Anteckning
Åtkomst till den här sidan kräver auktorisering. Du kan prova att logga in eller ändra kataloger.
Åtkomst till den här sidan kräver auktorisering. Du kan prova att ändra kataloger.
Du kan använda det här avsnittet för att lära dig hur du distribuerar programtrafik över olika geografiskt distribuerade instanser av ett program med hjälp av DNS-principer som baseras på tid på dagen.
Det här scenariot är användbart i situationer där du vill dirigera trafik i en tidszon till alternativa programservrar, till exempel webbservrar som finns i Microsoft Azure, som finns i en annan tidszon. På så sätt kan du belastningsbelasta trafik mellan programinstanser under perioder med hög belastning när dina primära servrar överbelastas med trafik.
Anmärkning
Information om hur du använder DNS-principer för intelligenta DNS-svar utan att använda Azure finns i Använda DNS-princip för intelligenta DNS-svar baserat på tid på dagen.
Exempel på intelligenta DNS-svar baserat på tid på dagen med Azure Cloud App Server
Följande är ett exempel på hur du kan använda DNS-principen för att balansera programtrafik baserat på tid på dagen.
I det här exemplet används ett fiktivt företag, Contoso Gift Services, som tillhandahåller lösningar för onlinegåva över hela världen via sin webbplats, contosogiftservices.com.
Den contosogiftservices.com webbplatsen finns endast på ett enda lokalt datacenter i Seattle (med offentlig IP-adress 192.68.30.2).
DNS-servern finns också i det lokala datacentret.
Med en ny ökning i verksamheten har contosogiftservices.com ett högre antal besökare varje dag, och några av kunderna har rapporterat problem med tjänsttillgänglighet.
Contoso Gift Services utför en webbplatsanalys och upptäcker att trafiken till Seattle-webbservern ökar varje kväll mellan 18.00 och 21.00 lokal tid. Webbservern kan inte skalas för att hantera den ökade trafiken vid dessa tider med hög belastning, vilket resulterar i överbelastning för kunder.
För att säkerställa att contosogiftservices.com kunder får en dynamisk upplevelse från webbplatsen bestämmer Contoso Gift Services att de under dessa timmar kommer att hyra en virtuell dator (VM) på Microsoft Azure som värd för en kopia av webbservern.
Contoso Gift Services hämtar en offentlig IP-adress från Azure för den virtuella datorn (192.68.31.44) och utvecklar automatiseringen för att distribuera webbservern varje dag på Azure mellan 17:00 och 22:00, vilket möjliggör en entimmes beredskapsperiod.
Anmärkning
Mer information om virtuella Azure-datorer finns i dokumentationen om virtuella datorer
DNS-servrarna konfigureras med zonomfattningar och DNS-principer så att mellan 17:00 och 21:00 varje dag skickas 30% frågor till instansen av webbservern som körs i Azure.
Följande bild visar det här scenariot.
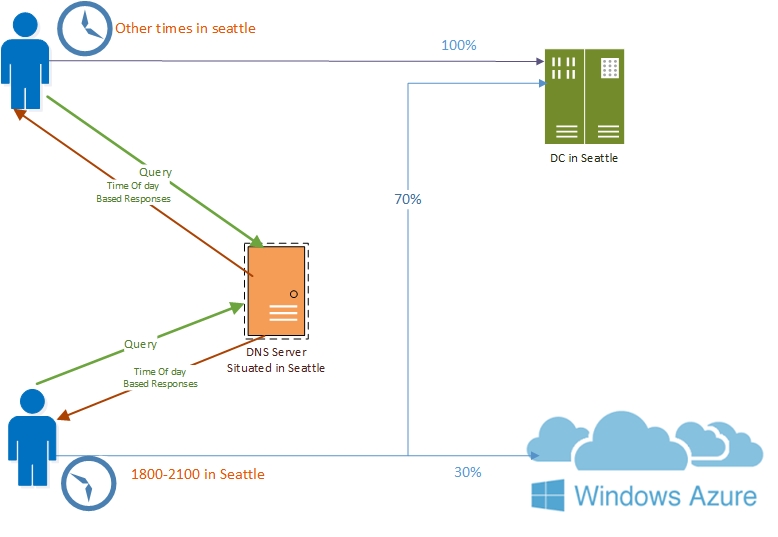
Så här fungerar intelligenta DNS-svar baserat på tid på dagen med Azure App Server
Den här artikeln visar hur du konfigurerar DNS-servern för att besvara DNS-frågor med två olika IP-adresser för programservern – en webbserver finns i Seattle och den andra finns i ett Azure-datacenter.
Efter konfigurationen av en ny DNS-princip som baseras på rusningstiderna 18:00 till 21:00 i Seattle skickar DNS-servern sjuttio procent av DNS-svaren till klienter som innehåller IP-adressen för Seattle-webbservern och trettio procent av DNS-svaren till klienter som innehåller IP-adressen för Azure-webbservern. dirigerar därmed klienttrafiken till den nya Azure-webbservern och förhindrar att Seattle-webbservern överbelastas.
