Virtual Tech Days – September 2008 – Virtualization Security
Hi I am Ravi Sankar (https://ravisankar.spaces.live.com/blog) from the TechNet India team. First of all let me thank everyone who attended the sessions under virtualization track. We have received hundreds of questions as part of the sessions and due to time constraints the speakers could answer only a few of them. So I am taking this opportunity to answer all of those questions.
A number of questions are either repeated or asked with same concepts in mind. I have consolidated those into fewer number of questions and answered here. In other words answers written here are not 1:1 replies of your questions but essentially covers everything you wanted to know.
Q1: Is there a virtual firewall or special security protocol in Hyper-V?
A1: The answer is NO. Virtual machines can be protected using the same firewall applications and security protocols used in physical machines. To know more about virtual networks please click here
Q2: Do I need to run antivirus software in all the virtual machines in a Hyper-V based server or is it sufficient to run one instance of antivirus software in the parent partition?
A2: Antivirus software should be installed in all virtual machines including the parent partition. Also depending on the applications installed, the requirement on antivirus software would vary from one virtual machine to another virtual machine. For example, the antivirus software required for a virtual machine running Exchange Server is different from a virtual machine running SQL Server.
Q3: I have a smart client application. Will this work in a virtual machine environment (as such) or does it require customization?
A3: I don’t see any reason for additional customisations. But I do not know the details of the application you have mentioned. So I suggest you to thoroughly test the application before using it in production
Q4: Can my offline virtual machines be patched to keep it update?
A4: Yes, you can do this. Offline Virtual Machine Servicing Tool can be used to achieve this goal. Click here to download the tool. An update version of this tools is expected soon.
Q5: Please explain the ring model of CPU as far as Hyper-V is concerned.
A5: Hypervisors work at ring –1, OS kernel works at ring 0 and user applications work at ring 3. Ring 1 & 2 are not used in Windows
Q6: What are the specific CPU features required for Hyper-V to run?
A6: For any computer to run Hyper-V it should have a CPU from Intel or AMD with hardware assisted virtualization capability. For Intel processors this technology is called Intel-VT and for AMD processors this technology is known as AMD-V. Additionally Data Execution Prevention (DEP) should be turned on for Hyper-V to run.
Q7: Will the physical environment security applications take care of the full virtual environment or do I have to consider any additional products?
A7: Security applications such as firewalls and anti malware products remain the same for virtual environments. But these security applications should be configured to secure both parent and child virtual machines
Q8: Is System Management Server/System Center Configuration Manager a supported application on Hyper-V?
A8: Yes, SMS/SCCM products can be installed in a Hyper-V based virtual machine. Hyper-V based virtual machines can also be configured as SMS/SCCM clients.
Q9: Is there a “bare metal” installation type available for Hyper-V? Is it possible to install Hyper-V without installing Windows Server 2008?
A9: Yes and this type of Hyper-V implementation is known as Microsoft Hyper-V server. For more details please follow this link https://www.microsoft.com/Hyper-VServer
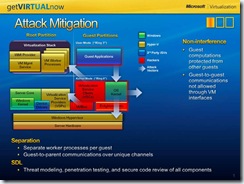
Q10: How the Hyper-v architecture can mitigate security attacks?
A10: Let’s look at different potential attack vendors on the virtualized environment.
Let’s say an application that encounters malware with some frequency (e.g. a web server) is running in one of the guest virtual machines above. It becomes compromised, but the malware would still need to compromise the guest kernel OS for the virtual machine (which is typically what happens when a physical machine is running an application with a vulnerability). From there the malware could potentially target a number of vectors for broader infection:
- The right arrow signifies that the malware could try to target other virtual machines running on the same box
- Alternatively, it could try to target the hypervisor to bring down the overall virtualization environment, or
- Try to target the VSPs through the VSC-VSP communications path. (Again, the virtualization service clients, or VSCs, enable virtual machines to be installed on their own Hyper-V device and to talk more directly with the virtual service providers which broker access to physical I/O.)
- Another option is to target the individual virtual machine worker processes where the majority of the code with Hyper-V resides
Let’s now look at how the Hyper-V architecture helps to mitigate these potential attack vectors
The hardware itself mitigates attacks on the OS kernel. The latest CPUs from Intel and AMD have the ability to run this in the most privileged part of the processor, otherwise known as “Ring 0”, and to block access to this from other components (e.g. guest virtual machines running in user mode) that should not have access.
The architecture itself creates isolation between other virtual machines, addressing the scenario of malware trying to attack other virtual machines from the infected virtual machine. If a guest wants to communicate with another guest, it must be done through the root partition. “Back-channeling” is not allowed – no two parts can communicate directly with each other, similar to how two machines connect on a physical network.
Regarding the other three attacks (on the Windows hypervisor, VSPs-VSCs, and on VM Worker processes):
- The size of the hypervisor, VSCs/VSPs are small (i.e. lower likelihood of vulnerabilities)
- When VSPs receive data from the VMBus, it is considered untrusted and requires validation
- If a VM Worker process (where most of the Hyper-V code resides) is brought down, it only brings down the VM session
In short, the separation of components from each other by privilege level and architecture helps enable defence-in-depth against malware attacks.
All of the above components have been extensively tested through the Security Design Lifecycle – threat modelling, fuzz testing, and security code review.
Q11: What is Microsoft Forefront and what kind of protection does it offer?
A11: Microsoft Forefront represents a suite of security products offering protection at client, server and network edge levels. Fore more details please refer to the following link www.microsoft.com/forefront
Q12: How many virtual machines can be created in a given instance of Hyper-V?
A12: Please follow this link to see the maximum supported configurations under Hyper-V. https://blogs.msdn.com/nickmac/archive/2008/07/04/hyper-v-rtm-maximum-supported-configurations.aspx . But these are not fixed numbers. They would change with newer hardware configurations and corresponding changes made to Hyper-V.
Another link: https://support.microsoft.com/kb/956710
Q13: Please explain the difference between monolithic hypervisor and microkernelized hypervisor.
A14: The diagram below explains the difference. Hyper-V follows the more secure and stable microkernelized architecture unlike many of it’s competitors.
Q14: What kind of hardware is recommended for Hyper-V?
A14: https://technet.microsoft.com/en-us/library/cc816844.aspx
Technorati Tags: Virtualization,Hyper-V,Security
Comments
- Anonymous
January 01, 2003
thank you