Investigate and respond to an OT network alert
This article describes how to investigate and respond to an OT network alert in Microsoft Defender for IoT.
You might be a security operations center (SOC) engineer using Microsoft Sentinel, who's seen a new incident in your Microsoft Sentinel workspace and is continuing in Defender for IoT for further details about related devices and recommended remediation steps.
Alternately, you might be an OT engineer watching for operational alerts directly in Defender for IoT. Operational alerts might not be malicious but can indicate operational activity that can aid in security investigations.
Prerequisites
Before you start, make sure that you have:
An Azure subscription. If you need to, sign up for a free account.
A cloud-connected OT network sensor onboarded to Defender for IoT, with alerts streaming into the Azure portal.
To investigate an alert from a Microsoft Sentinel incident, make sure that you've completed the following tutorials:
An alert details page open, accessed either from the Defender for IoT Alerts page in the Azure portal, a Defender for IoT device details page, or a Microsoft Sentinel incident.
Investigate an alert from the Azure portal
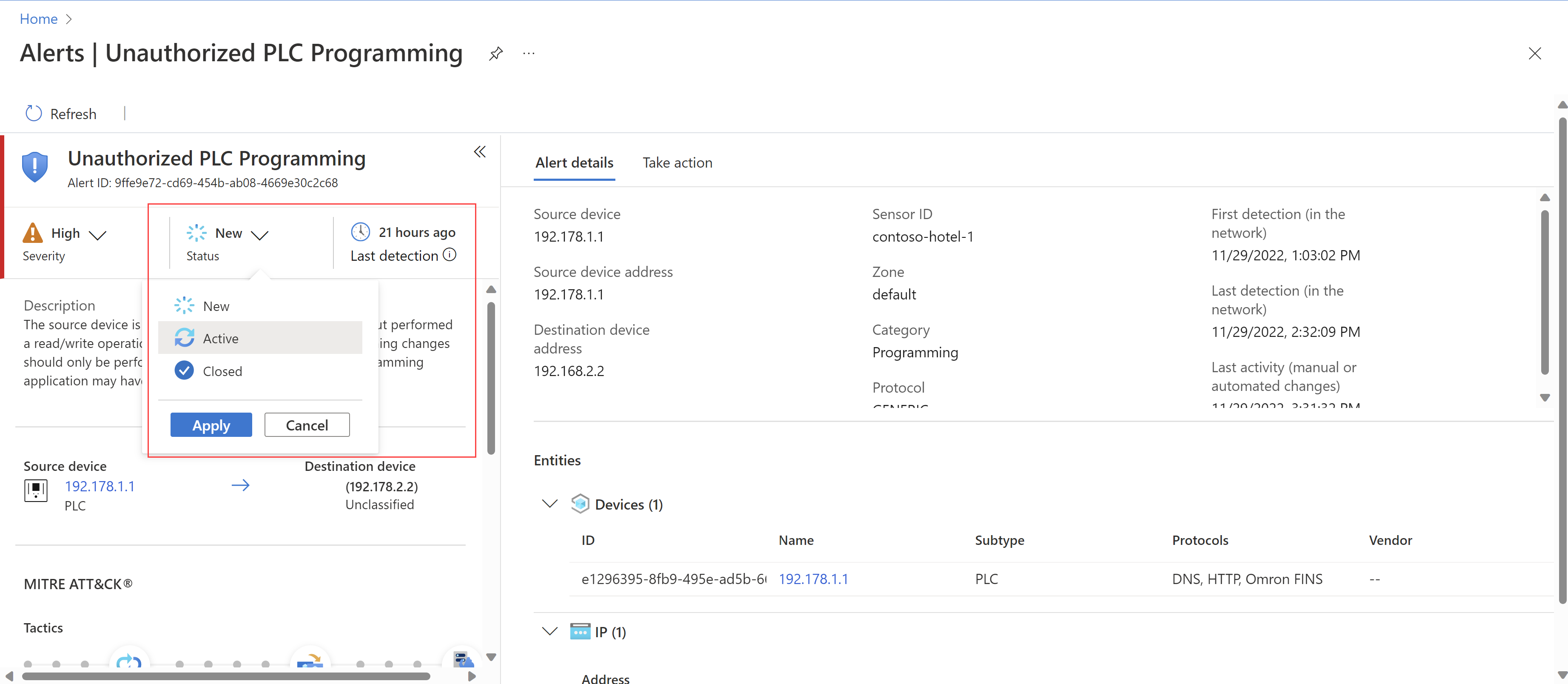
On an alert details page in the Azure portal, start by changing the alert status to Active, indicating that it's currently under investigation.
For example:
Important
If you're integrating with Microsoft Sentinel, make sure to manage your alert status only from the incident in Microsoft Sentinel. Alerts statuses are not synchronized from Defender for IoT to Microsoft Sentinel.
