remediation details.
- Push the updated image and delete the old image. It might take up to 24 hours for the previous image to be removed from the results, and for the new image to be included in the results.
- Use the new image across all vulnerable workloads.
- Check the recommendations page for the recommendation Running container images should have vulnerability findings resolved.
- If the recommendation still appears and the image you've handled still appears in the list of vulnerable images, check the remediation steps again.
Next steps
- Learn how to view and remediate vulnerabilities for registry images.
- Learn more about the Defender for Cloud Defender plans
Pripomienky
Pripravujeme: V priebehu roka 2024 postupne zrušíme službu Problémy v službe GitHub ako mechanizmus pripomienok týkajúcich sa obsahu a nahradíme ju novým systémom pripomienok. Ďalšie informácie nájdete na stránke: https://aka.ms/ContentUserFeedback.
Odoslať a zobraziť pripomienky pre