Attack path analysis and enhanced risk-hunting for containers
Attack path analysis is a graph-based algorithm that scans the cloud security graph. The scans expose exploitable paths that attackers might use to breach your environment to reach your high-impact assets. Attack path analysis exposes attack paths and suggests recommendations as to how best remediate issues that break the attack path and prevent successful breach.
Explore and investigate attack paths by sorting them based on risk level, name, environment, and risk factors, entry point, target, affected resources and active recommendations. Explore cloud security graph Insights on the resource. Examples of Insight types are:
- Pod exposed to the internet
- Privileged container
- Pod uses host network
- Container image is vulnerable to remote code execution
Azure: Testing the attack path and security explorer using a mock vulnerable container image
If there are no entries in the list of attack paths, you can still test this feature by using a mock container image. Use the following steps to set up the test:
Requirement: An instance of Azure Container Registry (ACR) in the tested scope.
Import a mock vulnerable image to your Azure Container Registry:
First, pull a base image (for example, alpine) to your local environment by running:
docker pull alpineTag the image with the following label and push it to your ACR. Replace
<MYACR>with your Azure Container Registry name:docker tag alpine <MYACR>.azurecr.io/mdc-mock-0001 docker push <MYACR>.azurecr.io/mdc-mock-0001If you don't have an AKS (Azure Kubernetes Service) cluster, use the following command to create a new AKS cluster:
az aks create -n myAKSCluster -g myResourceGroup --generate-ssh-keys --attach-acr $MYACRIf your AKS isn't attached to your ACR, use the following Cloud Shell command line to point your AKS instance to pull images from the selected ACR:
az aks update -n myAKSCluster -g myResourceGroup --attach-acr <acr-name>
Authenticate your Cloud Shell session to work with the cluster:
az aks get-credentials --subscription <cluster-suid> --resource-group <your-rg> --name <your-cluster-name>Install the ngnix ingress Controller :
helm install ingress-controller oci://ghcr.io/nginxinc/charts/nginx-ingress --version 1.0.1Deploy the mock vulnerable image to expose the vulnerable container to the internet by running the following command:
helm install dcspmcharts oci://mcr.microsoft.com/mdc/stable/dcspmcharts --version 1.0.0 --namespace mdc-dcspm-demo --create-namespace --set image=<your-image-uri> --set distribution=AZUREVerify success by doing the following steps:
- Look for an entry with mdc-dcspm-demo as namespace
- In the Workloads-> Deployments tab, verify "pod1" and "pod2" are created 3/3 and ingress-controller-nginx-ingress-controller is created 1/1.
- In services and ingresses look for-> service service1 and ingress-controller-nginx-ingress-controller. In the ingress tab, verify one ingress is created with an IP address and nginx class.
Note
After completing the above flow, it can take up to 24 hours to see results in the cloud security explorer and attack path.
After you completed testing the attack path, investigate the created attack path by going to Attack path analysis, and search for the attack path you created. For more information, see Identify and remediate attack paths.
AWS: Testing the attack path and security explorer using a mock vulnerable container image
Create an ECR repository named mdc-mock-0001
Go to your AWS account and choose Command line or programmatic access.
Open a command line and choose Option 1: Set AWS environment variables (Short-term credentials). Copy the credentials of the AWS_ACCESS_KEY_ID, AWS_SECRET_ACCESS_KEY, and AWS_SESSION_TOKEN environment variables.
Run the following command to get the authentication token for your Amazon ECR registry. Replace
<REGION>with the region of your registry. Replace<ACCOUNT>with your AWS account ID.aws ecr get-login-password --region <REGION> | docker login --username AWS --password-stdin <ACCOUNT>.dkr.ecr.<REGION>.amazonaws.comCreate a Docker image that is tagged as vulnerable by name. The name of the image should contain the string mdc-mock-0001. Once you created the image, push it to your ECR registry, with the following command (replace
<ACCOUNT>and<REGION>with your AWS account ID and region):docker pull alpine docker tag alpine <ACCOUNT>.dkr.ecr.<REGION>.amazonaws.com/mdc-mock-0001 docker push <ACCOUNT>.dkr.ecr.<REGION>.amazonaws.com/mdc-mock-0001Connect to your EKS cluster and install the provided Helm chart. Configure
kubectlto work with your EKS cluster. Run this command (replace<your-region>and<your-cluster-name>with your EKS cluster region and name):aws eks --region <your-region> update-kubeconfig --name <your-cluster-name>Verify the configuration. You can check if
kubectlis correctly configured by running:kubectl get nodesInstall the ngnix ingress Controller :
helm install ingress-controller oci://ghcr.io/nginxinc/charts/nginx-ingress --version 1.0.1Install the following Helm chart:
helm install dcspmcharts oci://mcr.microsoft.com/mdc/stable/dcspmcharts --version 1.0.0 --namespace mdc-dcspm-demo --create-namespace --set image=<ACCOUNT>.dkr.ecr.<REGION>.amazonaws.com/mdc-mock-0001 --set distribution=AWS
The Helm chart deploys resources onto your cluster that can be used to infer attack paths. It also includes the vulnerable image.
Note
After completing the above flow, it can take up to 24 hours to see results in the cloud security explorer and attack path.
After you completed testing the attack path, investigate the created attack path by going to Attack path analysis, and search for the attack path you created. For more information, see Identify and remediate attack paths.