After updating the status, check the alert details page for the following details to aid in your investigation:
Source and destination device details. Source and destination devices are listed in Alert details tab, and also in the Entities area below, as Microsoft Sentinel entities, with their own entity pages. In the Entities area, you'll use the links in the Name column to open the relevant device details pages for further investigation.
Site and/or zone. These values help you understand the geographic and network location of the alert and if there are areas of the network that are now more vulnerable to attack.
MITRE ATT&CK tactics and techniques. Scroll down in the left pane to view all MITRE ATT&CK details. In addition to descriptions of the tactics and techniques, select the links to the MITRE ATT&CK site to learn more about each one.
Download PCAP. At the top of the page, select Download PCAP to download the raw traffic files for the selected alert.
Investigate related alerts on the Azure portal
Look for other alerts triggered by the same source or destination device. Correlations between multiple alerts may indicate that the device is at risk and can be exploited.
For example, a device that attempted to connect to a malicious IP, together with another alert about unauthorized PLC programming changes on the device, might indicate that an attacker has already gained control of the device.
To find related alerts in Defender for IoT:
On the Alerts page, select an alert to view details on the right.
Locate the device links in the Entities area, either in the details pane on the right or in the alert details page. Select an entity link to open the related device details page, for both a source and destination device.
On the device details page, select the Alerts tab to view all alerts for that device. For example:
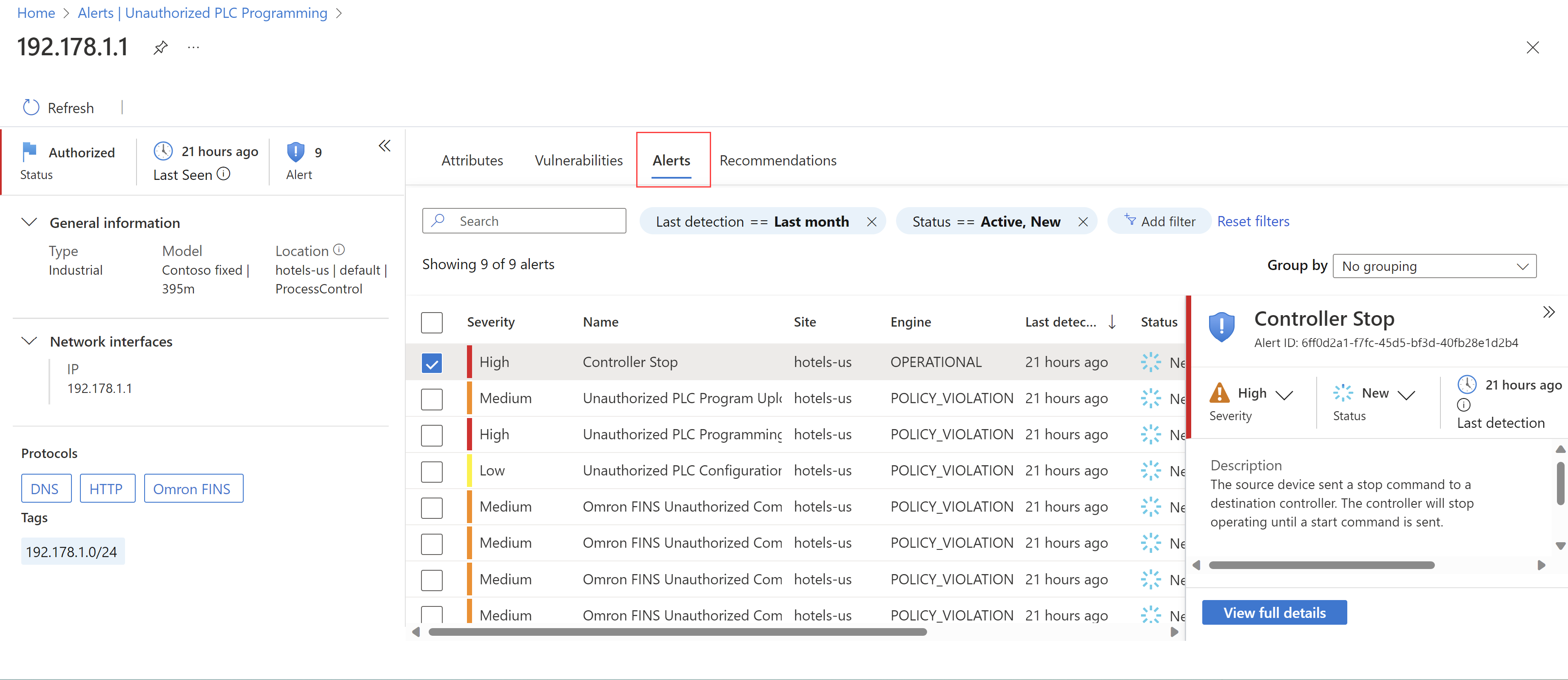
Investigate alert details on the OT sensor
The OT sensor that triggered the alert will have more details to help your investigation.
