Not
Åtkomst till den här sidan kräver auktorisering. Du kan prova att logga in eller ändra kataloger.
Åtkomst till den här sidan kräver auktorisering. Du kan prova att ändra kataloger.
Flera vanliga autentiseringsscheman är inte säkra via vanlig HTTP. I synnerhet skickar grundläggande autentisering och formulärautentisering okrypterade autentiseringsuppgifter. För att vara säker måste dessa autentiseringsscheman använda SSL. Dessutom kan SSL-klientcertifikat användas för att autentisera klienter.
Aktivera SSL på servern
Så här konfigurerar du SSL i IIS 7 eller senare:
- Skapa eller hämta ett certifikat. För testning kan du skapa ett självsignerat certifikat.
- Lägg till en HTTPS-bindning.
Mer information finns i Konfigurera SSL på IIS 7.
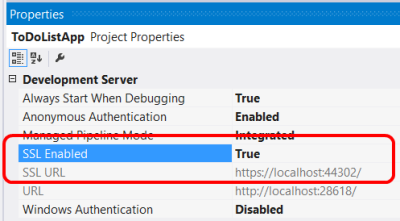
För lokal testning kan du aktivera SSL i IIS Express från Visual Studio. I fönstret Egenskaper anger du SSL-aktiverad till True. Observera värdet för SSL URL; använd den här URL:en för att testa HTTPS-anslutningar.
Framtvinga SSL i en webb-API-kontrollant
Om du har både en HTTPS-bindning och en HTTP-bindning kan klienter fortfarande använda HTTP för att komma åt webbplatsen. Du kan tillåta att vissa resurser är tillgängliga via HTTP, medan andra resurser kräver SSL. I så fall använder du ett åtgärdsfilter för att kräva SSL för de skyddade resurserna. Följande kod visar ett autentiseringsfilter för webb-API:et som söker efter SSL:
public class RequireHttpsAttribute : AuthorizationFilterAttribute
{
public override void OnAuthorization(HttpActionContext actionContext)
{
if (actionContext.Request.RequestUri.Scheme != Uri.UriSchemeHttps)
{
actionContext.Response = new HttpResponseMessage(System.Net.HttpStatusCode.Forbidden)
{
ReasonPhrase = "HTTPS Required"
};
}
else
{
base.OnAuthorization(actionContext);
}
}
}
Lägg till det här filtret i alla webb-API-åtgärder som kräver SSL:
public class ValuesController : ApiController
{
[RequireHttps]
public HttpResponseMessage Get() { ... }
}
SSL-klientcertifikat
SSL tillhandahåller autentisering med hjälp av certifikat för offentlig nyckelinfrastruktur. Servern måste ange ett certifikat som autentiserar servern till klienten. Det är mindre vanligt att klienten tillhandahåller ett certifikat till servern, men det här är ett alternativ för att autentisera klienter. Om du vill använda klientcertifikat med SSL behöver du ett sätt att distribuera signerade certifikat till dina användare. För många programtyper är detta inte en bra användarupplevelse, men i vissa miljöer (till exempel företag) kan det vara möjligt.
| Fördelar | Nackdelar |
|---|---|
| – Certifikatautentiseringsuppgifterna är starkare än användarnamn/lösenord. – SSL tillhandahåller en fullständig säker kanal med autentisering, meddelandeintegritet och meddelandekryptering. | – Du måste hämta och hantera PKI-certifikat. – Klientplattformen måste ha stöd för SSL-klientcertifikat. |
Om du vill konfigurera IIS för att acceptera klientcertifikat öppnar du IIS-hanteraren och utför följande steg:
Klicka på platsnoden i trädvyn.
Dubbelklicka på funktionen SSL-inställningar i mittenfönstret.
Under klientcertifikatväljer du något av följande alternativ:
- Acceptera: IIS accepterar ett certifikat från klienten, men kräver inget.
- Kräv: Kräv ett klientcertifikat. (Om du vill aktivera det här alternativet måste du också välja "Kräv SSL")
Du kan också ange följande alternativ i filen ApplicationHost.config:
<system.webServer>
<security>
<access sslFlags="Ssl, SslNegotiateCert" />
<!-- To require a client cert: -->
<!-- <access sslFlags="Ssl, SslRequireCert" /> -->
</security>
</system.webServer>
Flaggan SslNegotiateCert innebär att IIS accepterar ett certifikat från klienten, men kräver inget (motsvarar alternativet "Acceptera" i IIS-hanteraren). Om du vill kräva ett certifikat anger du flaggan SslRequireCert. För testning kan du också ange de här alternativen i IIS Express i den lokala applicationhosten. Konfigurationsfilen finns i "Documents\IISExpress\config".
Skapa ett klientcertifikat för testning
I testsyfte kan du använda MakeCert.exe för att skapa ett klientcertifikat. Skapa först en testrotsmyndighet:
makecert.exe -n "CN=Development CA" -r -sv TempCA.pvk TempCA.cer
Makecert uppmanar dig att ange ett lösenord för den privata nyckeln.
Lägg sedan till certifikatet i testserverns arkiv "Betrodda rotcertifikatutfärdare" enligt följande:
- Öppna MMC.
- Under Filväljer du Lägg till/ta bort snap-in.
- Under Tillgängliga snapin-modulerväljer du Certifikatoch klickar sedan på Lägg till.
- Välj datorkonto.
- Välj Lokal dator och slutför guiden.
- I navigeringsfönstret utökar du noden "Betrodda rotcertifikatutfärdare".
- På menyn Åtgärd pekar du på Alla uppgifteroch klickar sedan på Importera för att starta guiden Importera certifikat.
- Bläddra till certifikatfilen TempCA.cer.
- Klicka på Öppnaoch klicka sedan på Nästa och slutför guiden. (Du uppmanas att ange lösenordet igen.)
Skapa nu ett klientcertifikat som är signerat av det första certifikatet:
makecert.exe -pe -ss My -sr CurrentUser -a sha1 -sky exchange -n "CN=name"
-eku 1.3.6.1.5.5.7.3.2 -sk SignedByCA -ic TempCA.cer -iv TempCA.pvk
Använda klientcertifikat i webb-API
På serversidan kan du hämta klientcertifikatet genom att anropa GetClientCertificate i begärandemeddelandet. Metoden returnerar null om det inte finns något klientcertifikat. Annars återges en X509Certificate2-instans. Använd det här objektet för att hämta information från certifikatet, till exempel utfärdaren och ämnet. Sedan kan du använda den här informationen för autentisering och/eller auktorisering.
X509Certificate2 cert = Request.GetClientCertificate();
string issuer = cert.Issuer;
string subject = cert.Subject;