Secure Key Release feature with AKV and Azure Confidential Computing (ACC)
Secure Key Release (SKR) is a functionality of Azure Key Vault (AKV) Managed HSM and Premium offering. Secure key release enables the release of an HSM protected key from AKV to an attested Trusted Execution Environment (TEE), such as a secure enclave, VM based TEEs etc. SKR adds another layer of access protection to your data decryption/encryption keys where you can target an application + TEE runtime environment with known configuration get access to the key material. The SKR policies defined at the time of exportable key creation govern the access to these keys.
SKR support with AKV offerings
Overall Secure Key Release Flow with TEE
SKR can only release keys based on the Microsoft Azure Attestation (MAA) generated claims. There's a tight integration on the SKR policy definition to MAA claims.
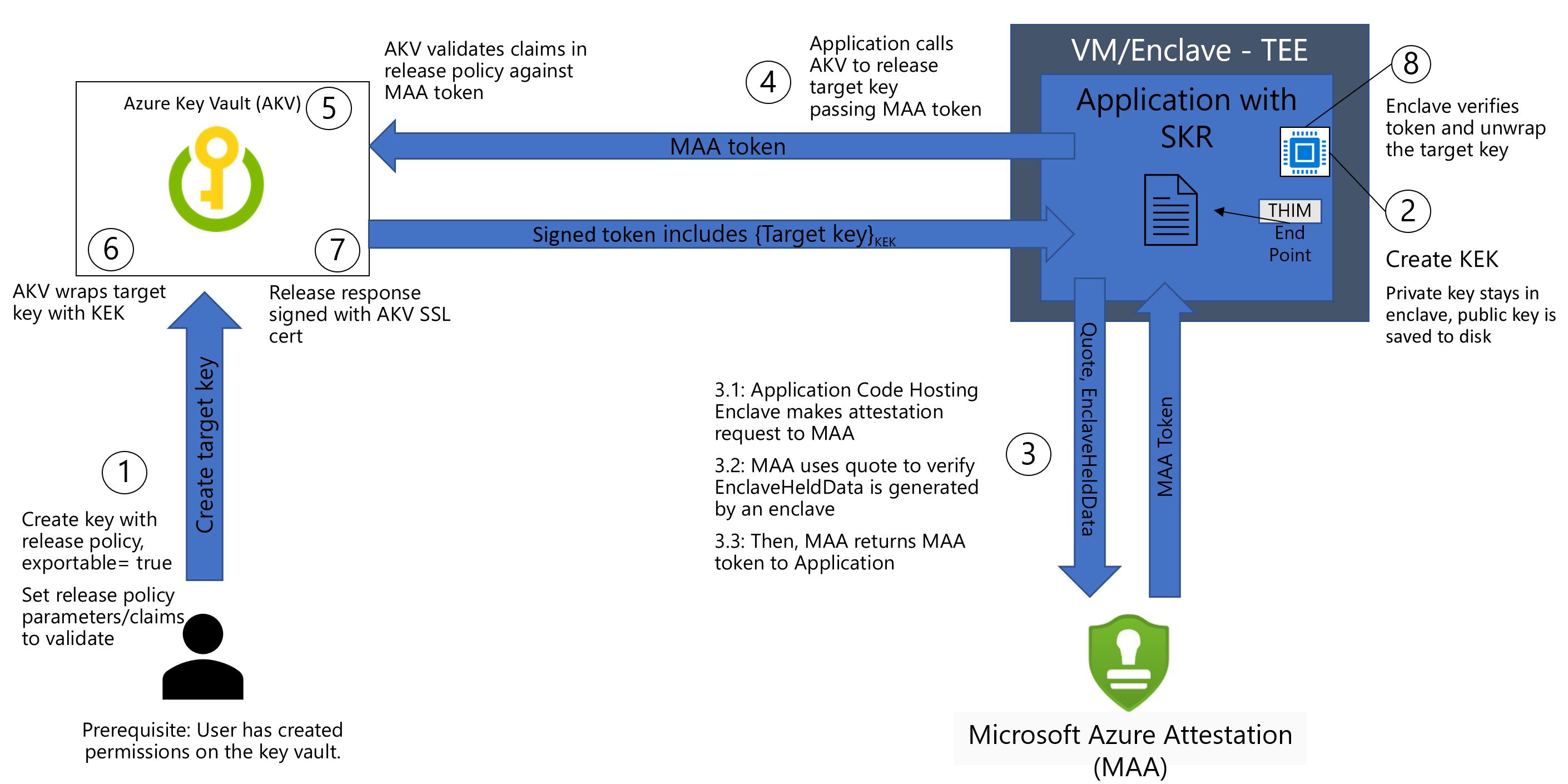
The below steps are for AKV Premium.
Step 1: Create a Key Vault Premium HSM Backed
Follow the details here for Az CLI based AKV creation
Make sure to set the value of [--sku] to "premium".
Step 2: Create a Secure Key Release Policy
A Secure Key Release Policy is a json format release policy as defined here that specifies a set of claims required in addition to authorization to release the key. The claims here are MAA based claims as referenced here for SGX and here for AMD SEV-SNP CVM.
Visit the TEE specific examples page for more details. For more information on the SKR policy grammar, see Azure Key Vault secure key release policy grammar.
Before you set an SKR policy make sure to run your TEE application through the remote attestation flow. Remote attestation isn't covered as part of this tutorial.
Example
{
"version": "1.0.0",
"anyOf": [ // Always starts with "anyOf", meaning you can multiple, even varying rules, per authority.
{
"authority": "https://sharedweu.weu.attest.azure.net",
"allOf": [ // can be replaced by "anyOf", though you cannot nest or combine "anyOf" and "allOf" yet.
{
"claim": "x-ms-isolation-tee.x-ms-attestation-type", // These are the MAA claims.
"equals": "sevsnpvm"
},
{
"claim": "x-ms-isolation-tee.x-ms-compliance-status",
"equals": "azure-compliant-cvm"
}
]
}
]
}
Step 3: Create an exportable key in AKV with attached SKR policy
Exact details of the type of key and other attributes associated can be found here.
az keyvault key create --exportable true --vault-name "vault name from step 1" --kty RSA-HSM --name "keyname" --policy "jsonpolicyfromstep3 -can be a path to JSON"
Step 4: Application running within a TEE doing a remote attestation
This step can be specific to the type of TEE you're running your application Intel SGX Enclaves or AMD SEV-SNP based Confidential Virtual Machines (CVM) or Confidential Containers running in CVM Enclaves with AMD SEV-SNP etc.
Follow these references examples for various TEE types offering with Azure:
- Application within AMD EV-SNP based CVM's performing Secure Key Release
- Confidential containers with Azure Container Instances (ACI) with SKR side-car containers
- Intel SGX based applications performing Secure Key Release - Open Source Solution Mystikos Implementation
Frequently Asked Questions (FAQ)
Can I perform SKR with non confidential computing offerings?
No. The policy attached to SKR only understands MAA claims that are associated to hardware based TEEs.
Can I bring my own attestation provider or service and use those claims for AKV to validate and release?
No. AKV only understands and integrates with MAA today.
Can I use AKV SDKs to perform key RELEASE?
Yes. Latest SDK integrated with 7.3 AKV API's support key RELEASE.
Can you share some examples of the key release policies?
Yes, detailed examples by TEE type are listed here.
Can I attach SKR type of policy with certificates and secrets?
No. Not at this time.
References
Azure Container Instance with confidential containers Secure Key Release with container side-cars
CVM on AMD SEV-SNP Applications with Secure Key Release Example