To continue your investigation on the OT sensor:
Sign into your OT sensor as a Viewer or Security Analyst user.
Select the Alerts page and find then alert you're investigating. Select **View more details to open the OT sensor's alert details page. For example:
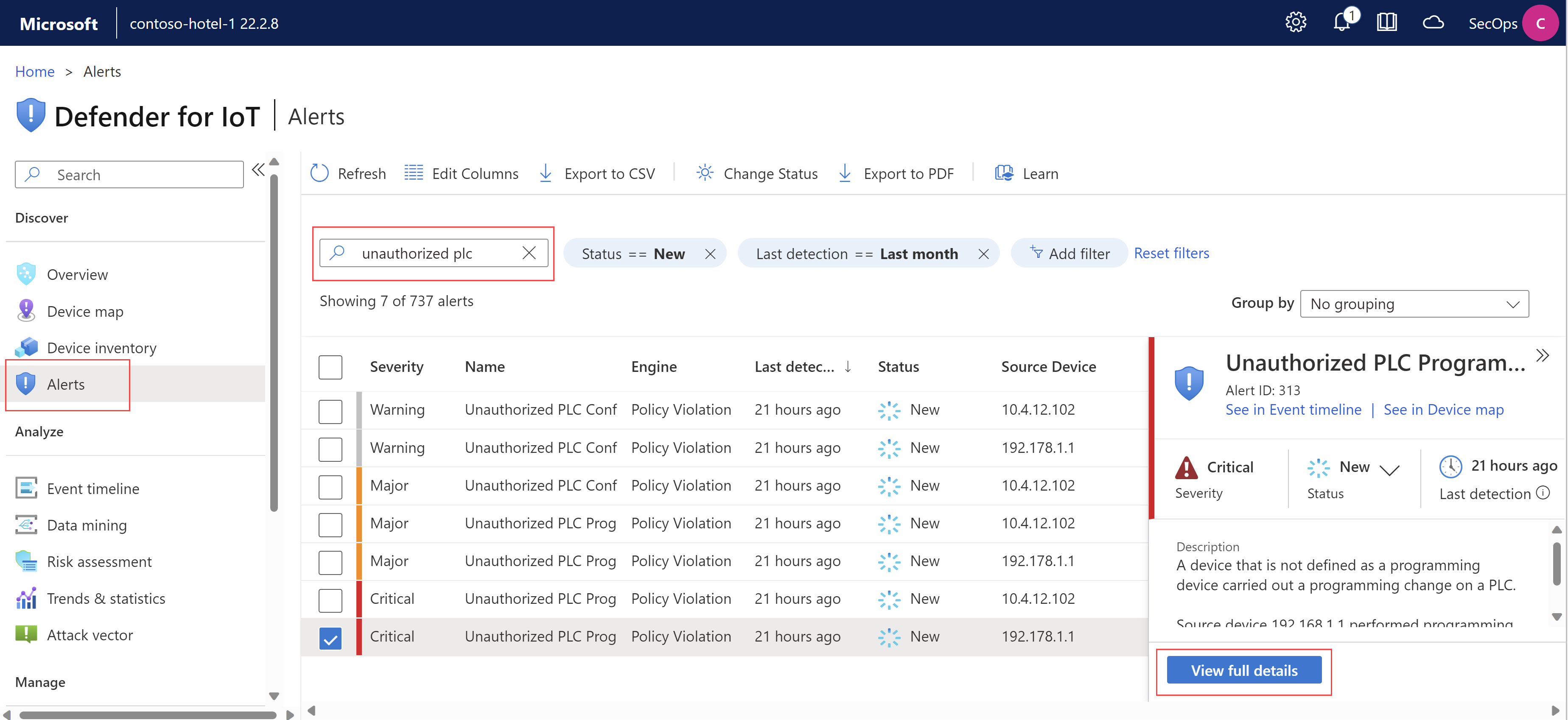
On the sensor's alert details page:
Select the Map view tab to view the alert inside the OT sensor's device map, including any connected devices.
Select the Event timeline tab to view the alert's full event timeline, including other related activity also detected by the OT sensor.
Select Export PDF to download a PDF summary of the alert details.
Take remediation action
The timing for when you take remediation actions may depend on the severity of the alert. For example, for high severity alerts, you might want to take action even before investigating, such as if you need to immediately quarantine an area of your network.
For lower severity alerts, or for operational alerts, you might want to fully investigate before taking action.
To remediate an alert, use the following Defender for IoT resources:
On an alert details page on either the Azure portal or the OT sensor, select the Take action tab to view details about recommended steps to mitigate the risk.