Vid alla andra tider på dagen sker den normala frågebearbetningen och svar skickas från standardzonens omfång som innehåller en post för webbservern i det lokala datacentret.
TTL på 10 minuter i Azure-posten säkerställer att posten har raderats från LDNS-cachen innan den virtuella datorn tas bort från Azure. En av fördelarna med sådan skalning är att du kan behålla dina DNS-data lokalt och fortsätta skala ut till Azure efter behov.
Konfigurera DNS-princip för intelligenta DNS-svar baserat på tid på dagen med Azure App Server
Om du vill konfigurera DNS-princip för belastningsutjämningsbaserade frågesvar för tid på dagen måste du utföra följande steg.
Anmärkning
Du måste utföra de här stegen på DEN DNS-server som är auktoritativ för den zon som du vill konfigurera. Medlemskap i DnsAdmins, eller motsvarande, krävs för att utföra följande procedurer.
Följande avsnitt innehåller detaljerade konfigurationsinstruktioner.
Viktigt!
Följande avsnitt innehåller exempel på Windows PowerShell-kommandon som innehåller exempelvärden för många parametrar. Se till att du ersätter exempelvärden i dessa kommandon med värden som är lämpliga för distributionen innan du kör dessa kommandon.
Skapa zoners omfattning
Ett zonomfång är en unik instans av zonen. En DNS-zon kan ha flera zonomfattningar, där varje zonomfång innehåller en egen uppsättning DNS-poster. Samma post kan finnas i flera omfång, med antingen olika eller samma IP-adresser.
Anmärkning
Som standard finns det ett zonomfång i DNS-zonerna. Det här zonomfånget har samma namn som zonen, och äldre DNS-åtgärder fungerar i det här omfånget.
Du kan använda följande exempelkommando för att skapa ett zonomfång som värd för Azure-posterna.
Add-DnsServerZoneScope -ZoneName "contosogiftservices.com" -Name "AzureZoneScope"
Mer information finns i Add-DnsServerZoneScope
Lägg till poster i zonområdena
Nästa steg är att lägga till poster som representerar webbserverns värd i zonens områden.
I AzureZoneScope läggs posten www.contosogiftservices.com till med IP-adressen 192.68.31.44, som finns i det offentliga Azure-molnet.
På samma sätt läggs en post (www.contosogiftservices.com) till i standardzonsomfånget (contosogiftservices.com) med IP-adressen 192.68.30.2 för webbservern som körs i det lokala Seattle-datacentret.
I den andra cmdleten nedan ingår inte parametern –ZoneScope. Därför läggs posterna till i Standard ZoneScope.
Dessutom sparas TTL för posten för virtuella Azure-datorer på 600 sekunder (10 minuter) så att LDNS inte cachelagrar den under en längre tid och skulle störa belastningsutjämningen. Dessutom är de virtuella Azure-datorerna tillgängliga i 1 extra timme som en beredskap för att säkerställa att även kunder med cachelagrade poster kan lösa upp.
Add-DnsServerResourceRecord -ZoneName "contosogiftservices.com" -A -Name "www" -IPv4Address "192.68.31.44" -ZoneScope "AzureZoneScope" –TimeToLive 600
Add-DnsServerResourceRecord -ZoneName "contosogiftservices.com" -A -Name "www" -IPv4Address "192.68.30.2"
Mer information finns i Add-DnsServerResourceRecord.
Skapa DNS-principerna
När zonomfattningarna har skapats kan du skapa DNS-principer som distribuerar inkommande frågor över dessa omfång så att följande inträffar.
- Från 18:00 till 21:00 dagligen tar 30% klienter emot IP-adressen för webbservern i Azure-datacentret i DNS-svaret, medan 70% klienter får IP-adressen för den lokala Seattle-webbservern.
- Vid alla andra tillfällen får alla klienter IP-adressen för den lokala Seattle-webbservern.
Tiden på dagen måste uttryckas i lokal tid för DNS-servern.
Du kan använda följande exempelkommando för att skapa DNS-principen.
Add-DnsServerQueryResolutionPolicy -Name "Contoso6To9Policy" -Action ALLOW -ZoneScope "contosogiftservices.com,7;AzureZoneScope,3" –TimeOfDay “EQ,18:00-21:00” -ZoneName "contosogiftservices.com" –ProcessingOrder 1
Mer information finns i Add-DnsServerQueryResolutionPolicy.
Nu har DNS-servern konfigurerats med de DNS-principer som krävs för att omdirigera trafik till Azure-webbservern baserat på tid på dagen.
Observera uttrycket:
-ZoneScope "contosogiftservices.com,7;AzureZoneScope,3" –TimeOfDay “EQ,18:00-21:00”
Det här uttrycket konfigurerar DNS-servern med en kombination av ZoneScope och vikt som instruerar DNS-servern att skicka IP-adressen till Seattle-webbservern sjuttio procent av tiden, medan IP-adressen till Azure-webbservern skickas trettio procent av tiden.
Du kan skapa tusentals DNS-principer enligt dina trafikhanteringskrav och alla nya principer tillämpas dynamiskt – utan att starta om DNS-servern – på inkommande frågor.