Exclude devices
Applies to:
- Microsoft Defender for Endpoint Plan 1
- Microsoft Defender for Endpoint Plan 2
- Microsoft Defender XDR
Want to experience Defender for Endpoint? Sign up for a free trial.
Exclude devices from vulnerability management
Excluding devices that are inactive, duplicate, or out of scope allows you to focus on discovering and prioritizing the risks on your active devices. This action can also help reflect a more accurate vulnerability management exposure score, as the excluded devices won't be visible in your vulnerability management reports.
Once devices are excluded, you won't be able to view updated or relevant information about vulnerabilities and installed software on these devices. It affects all vulnerability management pages, reports, and related tables in advanced hunting.
Even though the device exclusion feature removes the device data from vulnerability management pages and reports, the devices remain connected to the network and can still be a risk to the organization. You'll be able to cancel the device exclusion at any time.
How to exclude a device
You can choose to exclude a single device or multiple devices at the same time.
Exclude a single device
Go to the Device inventory page and select the device to exclude.
Select Exclude from the action bar on the device inventory page or from the actions menu in the device flyout.

Select a justification:
- Inactive device
- Duplicate device
- Device doesn't exist
- Out of scope
- Other
Type a note and select Exclude device.
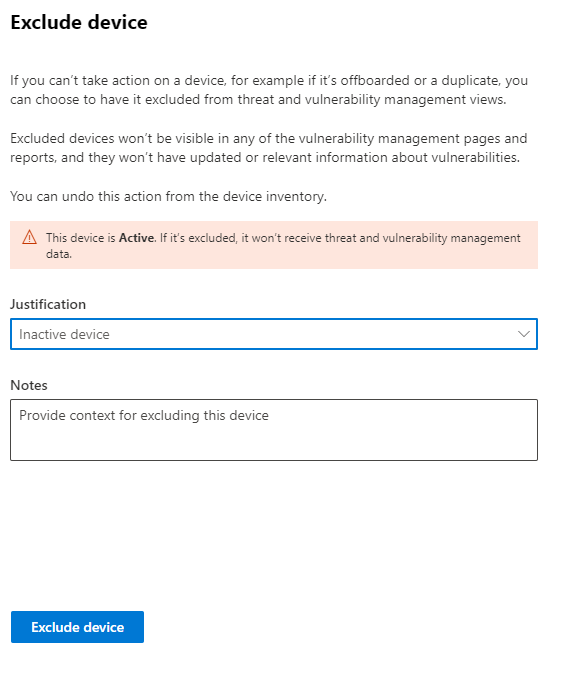
You can also exclude a device from its device page.
Note
Excluding active devices is not recommended, since it is especially risky to not have visibility into their vulnerability info. If a device is active and you try to exclude it, you'll get a warning message and a confirmation pop-up asking if you are sure you want to exclude an active device.
It can take up to 10 hours for a device to be fully excluded from vulnerability management views and data.
Excluded devices are still visible in the Device inventory list. You can manage your view of excluded devices by:
- Adding the Exclusion state column to the device inventory view.
- Using the Exclusion state filter to view the relevant list of devices.

Bulk device exclusion
You can also choose to exclude multiple devices at the same time:
Go to the Device inventory page and select the devices to exclude.
From the actions bar, select Exclude.
Choose a justification and select Exclude device.
If you select multiple devices in the device list with different exclusion statuses, the exclude selected devices flyout will provide you details on how many of the selected devices are already excluded. You can exclude the devices again, but the justification and notes will be overridden.

Once a device is excluded, if you go to the device page of an excluded device, you won't be able to see data for discovered vulnerabilities, software inventory or security recommendations. The data also won't show up in vulnerability management pages, related advanced hunting tables and the vulnerable devices report.
Stop excluding a device
You'll be able to stop excluding a device at any time. Once devices are no longer excluded, their vulnerability data will be visible in vulnerability management pages, reports, and in advanced hunting. It may take up to 8 hours for the changes to take effect.
- Go to the Device inventory, select the excluded device to open the flyout, and then select Exclusion details
- Select Stop exclusion

See also
Tip
Do you want to learn more? Engage with the Microsoft Security community in our Tech Community: Microsoft Defender for Endpoint Tech Community.