On a device details page in the Azure portal, for both the source and destination devices:
Select the Vulnerabilities tab and check for detected vulnerabilities on each device.
Select the Recommendations tab and check for current security recommendations for each device.
Defender for IoT vulnerability data and security recommendations can provide simple actions you can take to mitigate the risks, such as updating firmware or applying a patch. Other actions may take more planning.
When you've finished with mitigation activities and are ready to close the alert, make sure to update the alert status to Closed or notify your SOC team for further incident management.
Note
If you integrate Defender for IoT with Microsoft Sentinel, alert status changes you make in Defender for IoT are not updated in Microsoft Sentinel. Make sure to manage your alerts in Microsoft Sentinel together with the related incident.
Triage alerts regularly
Triage alerts on a regular basis to prevent alert fatigue in your network and ensure that you're able to see and handle important alerts in a timely manner.
To triage alerts:
In Defender for IoT in the Azure portal, go to the Alerts page. By default, alerts are sorted by the Last detection column, from most recent to oldest alert, so that you can first see the latest alerts in your network.
Use other filters, such as Sensor or Severity to find specific alerts.
Check the alert details and investigate as needed before you take any alert action. When you're ready, take action on an alert details page for a specific alert, or on the Alerts page for bulk actions.
For example, update alert status or severity, or learn an alert to authorize the detected traffic. Learned alerts are not triggered again if the same exact traffic is detected again.
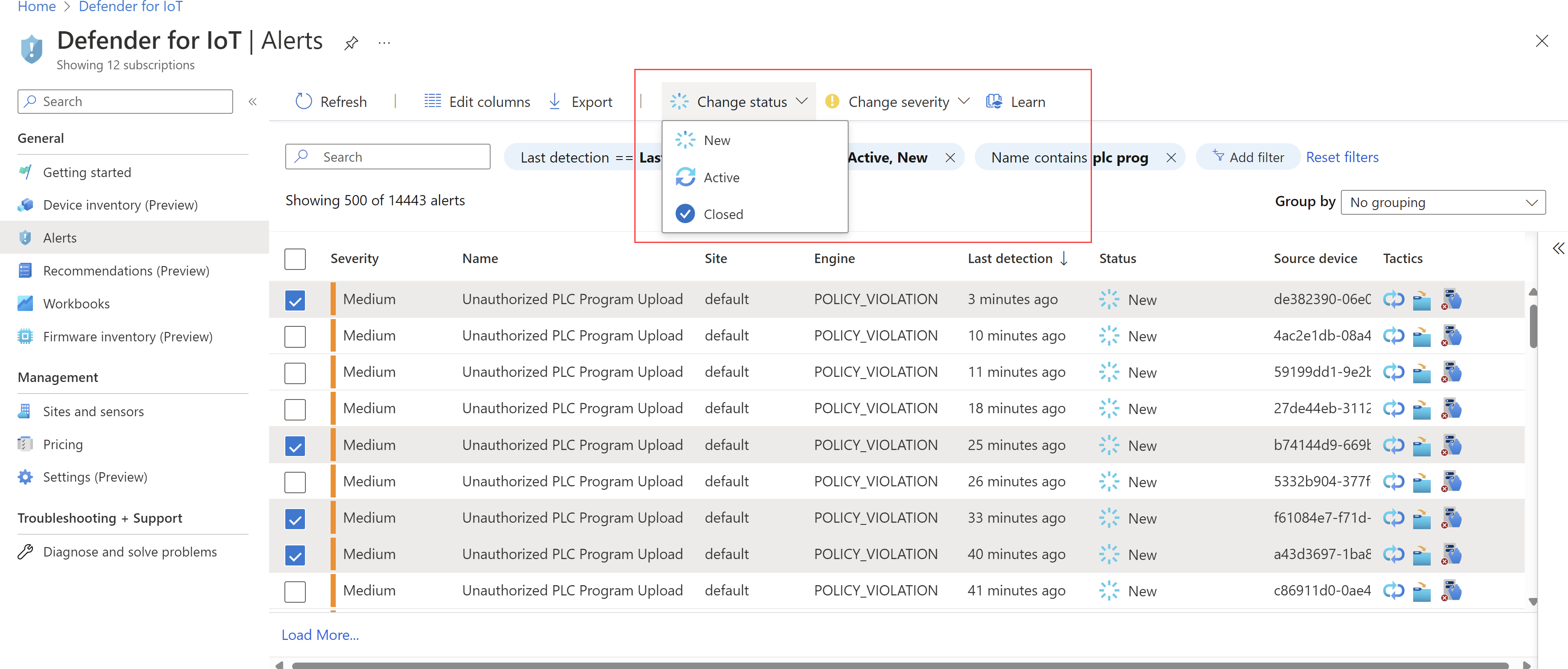
For high severity alerts, you may want to take action immediately.