Microsoft Entra recommendation: Renew expiring service principal credentials (preview)
Microsoft Entra recommendations is a feature that provides you with personalized insights and actionable guidance to align your tenant with recommended best practices.
This article covers the recommendation to renew expiring service principal credentials. This recommendation is called servicePrincipalKeyExpiry in the recommendations API in Microsoft Graph.
Prerequisites
There are different role requirements for viewing or updating a recommendation. Use the least-privileged role for the type of access needed. For a full list of roles, see Least privileged roles by task.
| Microsoft Entra role | Access type |
|---|---|
| Reports Reader | Read-only |
| Security Reader | Read-only |
| Global Reader | Read-only |
| Authentication Policy Administrator | Update and read |
| Exchange Administrator | Update and read |
| Security Administrator | Update and read |
DirectoryRecommendations.Read.All |
Read-only in Microsoft Graph |
DirectoryRecommendations.ReadWrite.All |
Update and read in Microsoft Graph |
Some recommendations might require a P2 or other license. For more information, see the Recommendations overview table.
Description
Service principal credentials include certificates and client secrets added to a service principal. The credentials are used to prove the identity of that service principal. If the credentials expire, the service principal can't authenticate, which can cause downtime for your business scenario. This recommendation shows up if your tenant has service principals with credentials that are expiring soon.
A service principal credential is expiring if:
- It's on a service principal AND is expiring within the next 30 days.
The following credentials are exempted from this recommendation:
- Credentials that were identified as expiring but have since been removed from the application registration.
- Credentials whose expiration date has lapsed show as completed in the list of Impacted resources.
Value
Renewing a service principal's credentials prior to their expiry date is crucial for maintaining uninterrupted operations and minimizing the risk of any downtime resulting from outdated credentials.
Action plan
This recommendation is available in the Microsoft Entra admin center and using the Microsoft Graph API.
Sign in to the Microsoft Entra admin center as at least a Security Administrator.
Browse to Identity > Overview.
Select the Recommendations tab and select the Renew expiring service principal credentials recommendation.
Select More Details from the Actions column.
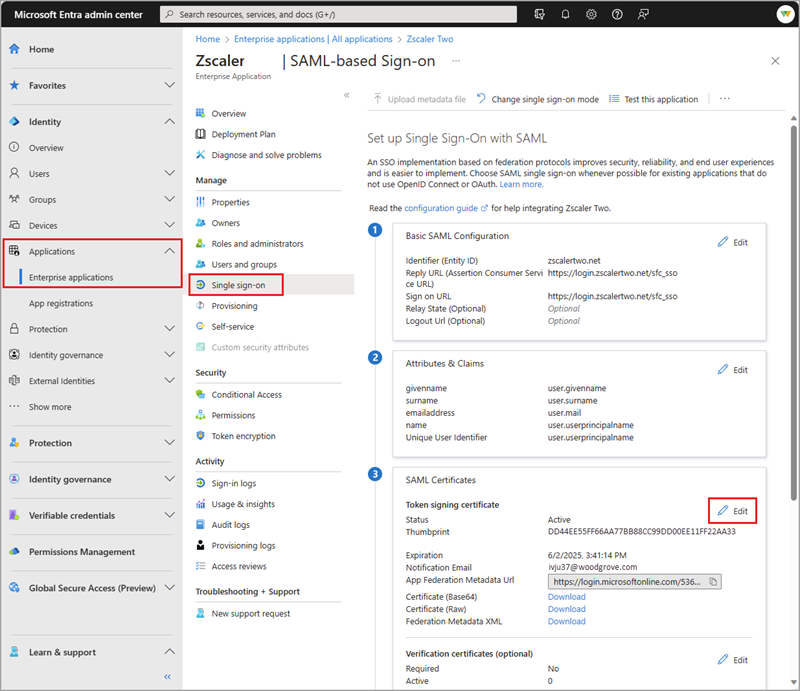
From the panel that opens, select Update Credential to navigate directly to the Single sign-on area of the app registration.
- Alternatively, browse to Identity > Applications > App registrations and locate the application for which the credential needs to be rotated.
- Navigate to the Single sign-on section of the app registration.
Edit the SAML signing certificate section and follow the prompts to add a new certificate.
Once the certificate or secret is successfully added, update the SAML signing certificate configuration to make the new cert active.
Verify that the application works as expected then remove the inactive SAML certificate from the SAML certificates collection.
Note
If you don't have any SAML credentials configured but you received this recommendation, use the Microsoft Graph ServicePrincipalAPI endpoint to check the keyCredentials and passwordCredentials properties of the service principal object. Locate and rotate the credential.
We highly recommend changing your service so that it works with the credential defined on the backing application object instead of the service principal.