GCP: Testing the attack path and security explorer using a mock vulnerable container image
In the GCP portal, search for Artifact Registry, and then create a GCP repository named mdc-mock-0001
Follow these instructions to push the image to your repository. Run these commands:
docker pull alpine docker tag alpine <LOCATION>-docker.pkg.dev/<PROJECT_ID>/<REGISTRY>/<REPOSITORY>/mdc-mock-0001 docker push <LOCATION>-docker.pkg.dev/<PROJECT_ID>/<REGISTRY>/<REPOSITORY>/mdc-mock-0001Go to the GCP portal. Then go to Kubernetes Engine > Clusters. Select the Connect button.
Once connected, either run the command in the Cloud Shell or copy the connection command and run it on your machine:
gcloud container clusters get-credentials contra-bugbash-gcp --zone us-central1-c --project onboardingc-demo-gcp-1Verify the configuration. You can check if
kubectlis correctly configured by running:kubectl get nodesTo install the Helm chart, follow these steps:
Under Artifact registry in the portal, go to the repository, and find the image URI under Pull by digest.
Use the following command to install the Helm chart:
helm install dcspmcharts oci:/mcr.microsoft.com/mdc/stable/dcspmcharts --version 1.0.0 --namespace mdc-dcspm-demo --create-namespace --set image=<IMAGE_URI> --set distribution=GCP
The Helm chart deploys resources onto your cluster that can be used to infer attack paths. It also includes the vulnerable image.
Note
After completing the above flow, it can take up to 24 hours to see results in the cloud security explorer and attack path.
After you completed testing the attack path, investigate the created attack path by going to Attack path analysis, and search for the attack path you created. For more information, see Identify and remediate attack paths.
Find container posture issues with cloud security explorer
You can build queries in one of the following ways:
- Explore risks with built-in cloud security explorer templates
- Create custom queries with cloud security explorer
In the following sections, we present examples of queries you can select or create.
Explore risks with cloud security explorer templates
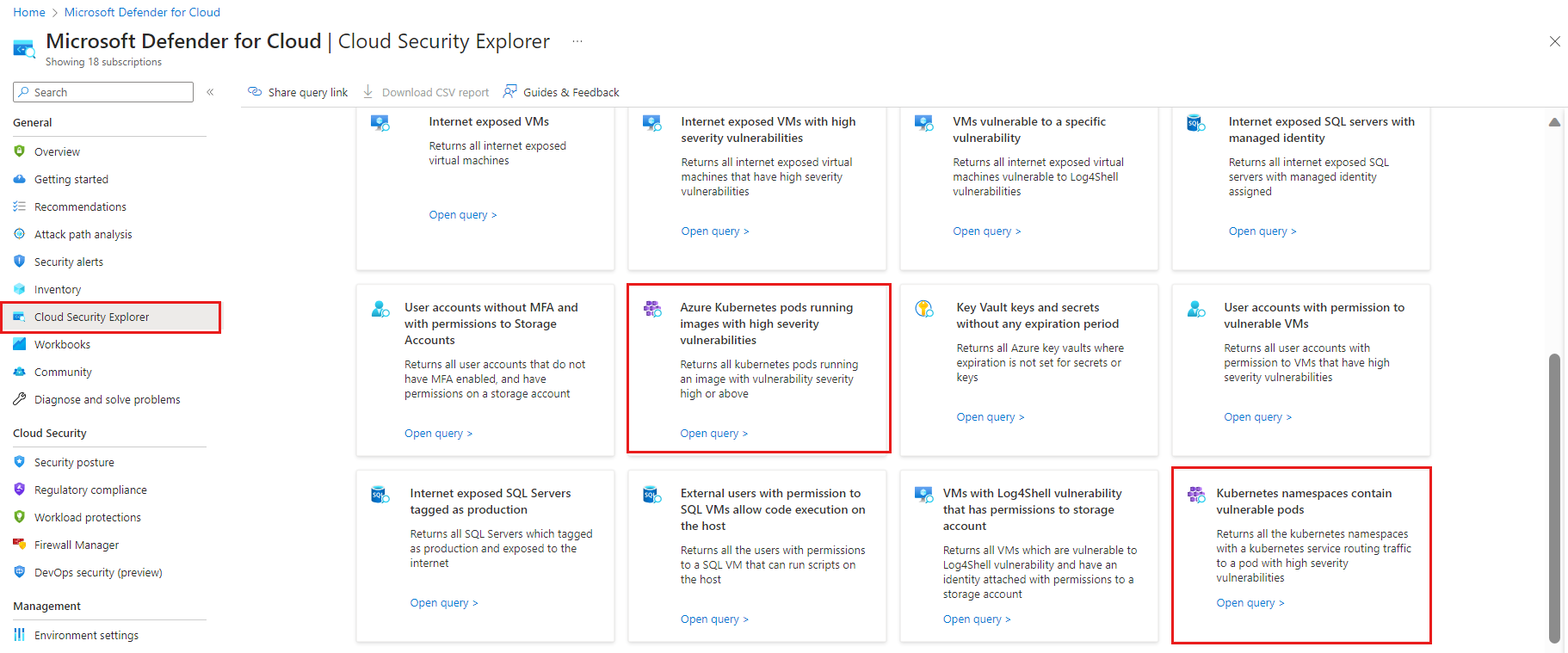
From the Defender for Cloud overview page, open the cloud security explorer.
Some out of the box templates for Kubernetes appear. Select one of the templates:
- Azure Kubernetes pods running images with high severity vulnerabilities
- Kubernetes namespaces contain vulnerable pods
Select Open query; the template builds the query in the upper portion of the screen. Select Search to view the results.
Create custom queries with cloud security explorer
You can also create your own custom queries. The following example shows a search for pods running container images that are vulnerable to remote code execution.
The results are listed below the query.
Next steps
- Learn more about the Defender for Cloud Defender plans.