Använd ditt GitHub-konto för att logga in på Azure
Skapa en Microsoft Entra-app och tjänstens huvudnamn i portalen
- tilldela säkerhetsrollen till en app.
Kopiera prenumerations-ID:t.
| Fält | Description | Exempel |
|---|---|---|
| Organisation | contoso |
|
| Lagringsplats | GitHub-lagringsplatsnamn | contoso-app |
| Entitetstyp | Environment, Branch, Pull request, Tag |
|
| GitHub-namngivning | main |
|
| Name | contoso-deploy |
-
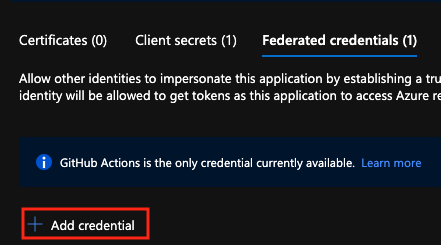
-
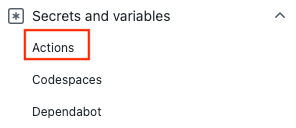
GitHub-hemligheter Azure Active Directory-programmet App-ID (klient-ID) Katalog-ID (klientorganisation) Prenumerations-ID:t
name: Run Azure Login with OpenID Connect
on: [push]
permissions:
id-token: write
contents: read
jobs:
build-and-deploy:
runs-on: ubuntu-latest
steps:
- name: 'Az CLI login'
uses: azure/login@v1
with:
client-id: ${{ secrets.AZURE_CLIENT_ID }}
tenant-id: ${{ secrets.AZURE_TENANT_ID }}
subscription-id: ${{ secrets.AZURE_SUBSCRIPTION_ID }}
- name: 'Run Azure CLI commands'
run: |
az account show
az group list
pwd
Du bör se meddelandet Login successful.
Skapa ett huvudnamn för tjänsten
-
Kommentar
az cloud update -n {environmentName} --endpoint-sql-management https://notsupported Skapa en Azure AD-app och tjänstens huvudnamn i portalen
az ad sp create-for-rbac --name "myApp" --role contributor \ --scopes /subscriptions/{subscription-id}/resourceGroups/{resource-group} \ --json-auth-
{ "clientId": "<GUID>", "clientSecret": "<GUID>", "subscriptionId": "<GUID>", "tenantId": "<GUID>", (...) }
Gå till GitHub-lagringsplatssidan.
I navigeringsmenyn går du till InställningarDetaljer.
-

Välj Add secret (Lägg till hemlighet).
on: [push]
name: AzureLoginSample
jobs:
build-and-deploy:
runs-on: ubuntu-latest
steps:
- name: Log in with Azure
uses: azure/login@v1
with:
creds: '${{ secrets.AZURE_CREDENTIALS }}'
on: [push]
name: AzureLoginSample
jobs:
build-and-deploy:
runs-on: ubuntu-latest
steps:
- name: Log in with Azure
uses: azure/login@v1
with:
creds: '${{ secrets.AZURE_CREDENTIALS }}'
enable-AzPSSession: true
- name: Azure PowerShell Action
uses: Azure/powershell@v1
with:
inlineScript: Get-AzResourceGroup -Name "< YOUR RESOURCE GROUP >"
azPSVersion: "latest"
on: [push]
name: AzureLoginSample
jobs:
build-and-deploy:
runs-on: ubuntu-latest
steps:
- name: Log in with Azure
uses: azure/login@v1
with:
creds: ${{ secrets.AZURE_CREDENTIALS }}
- name: Azure CLI script
uses: azure/CLI@v1
with:
azcliversion: 2.0.72
inlineScript: |
az account show
az storage -h
- name: Login to Azure US Gov Cloud with CLI
uses: azure/login@v1
with:
creds: ${{ secrets.AZURE_US_GOV_CREDENTIALS }}
environment: 'AzureUSGovernment'
enable-AzPSSession: false
- name: Login to Azure US Gov Cloud with Az Powershell
uses: azure/login@v1
with:
creds: ${{ secrets.AZURE_US_GOV_CREDENTIALS }}
environment: 'AzureUSGovernment'
enable-AzPSSession: true
Använda med andra Azure-tjänster
Microsoft Entra-ID
Power BI
Anslutningar
Azure Databricks
Distribuera till Azure från GitHub
Feedback
Kommer snart: Under hela 2024 kommer vi att fasa ut GitHub-problem som feedbackmekanism för innehåll och ersätta det med ett nytt feedbacksystem. Mer information finns i: https://aka.ms/ContentUserFeedback.
Skicka och visa feedback för